Unmasking the SMS Stealer: Targeting Several Countries with Deceptive Apps
Researchers: Aazim Bill SE Yaswant, Rajat Goyal, Vishnu Pratapagiri, Gianluca Braga
Executive Summary
One-time passwords (OTPs) are designed to add an extra layer of security to online accounts, and most enterprises have become very dependent upon them for controlling access to sensitive data and applications. However, these passwords are just as valuable to attackers. Mobile malware has become increasingly sophisticated, employing cunning tactics to steal these crucial codes and bypass their added protection to enable malicious infiltration to corporate networks and data.
In this blog post, we will dive into a large-scale, Android-targeted SMS stealer campaign that our zLabs team discovered and has tracked since February 2022. Since then, zLabs researchers have identified over 107,000 malware samples. Throughout this period, zLabs researchers have witnessed firsthand how the attacker has evolved the malware to stay current and effective. This highlights both the longevity and sophistication of the malware and the attackers behind the campaign.
The Journey to Infection
Before we dive into the technical details of this sophisticated and dangerous malware campaign, let’s first take a journey into the deceptive lifecycle of how a user/device becomes a target.
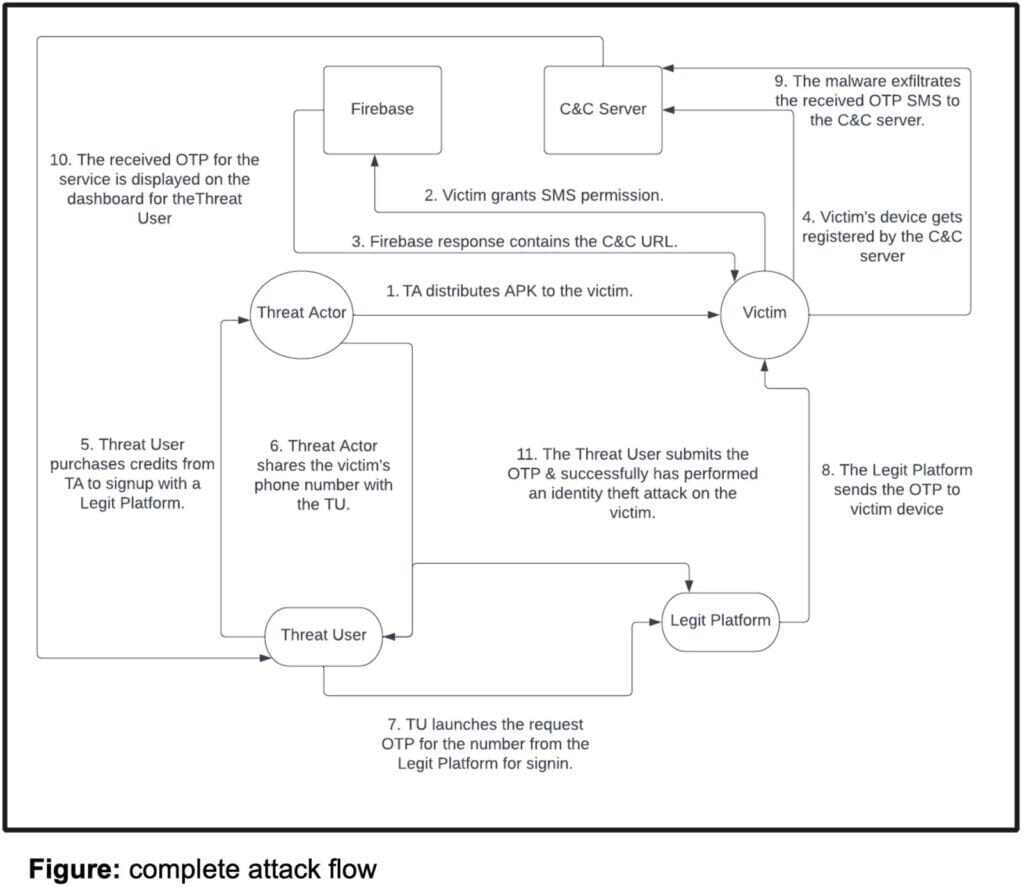
- Phase 1: App Installation – A Wolf in Sheep’s Clothing
- The victim is tricked into sideloading a malicious application either through a deceptive advertisement mimicking a legitimate app store or through the usage of automated Telegram bots communicating directly with the target (see below for more details).
- Phase 2: Permission Requests – Gaining Access
- Upon installation, the malicious application requests the SMS message read permission. This is a high-risk permission on Android that grants extensive access to sensitive personal data. While legitimate applications may require SMS permissions for specific, well-defined functions, this particular app’s request is intended to exfiltrate the victim’s private text message communications.
- Phase 3: Command & Control Server Retrieval – Finding its Puppet Master
- The malware then reaches out to its Command and Control (C&C) server. This server acts as the brain of the operations, executing commands and collecting stolen data. Initially, the malware relied on Firebase to retrieve the C&C server address. However, the attackers have adapted their tactics and they now utilize Github repositories or even embed the C&C server address directly within the app itself.
- Phase 4: C&C Communication – Checking In & Uploading Data
- With the C&C server address secured, the infected device establishes a connection. This communication serves a dual purpose; 1) The malware registers its presence with the server, confirming its operational status, and 2) Establishes a channel to transmit stolen SMS messages, including any valuable OTP codes.
- Phase 5: OTP Harvesting – The Silent Interceptor
- The final phase transforms the victim’s device into a silent interceptor. The malware remains hidden, constantly monitoring new incoming SMS messages. Its primary target is OTPs used for online account verification.
Deep Dive Analysis
Now that you have a better understanding of the infection phases, let’s take a closer look into some of the intricacies of this silent stealing malware campaign.
Distribution Channels: Master of Disguise
The actors behind this malware campaign employed deceptive tactics to compromise their victims. Malicious advertisements and bots were two of the common methods used to trick users into downloading and installing the malicious software. These deceptive tactics appeared legitimate, mimicking trusted sources to lure victims into clicking on malicious links or downloading applications that they later sideloaded onto their devices, a common tactic used to bypass security controls. By appearing trustworthy, victims were convinced to download and install the malware. Additionally, victims permitted the malicious application to read SMS messages, enabling the theft of sensitive data, including OTPs.
In addition to using malicious advertisement links to deceive users into installing malware, the threat actors also used Telegram bots to distribute the SMS stealing malware. These Telegram bots, posing as legitimate services, tricked victims into downloading unique malicious applications disguised as legitimate APKs.
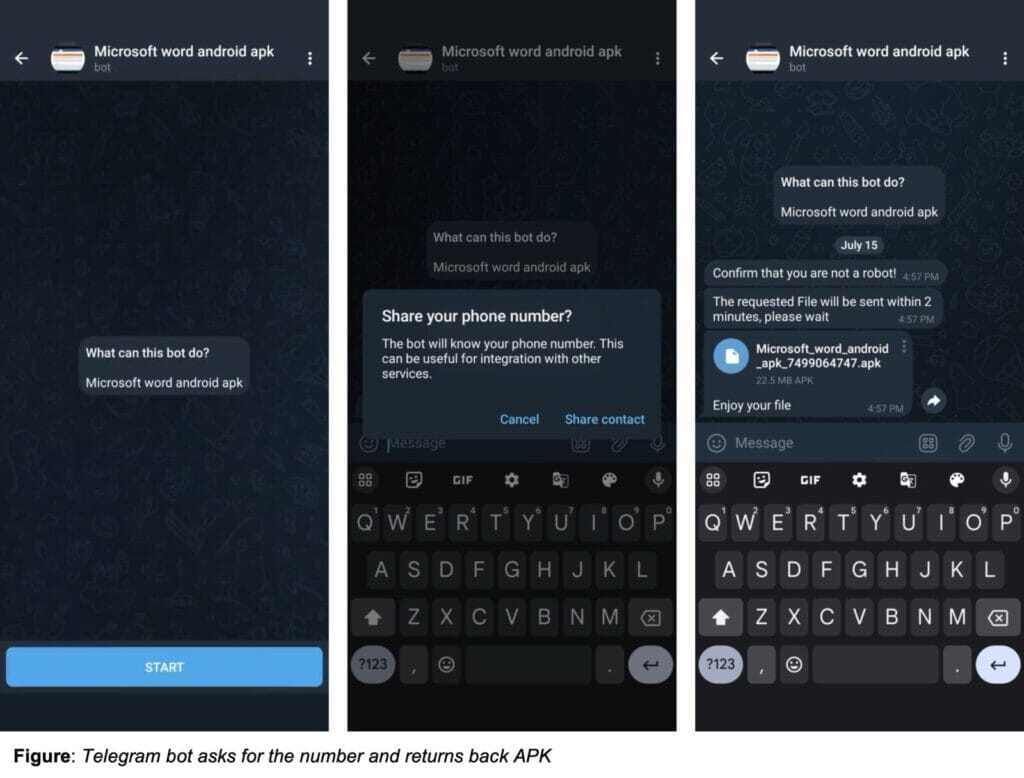
Devices were compromised not only by clicking on malicious web links hosting fake app store apps, but also infected by interacting with Telegram bots when searching for unofficial or free Android applications. For example, we witness a user initiating an interactive session with the bot from their mobile device. The bot then requested the user to share their phone number, which seems harmless but is actually a red flag. Once access is granted, the bot sends the user an APK (Android application package) cleverly modified to embed the user’s phone number within it This enables the attacker to target the victim further or personalize the attack. With the victim firmly in the grasp of the attacker, the attacker now has the ability to steal and sell sensitive information about the user for financial gain.
Command & Control
With the malware firmly in place on the victim’s device, we now turn our attention to how the malware is controlled by the threat actor. Our zLab researchers witnessed several evolving techniques to register and establish a C&C channel. In the early revisions of the malware, the threat actors leveraged Firebase to establish the C&C connections. But like with any well maintained and evolving malware campaign, our researchers witnessed alternative techniques to establish a C&C channel with the victims. We witnessed the use of Github repositories to share the C&C details, which contained one or more JSON (JavaScript Object Notation) files that included the URLs. We also witnessed the use of Github to distribute several of the malicious APK’s. Below is a snippet of one of the JSON files containing example C&C servers. 
From our research, most of the C&C servers seem to have implemented and are using the Laravel Framework.
Once the victim’s device has registered with its configured C&C server, the malware can now begin stealing the victim’s personal information, including but not limited to SMS messages and phone details. This information is then forwarded from the victim’s device to its configured C&C server, as demonstrated in the HTTP payload below.
The Scale of the Campaign
The scale of this malware campaign is staggering. Let’s take a look at some of the numbers our researchers uncovered to truly understand the scale of this campaign:
- Over 107,000 Unique Malware Applications: To date, our researchers have found over 107,000 malware samples directly tied to this campaign. This indicates a prolific campaign targeting a vast number of global victims.
- Over 95% of Malware Samples are Unknown or Unavailable: Of those 107,000 malware samples, over 99,000 of these applications are/were unknown and unavailable in generally available repositories.
- Over 60 Top-tier Global Brand Services Targeted: This malware was monitoring one-time password messages across over 600 global brands, with some brands having user counts in the hundreds of millions of users.
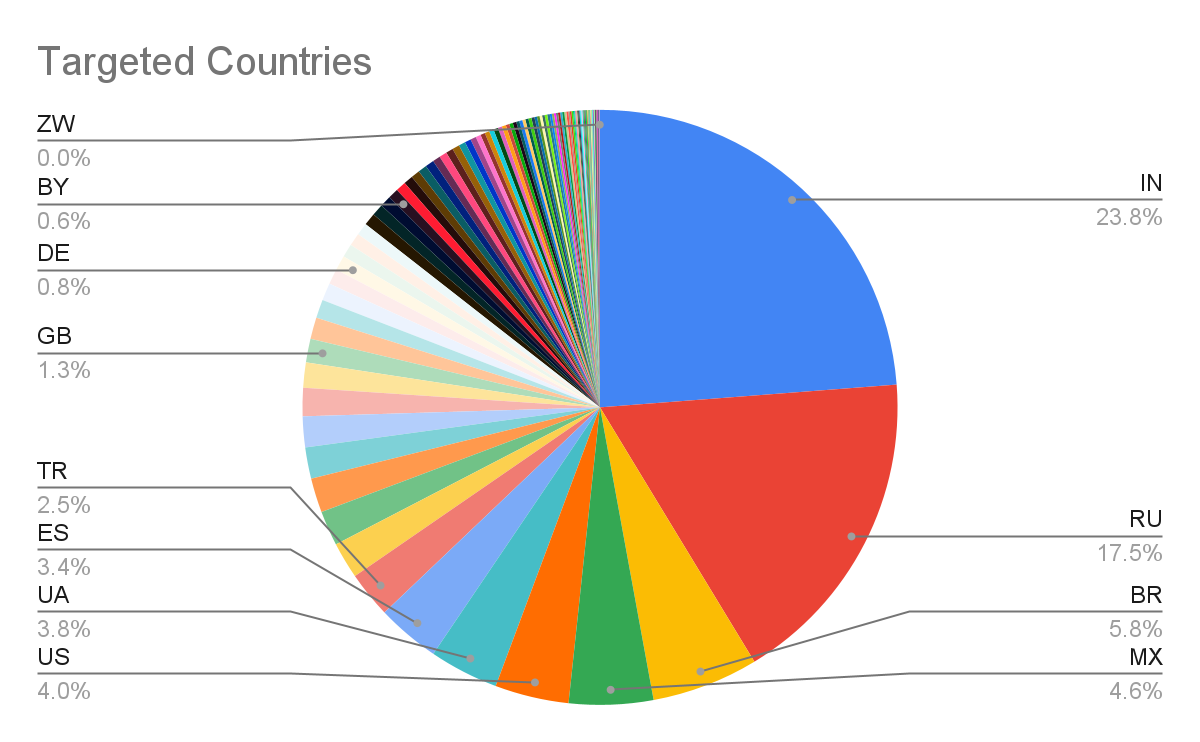
- 113 Countries : Victim’s spanned across 113 countries with Russia and India being the primary targets based on the volume of victim’s pulled from the samples. We also saw activity from several embargo countries as well.
- 13 Command and Control (C&C) Servers: Our researchers identified 13 C&C servers used by the malware to steal and leak SMS messages from victim devices.
- Extensive Telegram Bot Network: A vast network of roughly 2,600 Telegram bots was linked to this campaign, serving as a distribution channel for some of the malicious applications.
These numbers paint a concerning picture of a large-scale and sophisticated operation behind this malware campaign. The campaign’s ability to evade detection by many AV solutions emphasizes the need for a multi-layered approach to mobile security.
Unmasking the Threat Actors to Understand their Motive
While we cannot say for certain the exact motive behind this campaign, we do know that there was a financial component based on our research. We can see in the screenshot below that the platform accepts various payment methods, including cryptocurrency, a method that is commonly used by cybercriminals to conceal user identity.
During our investigation, our researchers uncovered a crucial link that highlights the financial motive behind this large-scale malware campaign. They discovered a connection between a website, fastsms.su, and one of the malware samples from this campaign. Further investigation revealed a well-developed C&C platform with a user-defined geographic selection model. This platform presented a range of service providers, both well-known consumer and enterprise services, with varying costs based on phone number availability within the chosen country. Upon selecting a service and making a payment, the threat actor received a designated phone number available to the selected and available service. The platform subsequently displays the OTP generated upon successful account setup.
Upon further investigation into this particular sample, we can see the malware transmitting the SMS messages from the infected device to a specific API endpoint on this domain. The malware actively searches for incoming messages originating from popular cloud services with the goal of intercepting one-time passwords (OTPs), likely used for two-factor authentication on these services or accounts linked to the stolen phone numbers.
Conclusion
The proliferation of this mobile malware, coupled with the ease of data theft (eg. SMS, OTP’s), poses a significant threat to individuals and organizations alike. With a vast array of malware samples discovered by our research team and the multiple infection vectors, you can see the threat landscape is complex and constantly evolving. On its own, stealing SMS messages may seem insignificant, but the ability of these malicious applications to steal sensitive information, including one-time passwords (OTPs), underscores the critical need for robust Enterprise mobile security solutions to protect from malicious sites and unknown malware, and provide enterprise visibility into those targeted.
These stolen credentials serve as a springboard for further fraudulent activities, such as creating fake accounts on popular services to launch phishing campaigns or social engineering attacks. Addressing this complex challenge requires a multi-layered approach, encompassing not only advanced detection technologies but also user education and awareness.
How can Zimperium help combat this campaign?
We witnessed several malicious and deceiving tactics and techniques to compromise the victim to steal sensitive information from the victims device. Everything from malicious websites, fake app stores hosting malicious applications and being sideloaded with elevated permissions, and data being leaked from the victims device to a well developed command and control platform with a broad set of services being monitored for things such as one-time passwords.
Sophisticated campaigns such as this SMS stealer campaign introduce a variety of unwanted security risks to enterprises and can be easily avoided if properly prepared with a comprehensive mobile threat defense (MTD) solution. Ignoring the risks is not an option. That is why it is important to take proactive measures to understand your risk exposure and to protect your device assets and the sensitive information associated with it.
Zimperium’s Mobile-first platform is perfectly designed to assist Enterprise’s (MTD) and App Developers (MAPS) to protect their PII and intellectual property from these evolving, polymorphic malware campaigns. Whether you have or are looking to protect Enterprise devices, or protecting your applications, Zimperium’s patented On-Device Dynamic Detection Engine, blends machine learning, behavioral analysis, and deterministic techniques to ensure comprehensive threat detection and mitigation with its unique capability of seamlessly and dynamically updating devices and applications with latest threat intelligence with zero user or development impact, eliminating disruptions to user experience or your development operations, commonly found with other mobile security solutions that may require frequent updates to combat these polymorphic campaigns. All customers who have deployed Zimperium’s MTD solution are protected from this dangerous and evolving malware campaign.
MITRE ATT&CK Techniques
To help our customers and the industry understand the impact of this malware, we’ve compiled the MITRE Tactics and Techniques for reference.
| Tactic | ID | Name | Description |
| Persistence | T1624.001 | Event Triggered Execution: Broadcast Receivers | It creates a broadcast receiver to receive SMS events. |
| Defense Evasion | T1406.002 | Obfuscated Files or Information: Software Packing | It is using obfuscation and packers to conceal its code. |
| Collection | T1517 | Access Notifications | It registers a receiver to monitor incoming SMS messages. |
| T1636.004 | Protected User Data: SMS Messages | It exfiltrates all the incoming OTP SMS messages. | |
| Command and Control | T1481.003 | Web Service: One-Way Communication | It sends all the exfiltrated info to a C&C server. |
| Exfiltration | T1646 | Exfiltration Over C2 Channel | It is using HTTPS protocol to exfiltrate data. |
Indicators of compromise (IOCs)
All IOCs relevant to this campaign can be found in this Github repository.