Our blog is sharing the five biggest mobile security threats your business needs to be aware of
All posts by Krishna Vishnubhotla

Posts by Krishna Vishnubhotla:
Top 5 Mobile Security Risks for Enterprises
Our blog is sharing the five biggest mobile security threats your business needs to be aware of
Debunking Five Myths About Mobile Security
Zimperium identifies and debunks the top five myths about mobile security and explained how to safeguard your enterprise with clarity and confidence.
Safeguarding Financial Data: Essential Cybersecurity Practices for Mobile Banking
Mobile app developers committed to upholding the highest security standards are faced with several considerations when developing and maintaining banking apps. Learn more.
Mobile Security Amongst Olympic Teams at the Paris 2024 Summer Olympics
Mobile devices have become indispensable for Olympic teams, providing critical data for training, performance tracking, and real-time analysis. However, with the increasing reliance on mobile technology comes the pressing need for robust mobile security measures to protect sensitive data and ensure uninterrupted performance.
The Critical Role of Supply Chain Resilience in Today’s Digital Landscape
Businesses must recognize that operational resilience extends beyond cybersecurity; it encompasses the entire supply chain, ensuring that even routine updates do not disrupt operations.
Every Industry’s Battle: The Threat of Mobile Malware on the Enterprise
Our research also shows that the 29 malware families we highlighted in the Heist report also target 478 non-banking mobile applications across 32 categories.
Securing Your React Native Apps: Top 6 Concerns to Address
In mobile app development, there are two primary approaches: native apps and hybrid apps. Native apps are developed for specific platforms using languages like Swift for iOS and Kotlin for Android, offering fast performance and a smooth user experience. Hybrid apps, on the other hand, are built with web technologies […]
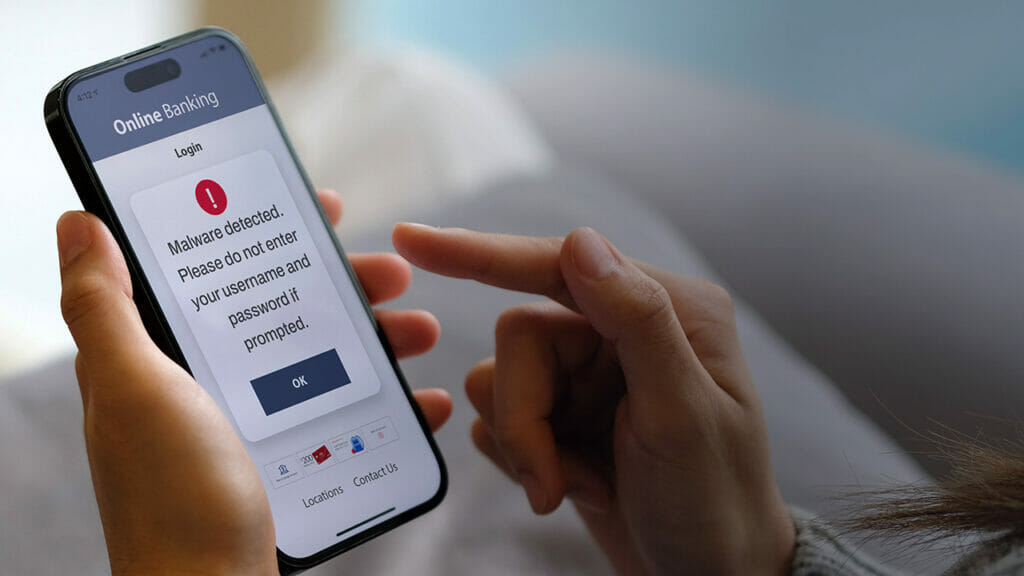
Mobile Banking Heists: The Emerging Threats and How to Respond
The past year has witnessed significant technological advancements in the banking and financial management which have greatly improved convenience for customers while also increasing security risks that should not be taken lightly. The financial industry has transformed mobile devices into a personal ATM for customers, offering services ranging from payments […]
Mobile Banking Malware and Regulation Stress the Need for Adaptive Security
The rise of mobile banking malware has led to stringent banking security regulations and the need for adaptive security techniques that resolve evolving threats.