It seems that with each major developer event covered by the media, a new device enters the work place. From the Apple Watch to wearables, tablets and smartphones, bring your own device (BYOD) is no longer something to try to plan for in the future, but something companies have to deal with right now. And for IT admins, it’s a completely new game as they struggle to adopt best practices quickly for protecting this new world of moving targets.
One of the biggest challenges of developing BYOD security policies is enabling users to reap the benefits of the devices without taking shortcuts on security. It’s a matter of keeping the experience flexible, private and fast, while securing corporate data, protecting against insider threats and complying with corporate governance initiatives.
The biggest mistake is treating mobile devices as an extension of your already existing traditional endpoint strategy. Security solutions designed for the desktop lack visibility to mobile traffic, are easily compromised by targeted mobile attacks and are certainly not able to secure against outsider threats.
 The bottom line is that organizations need to embrace a healthy mobile security policy that protects the organization and its sensitive IP while promoting productivity on mobile devices both inside and outside of the corporate network. We at Zimperium recently put together a white paper that examines the BYOD movement and provides a framework for enterprises who are struggling to adopt mobile security best practices. In it we took a look not only at the top risks BYOD brings to the enterprise today, but also what to consider when planning and designing for BYOD. We also break down the current mobile security solutions available today.
The bottom line is that organizations need to embrace a healthy mobile security policy that protects the organization and its sensitive IP while promoting productivity on mobile devices both inside and outside of the corporate network. We at Zimperium recently put together a white paper that examines the BYOD movement and provides a framework for enterprises who are struggling to adopt mobile security best practices. In it we took a look not only at the top risks BYOD brings to the enterprise today, but also what to consider when planning and designing for BYOD. We also break down the current mobile security solutions available today.
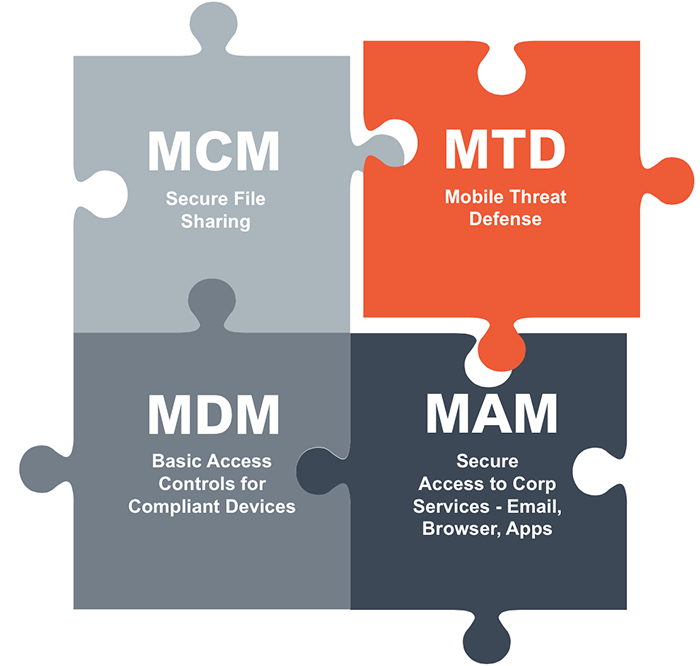
It’s important to note, however, that while some of the solutions mentioned in this whitepaper have valuable components for proper insider use and compliance purposes, they often fall short on preventing cyberattacks on mobile devices from the outside. Many solutions (Mobile Content Management/Mobile Device Management/Mobile App Management) have emerged to manage insider threats and provide secure access to corporate data; however they are missing a vital component that provides protection from cyberattacks. The best overall BYOD solution is one that combines the best in mobile threat defense technology with the best in enterprise mobility management technology so that you can secure and protect mobile devices from both insider and outsider threats, no matter where they are.
To read more about our breakdown of BYOD and security solutions, as well as our recommendations for mobile security best practices, you can download the whitepaper here: https://www.zimperium.com/download-whitepaper-BYOD-changes-the-game