
written and researched by Nicolás Chiaraviglio and Santiago A. Rodriguez
As mentioned in our blog post on mobile phishing, there are different types of phishing attacks. Here, we’ll dig deeper into the different types that exist. Moreover, we’ll take a look at phishing kits, a tool that allows non-technical scammers to execute successful attacks.
All phishing attacks have the same purpose: deceive the victim in order to obtain personal information or install malware by impersonating some known entity. Nevertheless, there are different ways to achieve this purpose: deceptive, spear and clone phishing, smishing and domain spoofing. Let’s take a look at each of them.
Deceptive phishing
This is the most common type of phishing attack. It is usually delivered by an email impersonating a legitimate company, asking the user to click on a link which shows a website which is a copy of the legitimate one. Once there, the user is asked to create accounts, enter credentials or verify personal data.
This type of attack targets millions of people at the same time. For that reason, it’s also known as bulk or spray phishing.
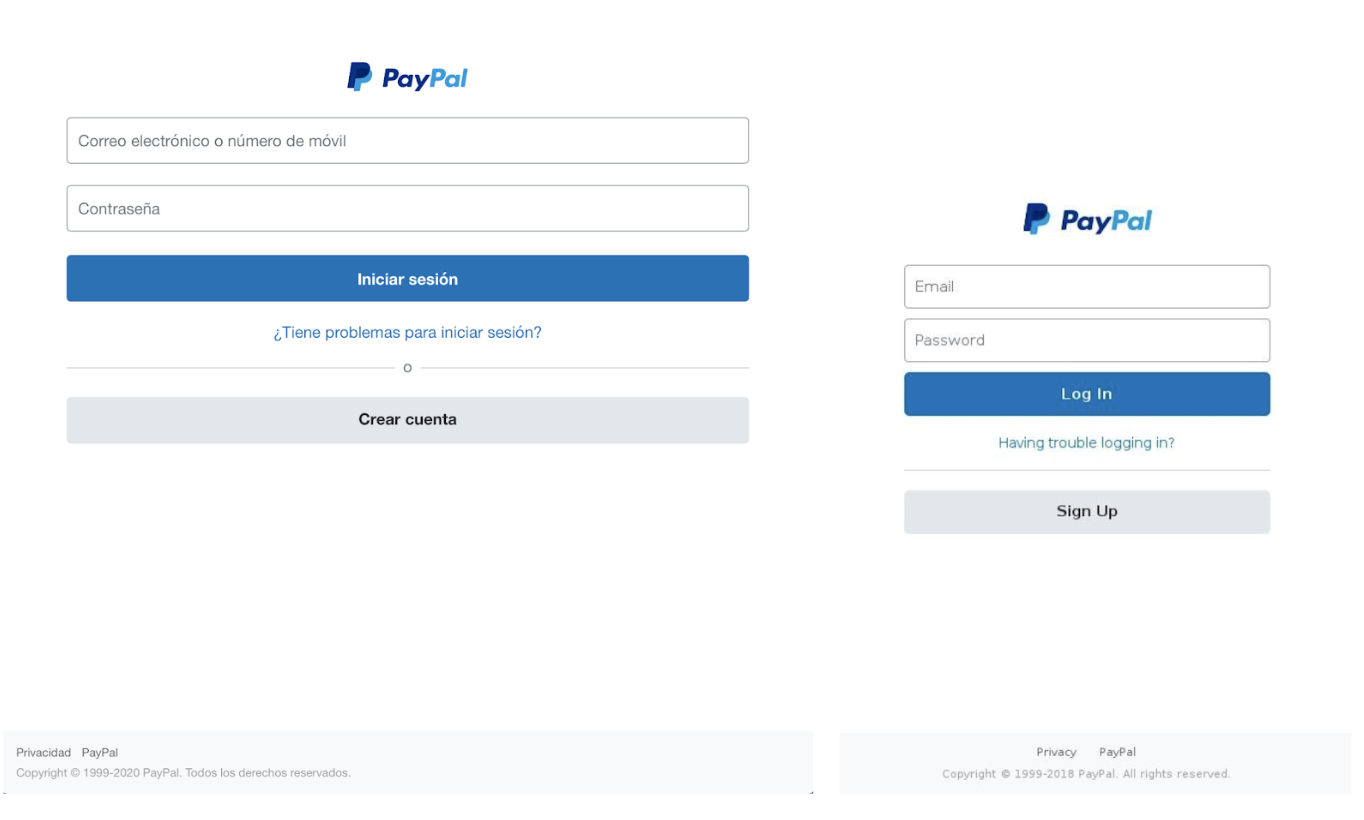
Two screenshots are shown below: one belongs to the real PayPal website and the other one to a deceptive phishing site. Can you spot which is the real one? Exactly.
Spear phishing (and whale phishing)
Spear phishing is a targeted phishing attempt against an individual or organization. This type of attack is usually delivered via email by a “known” sender and uses personal information (such as the name, company, position, social network accounts, etc.) in order to increase the probability of success. In order to create this type of phishing, the attacker needs to know some information about the organization or individual that is being targeted. For this reason, it is important to minimize the information we share online.
When this type of phishing attack is carried out against executives within an organization, this is known as whaling. Whaling is among the most risky types of attacks for any organization. Imagine what sensitive information an attacker can obtain by having the same access to company data as the company’s CEO.
Clone phishing
This type of attack reuses a legitimate email containing a link or an attachment that was previously delivered and creates a clone of that message but with malicious content (for example replacing the link pointed to by the URL, or the attachment with malware). In order to carry out this attack, the sender of the email has to be hacked in advance, adding an extra layer of difficulty.
A popular type of clone phishing attack consists of sending an email impersonating the CEO to a company employee, asking to do wire transfers or provide sensitive information.
Smishing
Smishing is more a delivery method than a separate type of attack. When an SMS is the delivery method of the bait, the phishing attack is called smishing. The importance of mentioning this type of delivery method is to emphasize that phishing attacks are not limited only to emails. As a matter of fact, mobile users are being warned against a new FedEx scam in the form of convincing SMS messages appearing to be from the delivery services company.
Domain spoofing/link manipulation
This type of phishing attack uses small variations of legitimate domains to trick the user into thinking it is the real domain. Some techniques used to conduct this attack are:
- Registering domains with spelling errors. For example gogle.com instead of google.com or instagrarm.com instead of instagram.com, linkedln.com instead of linkedin.com. You get the idea.
- Using subdomains. An attacker can register the domain important-information.com and then create a subdomain on it like: https://paypal.important-information.com which can be interpreted by the user as a legit PayPal URL.
- Use of non ASCII characters: ICANN allows the registration of domains using unicode characters. This opened a completely new game to link manipulation, letting the attacker register a completely new domain using lookalike characters. For example, can you spot the difference between www.google.com and www.ɡoogle.com? The difference is that the second domain is using the unicode character U+0261 (ɡ) instead of the regular U+0067 (g). Other examples of characters that can be used to replace the ones in the latin alphabet are: U+0430, U+0435, U+0440, U+0441, U+0443, and U+0456 (Cyrillic characters а, е, р, с, у, and і) with U+0061, U+0065, U+0070, U+0063, U+0079, and U+0069 (latin letters a, e, p, c, y, and i). This is also known as an IDN homograph attack.
Domain spoofing is usually chained with other types of phishing attacks, depending on the delivery method used. On mobile devices, this type of phishing attack is harder to detect since most mobile browsers are not showing the full URL but a short version of it.
Phishing kits
Putting together a phishing attack is more complicated than just sending an email/SMS with a URL in it. That URL needs to exist and produce a website that is able to trick even the most experienced user. This requires technical skills that exceed those of the common scammer.
However, this lack of skills can be “fixed” by buying the correct script kiddie tool. Such a tool is known as a phishing kit, which provides all that’s necessary to clone a legit website and send the information (after the attack is successful) back to the attacker. These kits can also contain software to send a large number of emails (and also an email database).
Phishing kits can be bought on the deep web or even be found on other phishing sites for free. Most of the time, the scammer is also scammed, since the creator of the kit is, at the same time, sending all the collected information to itself. This can be done since most kit user’s don’t have the required skills to assess what the kit is doing. It’s common to find the kit’s creator email address poorly obfuscated as part of the rendered site source code.
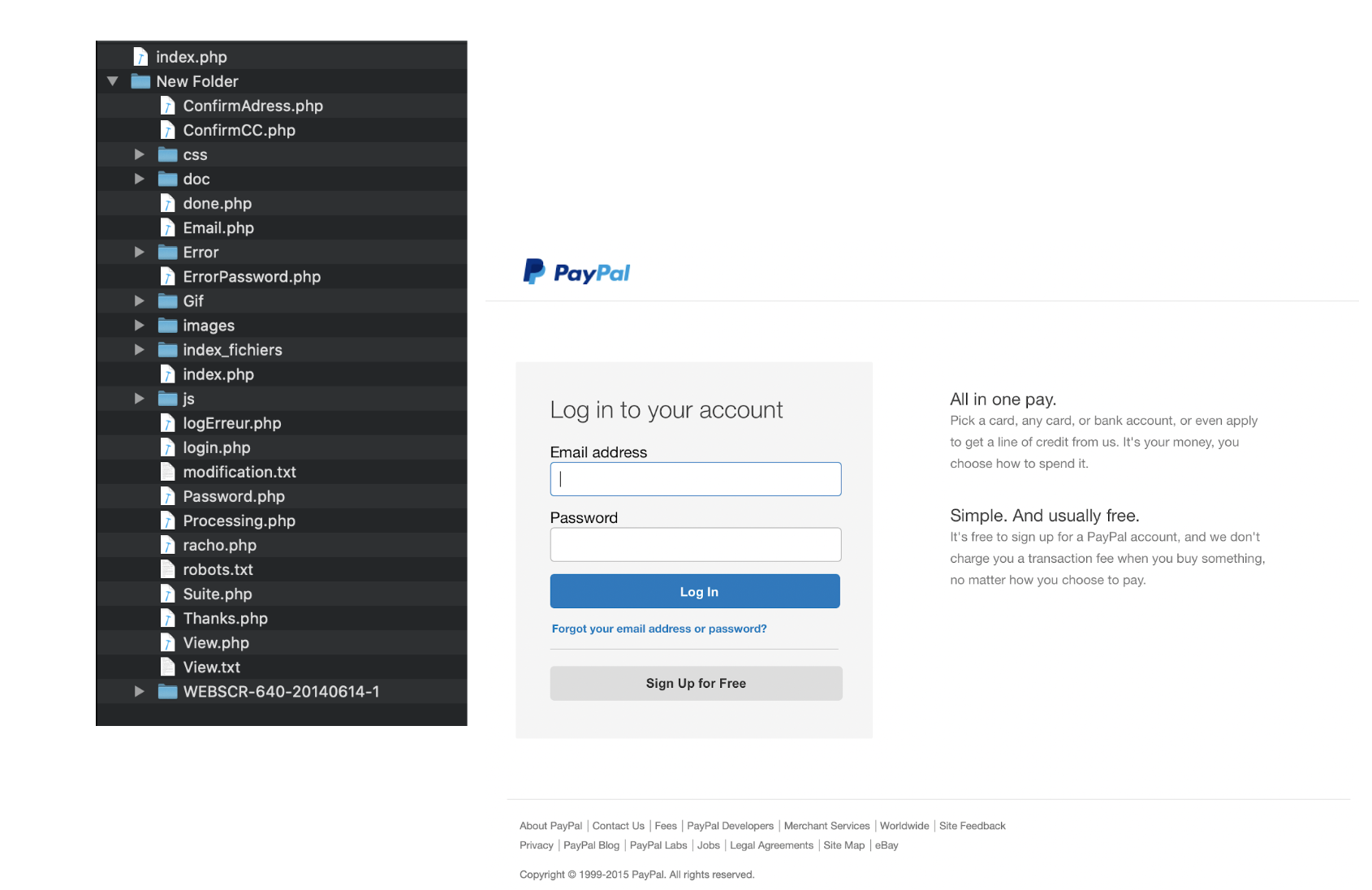
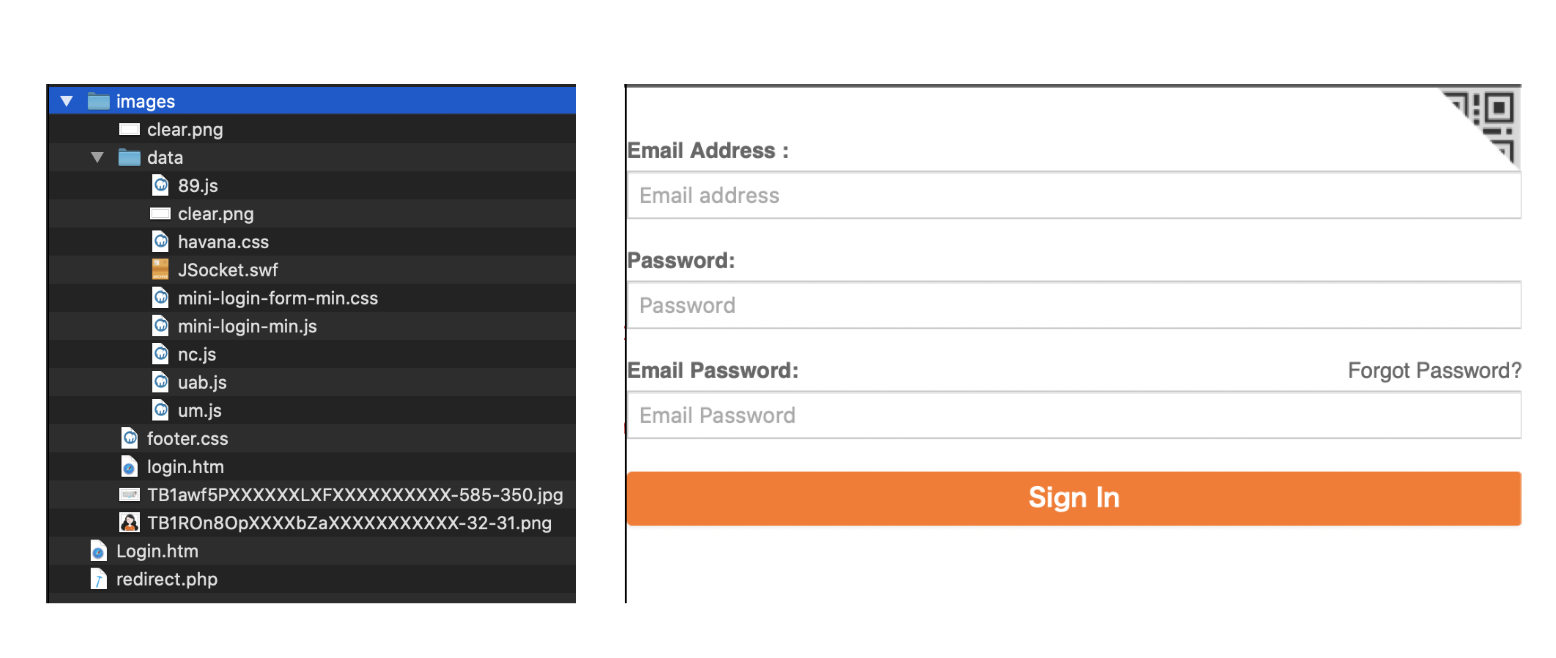
Phishing kits are important because they allow the non-technical scammer to access a massive amount of potential victims. As an example, the websites shown below, were generated using the phishing kits shown in the left. As you can see, some of them create an exact replica of the original website (like the PayPal and Yahoo ones), and some others are not good imitations.

Contact us
If you’d like to learn how to secure your mobile devices from phishing attacks, please contact us. We are here to help.


