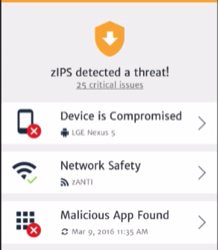
Several researchers have reported on the discovery of Hummer Trojan, as one calls it, or HummingBad as another calls it. Another said it was also known as Shedun. Zimperium’s customers are safe from this recently discussed threat even before these threats were published. The attack was detected through our z9 machine learning engine without requiring an update, similarly to other recently discovered Trojans such as the “S” trilogy dubbed Shuanet, Shifty Bug and Shedun, as well as Triada found in the trilogy of ad botnets including Leech, Ztorg and Gorpo. All of the Trojans utilizing exploits to gain elevated permissions (“rooting Trojans”) discovered in the last four years were detected by z9 without a need for an update.
Testing against the specific hash associated with Hummer Trojan:
SHA256 Hash: 3de64eafaddbc6a8974a019984a3c5b6103180091e3b396ca2e0f65dbd95b50f
zIPS detected the following attacks
- Malicious Apps
- Elevation of Privileges
- System Tampering
- Persistent Modifications
What Our Lab Testing Shows
What we found in our testing is that Hummer Trojan is similar to the Leech Trojan, demonstrated in our March 24, 2016 blogpost, Taking a Deeper Dive into Leech: One of the Three Families of Malware Dubbed as Triada. Hummer Trojan uses the same Youtube Downloader as Leech, including the UI and App icon. The only difference is that Hummer Trojan will push ads and multiple apps, both legitimate and malicious, onto the user’s device after rooting it.
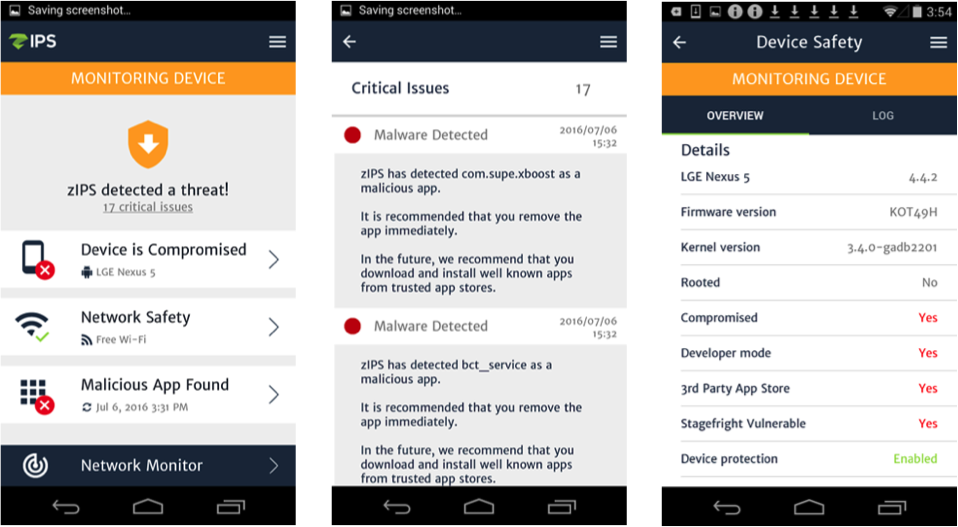
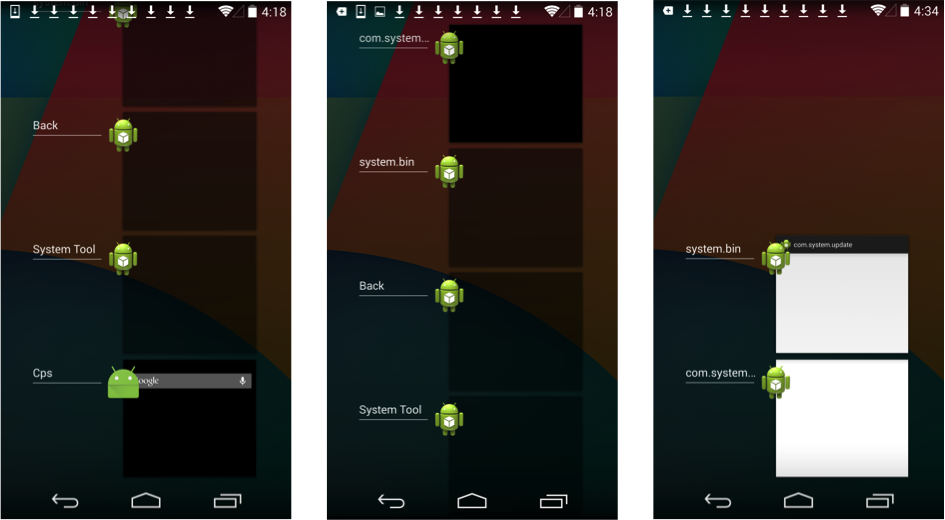
The screenshots below are collected after installing the Youtube Downloader malicious app.
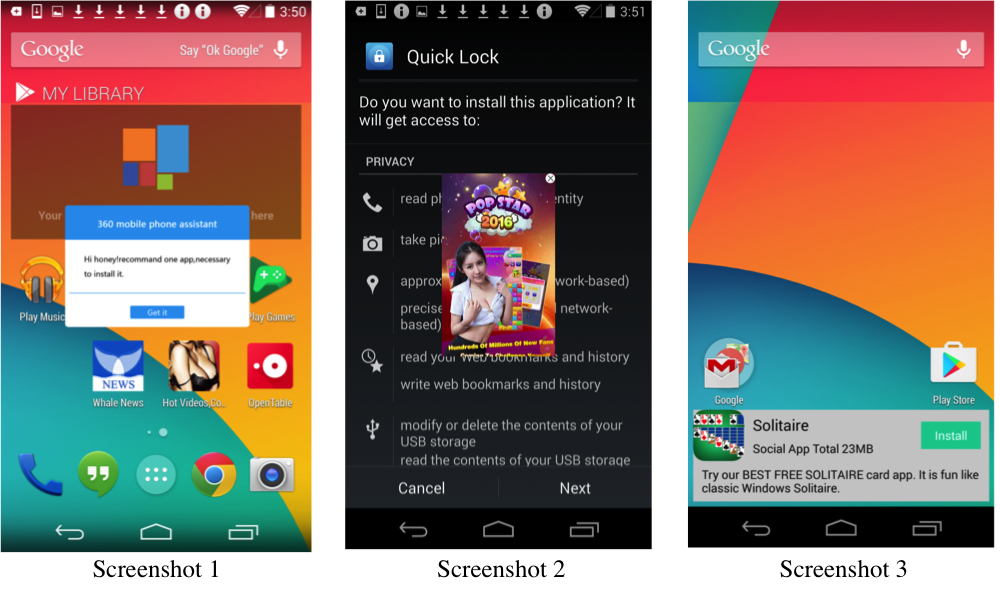
- Screenshot 1: Ad in the Center, 3 Apps installed (Whale News, Hot Videos, OpenTable)
- Screenshot 2: Ad in the Center, Quick Lock App waiting for install (pushed by the malicious app)
- Screenshot 3: Ads
Apps downloaded on the device storage by the malicious app are delineated in these screenshots
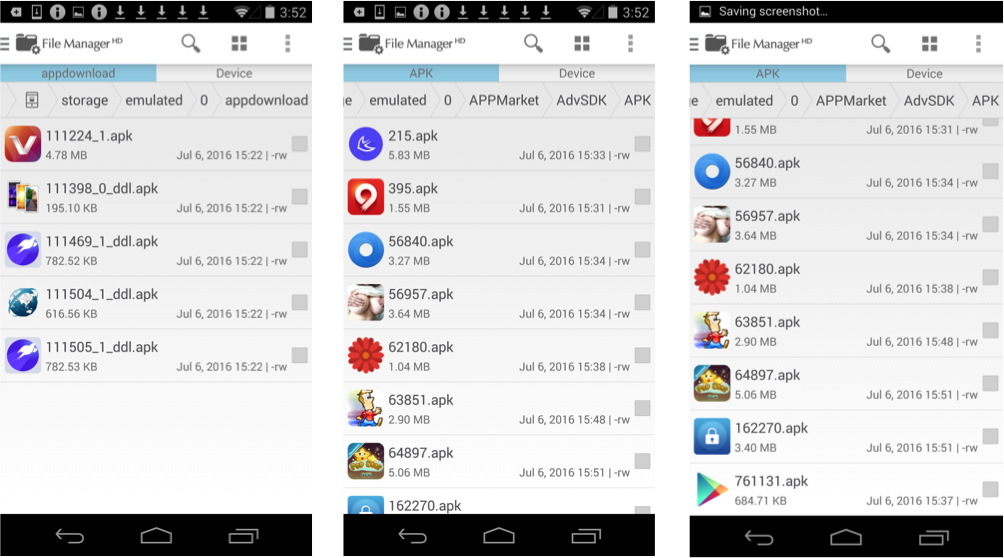
Other Suspicious Apps running in the background even after the device is rebooted are shown in these screenshots.
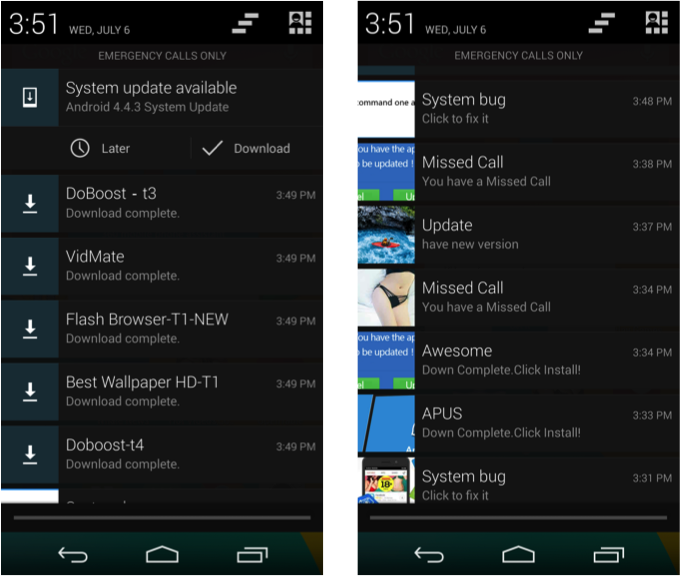
Apps downloaded notification looks like this.
A list of the Hummer Trojan indicators of compromise details including the foreign connections established by Hummer Trojan, list of the IPs, and domains the malicious app communicates with is available for download here.