Take Heed: Latest Research Shows Mobile Banking Apps are Not Created Equal
 As banks encourage us to move our money to mobile banking apps and cashless formats for convenience and speed, so does the threat of cybercrime. Today, cybercriminals target 63 percent of the banks in our study using specific malware campaigns to trick mobile users into surrendering their money and banking credentials.
As banks encourage us to move our money to mobile banking apps and cashless formats for convenience and speed, so does the threat of cybercrime. Today, cybercriminals target 63 percent of the banks in our study using specific malware campaigns to trick mobile users into surrendering their money and banking credentials.
Financial regulators like the US Federal Reserve acknowledge mobile device risks as well. As our banking practices migrate to mobile and cloud, so do the concerns about security and access our devices have. Regulators warn that mobile banking may help to address some challenges consumers face, but the mobile banking channel needs to become more trustworthy.
“A well-designed and secure mobile platform, as well as consumer access to and facility with mobile technology and the Internet, are likely needed in order for mobile banking to be a reliable banking channel.” US Federal Reserve
Are Banks Doing Enough?
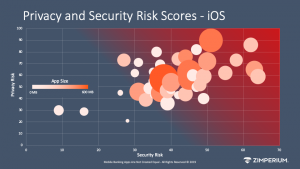 Mobile Banking Apps are not Created Equal discloses the security and privacy risks exposure and whether or not each passes or fails the Open Web Application Security Project (OWASP) Mobile Top 10. This research details how both iOS and Android banking applications from the top 45 US banks and mobile payment providers fared for security and privacy risk. This research scanned and scored 90 mobile banking apps available in the Apple App Store and Google Play in April 2019 for security, privacy, and data leakage risks. The results and scores are calculated using Zimperium’s z3A Advanced Application Analysis engine. Zimperium z3A is an application reputation scanning service that continually evaluates risks posed by mobile apps. z3A provides deep intelligence about app behavior, including content (the app code itself), intent (the app’s behavior), and context (the domains, certificates, shared code, network communications, and other data). z3A also provides privacy and security ratings, enabling enterprises to create security policies to limit or remove risky apps from managed devices.
Mobile Banking Apps are not Created Equal discloses the security and privacy risks exposure and whether or not each passes or fails the Open Web Application Security Project (OWASP) Mobile Top 10. This research details how both iOS and Android banking applications from the top 45 US banks and mobile payment providers fared for security and privacy risk. This research scanned and scored 90 mobile banking apps available in the Apple App Store and Google Play in April 2019 for security, privacy, and data leakage risks. The results and scores are calculated using Zimperium’s z3A Advanced Application Analysis engine. Zimperium z3A is an application reputation scanning service that continually evaluates risks posed by mobile apps. z3A provides deep intelligence about app behavior, including content (the app code itself), intent (the app’s behavior), and context (the domains, certificates, shared code, network communications, and other data). z3A also provides privacy and security ratings, enabling enterprises to create security policies to limit or remove risky apps from managed devices.
The security summary focuses on application risks. These risks include functionality and code use, application capabilities, and critical vulnerabilities.
The privacy information focuses on the application’s access to private user data, unique device identifiers, SMS, communications, and unsecure data storage.
Some of the quick facts to follow in this research include:
- Despite banks increasingly encouraging customers to use mobile banking apps and acknowledging cybersecurity as the biggest threat to the financial system, banks fail to adhere to coding best practices. Not adhering to application development best practices exposes both customer and bank data and increases the chances for fraud as banks implement more third-party mobile and cloud services.
- Banks continue to use shared code in production apps that is infrequently updated or retired. If shared code is no longer supported or is vulnerable, all apps containing this code are impacted after an incident occurs. Furthermore shared code means that anyone (especially open source code) has the opportunity to review and probe the code for vulnerabilities and weaknesses to identify the attack surface and exploit it.
- Banks continue to share sensitive customer data with advertisers. This practice increases the chances of data leakage if a mobile banking app is reverse engineered or a third-party library or service vulnerability is exploited. If there is a data breach, and personally identifiable information is exposed, banks suffer severe brand damage and regulatory fines.
- Most banks fail to obfuscate code, secure mobile device data, or implement runtime application self-protection for mobile apps. Failing to obfuscate code allows anyone to reverse engineer an app to identify weaknesses and identify an attack surface. One such example is how cybercriminals reverse-engineered a mobile app to identify vulnerabilities and stole millions of dollars overnight from thousands of users all without being detected.
To download a complete copy of the report, please click here.


