According to the 2018 McKinsey Global Institute’s Smart Cities: Digital Solutions for a More Livable Future, more than half of the world’s population resides in cities, with another 2.5 billion new residents expected by 2050. Cities face increasing environmental pressures and infrastructure needs – and growing demands from residents to deliver a better quality of life and to do so at a sustainable cost.
Enter the smart city.
Smart cities put data and digital technology to work for its residents. The goal is to improve the quality of life by, in part, changing the nature and economics of existing infrastructure.
The cost of gathering information about usage patterns is reduced, and with an unprecedented volume of data points in-hand, city governments, employers, and residents can find new ways to optimize existing systems.
Smart cities encourage people to use transit during off-hours, change routes, use energy and water more efficiently, and reduce the strain on the healthcare system through preventive self-care. The result is not only a more livable city but also a more productive place for people and businesses to operate.
McKinsey notes, smart cities create a more efficient, responsive, and sustainable environment that delivers better outcomes for the people who call it home:
- 30 – 300 lives saved each year in a city of 5 million;
- 30 – 40 percent fewer crime incidents;
- 8 – 15 percent lower disease burden;
- 15 – 30 minutes shaved off the daily commute;
- 25 – 80 liters of water saved per person per day; and
- 20 – 35% faster emergency response times
And cities are responding. Los Angeles. Chicago. Boston. New York. Las Vegas. Houston. As of 2018, 11 of the top 50 Smart Cities in the world were U.S. cities. And the number of smart cities continues to grow.
Smart Cities Can Get Smarter
Two obvious and necessary elements in developing a successful smart city are connectivity, in the form of standardized Wi-Fi collaborating with the second element. Mobile devices.
Smart cities aside, mobile devices already hold tons of our own and our families’ personal and financial data as well as company information. Now, imagine the amount of data and information found in the phones and apps of smart city residents and businesses.
We protect our personal computers with antivirus, firewalls, VPNs, anti-spyware and every anti-X solution we can find. However, very few people do the same with their mobile devices. And only one smart city has taken the extra step in protecting its residents.
Hackers know this, making the mobile device the easiest attack vector to fully compromise an individual, organization or smart city.
The overwhelming majority of attacks – by our estimates, over 90% – start with the most used feature on a mobile device: the WiFi connections. Unfortunately, WiFi relies on mostly insecure protocols and standards, making them easy to impersonate or intercept, mislead and redirect traffic.
Most users of mobile devices are completely unaware their devices are being attacked because there are very few, if any, telltale signs their device has been compromised.
To make matters worse, every iOT device using the WiFi infrastructure in the smart city – traffic lights, sensors, public building doorbells, etc, – is susceptible to an attack.
Danger Zone – 600 Million Threats a Day
Every day, Zimperium detects six hundred million events. We process the most relevant events as network attacks and create what we call the Danger Zone – a real-time map, warning you from connecting to malicious private and public WiFi networks.
Danger Zones are found in Zimperium’s zIPS app, which provides comprehensive protection for iOS and Android devices against mobile network, device, phishing and application cyber attacks.
Let’s take a look at the Danger Zone for six of the leading smart cities we mentioned above (spoiler: one of those cities is protected with our technology). The timeframe we’ll use is one year. – March 13, 2018 – March 13, 2019.
For each city, we identified three types of events:
Low threat events are, for example, network scans. A network scan is a device inspecting IP addresses on the network to find active devices connected to it. It’s not a problem on its own, but it is a technique attackers use to find possible victims. There is no real compromise to the device itself, but it’s a sign you should probably disconnect from that network. Another low threat event could be a warning there is a danger zone network nearby. If a network in which we’ve detected attacks is in range of a zIPS protected device, the user will get a warning. This doesn’t mean the device was or is going to be attacked if it connects to that network, but the user knows it was used before to perform attacks.
An elevated threat is, for example, if you are indeed connected to a network we know presents attacks. This means the user ignored the first warning sign and moved further. Again, this doesn’t mean the device is compromised, but it was used in a potentially harmful situation.
A critical threat is when we know someone is compromising the data coming from the device. For example, someone is performing a man in the middle attack (MiTM) – a hacker is routing all your traffic to his/her own device, thus being able to steal information. This is irrefutable evidence an attack was performed against the device. zIPS detects MiTM attacks in about a second, which is not enough time for an attacker to get any useful information.
Each WiFi sign is a location in which we detected (and prevented) an attack over a WiFi network during that last year.
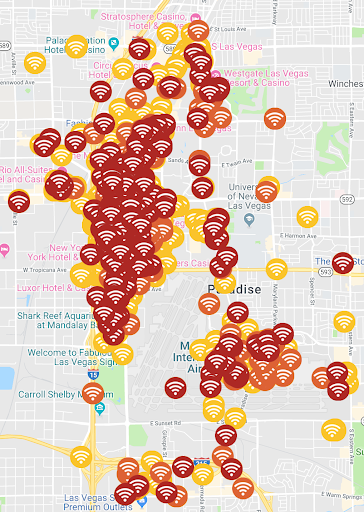
Las Vegas
Las Vegas has established what is called the “Innovation District” in the city’s urban core to concentrate its technology infrastructure investment. The Innovation District is the home of new transportation infrastructure and mobility technologies, allowing for the creation of partnerships with autonomous vehicle/mobility companies and with smart city technology firms.
The Innovation District and surrounding areas present WiFi network attacks with different severity. 5,422 low; 343 elevated; and 592 critical.
Boston
The City of Boston is using technology to re-imagine its streets. Smart streets, use cameras and sensors to learn more about how people navigate and interact on the streets in an effort to increase roadway safety.
In addition to street safety, Boston and its surrounding areas are seeing an abundance of WiFi network attacks. 10,582 low; 196 elevated; and 1,202 critical.
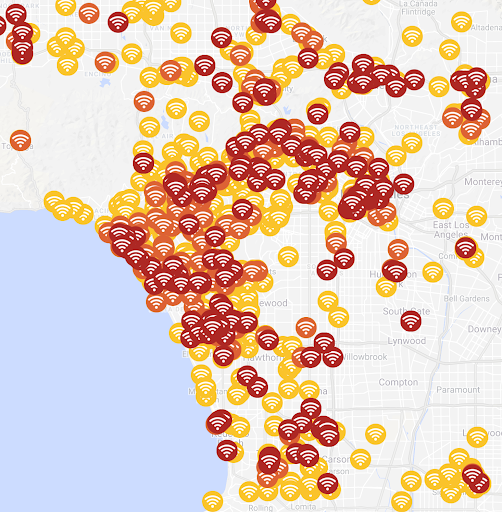
Los Angeles
Los Angeles is at the forefront of using technology and innovation to improve the community. Traffic, natural disaster preparedness, and public safety are priorities. Another priority should be protecting residents from hackers compromising mobile devices using WiFi attacks. 9,364 low; 640 elevated; and 750 critical.
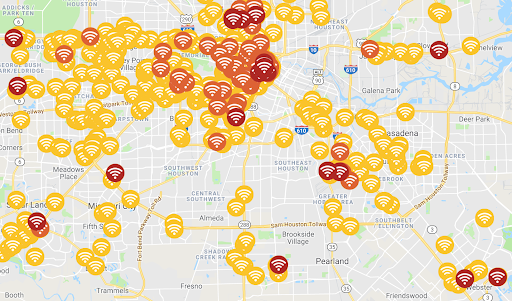
Houston
Houston’s recovery from Hurricane Harvey has been an opportunity to become a globally competitive “smart city” by putting more investments in cloud computing, public transportation and internet-connected environmental sensors. The transfer of data is also an opportunity for hackers to attack using WiFi networks. 1,536 low; 499 elevated; and 36 critical.
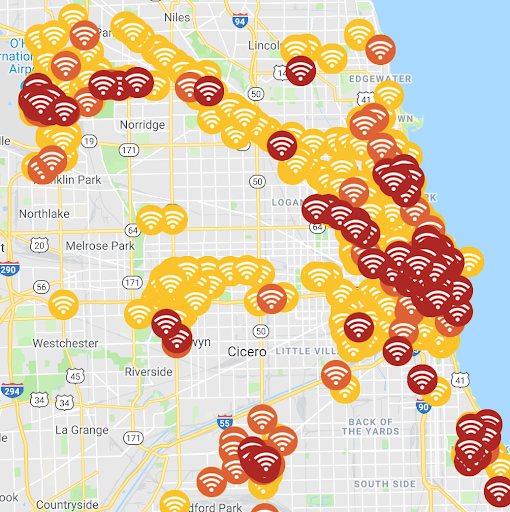
Chicago
As part of its “Array of Things” smart city initiative, Chicago has enabled its residents and businesses to be digitally-connected and engaged. Attacks using WiFi networks remain a risk. 3,873 low; 265 elevated; and 396 critical.
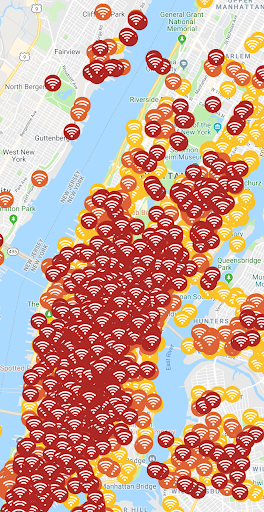
New York City
The city that never sleeps and has led the way as a smart city, also leads the way when it comes to WiFi attacks. 130,459 low; 6,699 elevated; and 4,528 critical.
NYC Secure
New York City is the only city to incorporate additional security measures to protect its residents. In July 2017, Mayor de Blasio established New York City Cyber Command, charged with protecting city-owned systems, which deliver critical services to New Yorkers, and helping New Yorkers become safer in their digital lives.
In August 2018, New York City Cyber Command launched NYC Secure, a free smartphone application platform that helps New Yorkers protect their phones against cyber threats by identifying and issuing warnings to users when suspicious activity is detected or they connect to an unsecure Wi-Fi network.
The Danger Zone threats above are taken from our enterprise customers in New York City using zIPS, the same technology NYC Secure uses. New York City and Zimperium do not collect or transmit any information from NYC Secure.
How to Stay Safe Using Public WiFi
There are private and public WiFi security solutions available. If adhered to, they will help ensure you are connecting to a legitimate WiFi. That said, they will not protect against a host of attack techniques. These attack techniques range from malware detection to anomalies in processes to phishing attacks to device compromises and malicious profiles. Your best best is working with the right mobile security solution. This ensures every person – and therefore the city – is properly protected.
That said, here are a few things users can do on their own to prevent these kinds of attacks:
- Configure devices to not connect automatically to known networks. This can be done easily on iOS, but on Android it has to be done for each network. A workaround is to delete known networks periodically.
- Don’t connect to open WiFi networks or networks using weak encryption protocols.
- Since users will likely ignore recommendation number two, avoid activities involving credentials (email, social media, bank, etc). This won’t prevent hackers from seeing traffic, but no credentials can be accessed by sniffing the traffic. That said, hackers are still able to perform other kinds of attacks. Attacks like directing the user to a malicious website. In this instance, the user can be tricked to install malicious apps, etc.
- Use a VPN which will encrypt traffic and show an attacker a nice set of nonsense characters.
zIPS – The World’s First Mobile Intrusion Prevention System App
The best way for a city to protect its residents is to incorporate Zimperium’s zIPS.
zIPS is the world’s first mobile intrusion prevention system app. It provides comprehensive protection for iOS and Android devices against mobile network, device and application cyber attacks.
In addition, zIPS can detect both known and unknown threats by analyzing the behavior of your mobile device, much like a doctor can diagnose an illness by analyzing the symptoms your body is exhibiting. By analyzing slight deviations to the mobile device’s operating system’s statistics, memory, CPU and other system parameters, our detection engine – z9 -accurately identifies, not only the specific type of malicious attack, but also the forensics associated with the who, what, where, when, and how of an attack occurrence.
Zimperium developed the innovative and award-winning z9 engine by training it over many years on proprietary machine-learning algorithms. The algorithms distinguish normal from malicious behavior on Android and iOS devices. The z9 engine sits directly on the mobile devices within the zIPS app. Doing so, maintains privacy and provides complete protection around the clock. Cloud-based mobile security solutions employs app sandboxing or tunneling traffic through the cloud.