Zuk Avraham, Founder
Follow Zuk Avraham (@ihackbanme)
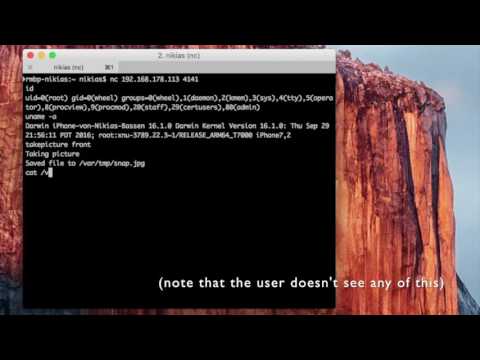
Last week, Ian Beer, from the Google Project Zero research team, released his local elevation of privileges exploit targeting iOS 10.1.1 [1]. We immediately understood that we had another opportunity to assess a new zero day exploit against our Machine-Learning attack and exploit detection engine – z9
z9 detected, once again, the newly released exploit that allows remote shell access as root, without requiring an update.
After catching our breath from all this excitement, we took the liberty to go over all the recent security events utilizing exploits to gain full control over the mobile device, or initial code execution remotely, and felt pretty proud of our track record:
| Exploit/Attack | Type | Z9 Detection Status |
| DIrtyCoW | Local | Successful DirtyCoW Attacks: z9 detected without requiring an update. Unsuccessful exploit attempts: We created new z9 simulation to provide an alert as well. |
| Ian Beer’s iOS 10.1.1 | Local | Successful DirtyCoW Attacks: Detected without an update |
| Gooligan | Local | Detected without an update – just a reuse of TowelRoot and VRoot in apps, mostly of third party marketstores – z9 doesn’t need to have app’s signatures to detect exploits. |
| Pegasus | Remote | Detected without an update |
| Stagefright | Remote | Using our previous trainings of z9 for CVE-2015-1538 and CVE-2015-3864 z9. Google Project Zero Stagefright exploit CVE-2016-3861: detected without an update. |
New Attack Classes:
Both Drammer and DressCode were not previously considered a valid class type for attacking the device. In security events, our partners and customers expect us to react as fast as possible. As a result, we developed custom simulations for both:
| Exploit/Attack | Type | Z9 Detection Status |
| Drammer | Local | z9 successfully trained to reliably detect Drammer’s templating technique |
| DressCode | Local to internal network | New anomaly detection for z9 to detect attempts to steal data via phone – successfully detects the attacks, regardless to the source of the attack. |
Drammer:
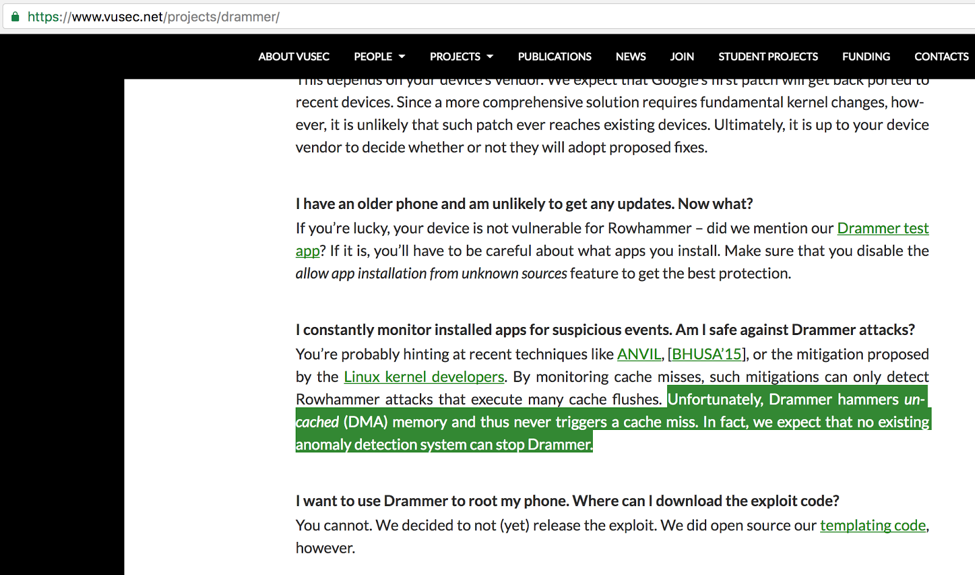
In the case of Drammer, it was even harder – the researchers who published the research on the exploit, only published their POC without the exploit. At first, we were concerned because the same researchers claimed that it is impossible to use behavioral methods to detect this[2], we were able to prove them wrong.
By only looking at the template code released, we were able to generate a generic z9 simulation that is able to detect Drammer accurately.
New and previously unknown threats are becoming more frequent, especially in targeted attacks and corporate espionage. Now when you evaluate a Mobile Threat Defense solution, ensure that it can alert you in case of real attacks, like the one described above.
If you wish to evaluate Zimperium’s Mobile Threat Defense solution and protect your organization, click here.