Best of Both Worlds: Integrating Zimperium Mobile Threat Data into Microsoft Sentinel Cloud-Native SIEM

While leading organizations are actively protecting mobile endpoints, security teams haven’t had clean and scalable ways to integrate and correlate threat data with other parts of the security infrastructure. But that is changing.
I recently hosted a webinar with David Branscome, Senior Cloud Solutions Architect, Microsoft and our very own Kern Smith, Vice President of Solution Engineering, discussing how – as the first and only mobile threat defense (MTD) solution integrated with Azure Sentinel – security analysts are now able to include Zimperium mobile threat data in their advanced threat hunting and threat correlation analysis.
To watch our on-demand webinar, please click here.
According to David, the SecOps mission of protecting organizations’ information and assets is becoming increasingly difficult. Attack techniques, frequency, and complexity are evolving fast. Security teams are under strain from the expanding breadth of defensive technologies, accelerating hybrid cloud adoption, and borderless, zero-trust networks. The shortage of SecOps talent makes this problem worse.
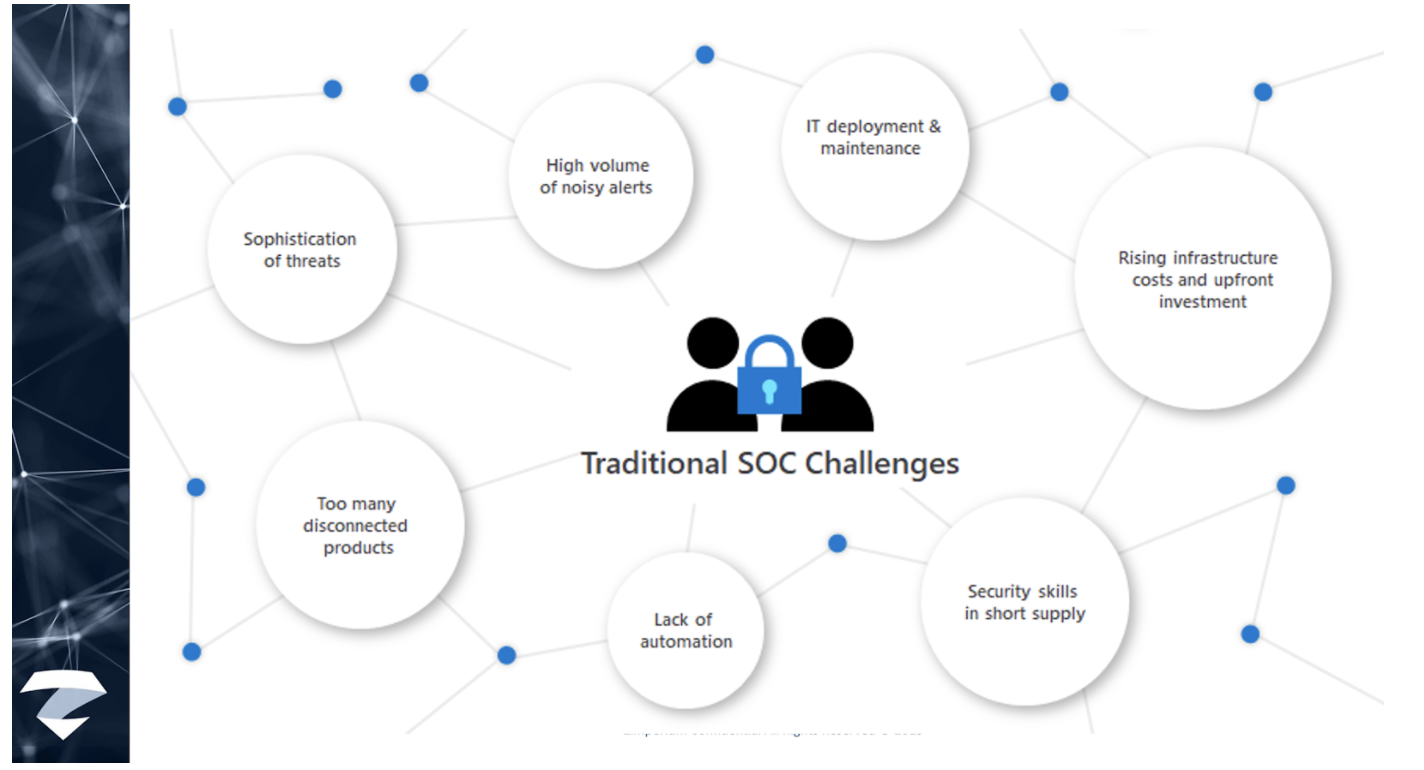
Considering the future needs of SOCs, these are the most prominent pain points:
Threats continue to grow in complexity and volume
Attacks are increasingly heterogeneous. A typical attack spans different parts of the enterprise and crosses various resource types: it might start from an IoT device, proceed to an endpoint, spread to a cloud service or to a database, involve multiple user accounts or tenants, and so on.
Alert fatigue: SOCs see too many alerts from disconnected products
Enterprise SOCs typically have dozens of security products, each producing a large volume of alerts. In isolation, these products often have high false positive rates and poor response prioritization, resulting in deafening alert noise. Attacks fall through the cracks despite generating alerts. Unfortunately, legacy SIEMs are functioning only as aggregators and don’t increase response capabilities. Enterprise SOCs need a way to integrate their security products to reduce the noise, prioritize alerts, and enable investigation and hunting across the entire dataset.
There is a global shortage of security analysts and experience
The need for skilled security professionals has greatly increased, and supply cannot meet current or future demand. A recent report by CSO magazine showed that this global talent shortage will increase to 3.5 million unfilled security jobs by 2021.
Investigation is complex and time-consuming
Every second counts when SecOps personnel are handling a threat that might jeopardize their organization. The clock is ticking fast, but investigation requires highly skilled security analysts and can often take days or weeks.
Legacy solutions are not architected for today’s demands, or tomorrow’s
Many legacy on-premises SIEMs require powerful hardware and extensive maintenance that make them expensive to operate. Storage and compute needs increase dramatically during an incident, which is difficult for an on-prem footprint to accommodate. The move to the cloud has enabled a new degree of enterprise scale-out, and with the explosion of cloud-born data, legacy SIEMs are less and less able to cope with the demand.
The cloud can help manage that complexity of the expanding digital estate. It simplifies and makes security easy to manage. Harnessing the power of cloud will set your SecOps teams free of IT work and help them focus on security work with no limits.
Next generation of AI and automation in the cloud helps to super-charge your work. It will leverage the large-scale intelligence available in the cloud and make it work for you.
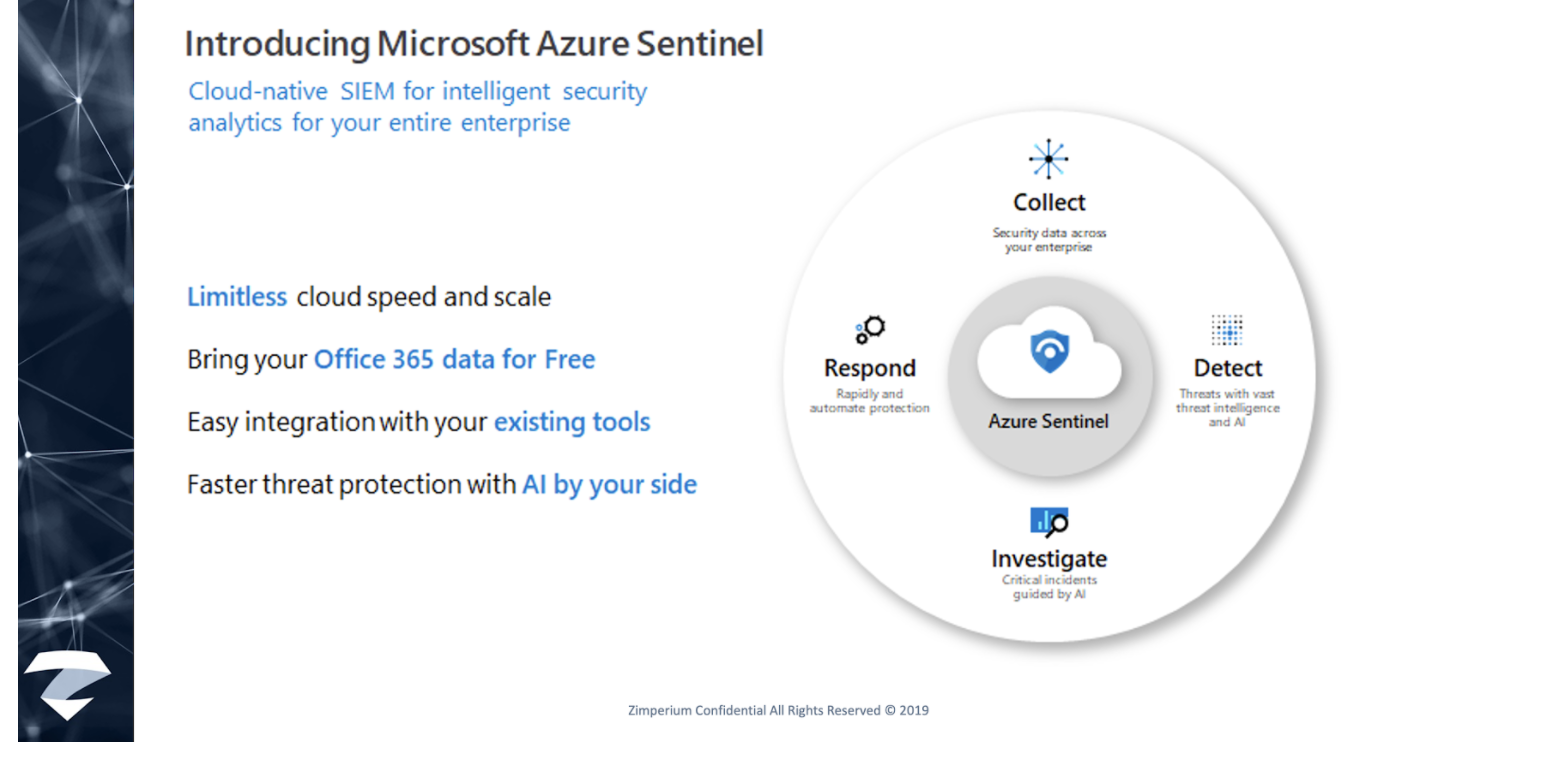
David explained that’s why the SIEM + SOAR tool was reimagined to introduce a new cloud-native solution called Microsoft Azure Sentinel – providing intelligent security analytics at cloud scale for your entire enterprise.
David went on to explain that Azure Sentinel makes it easy to collect security data across your entire hybrid organization from devices, users, apps, servers and any cloud, it uses the power of AI to ensure you are identifying real threats quickly, and unleashes you from the burden of traditional SIEMs by eliminating the need to spend time on setting up, maintaining and scaling infrastructure.
Since it is built on Azure, it offers limitless cloud scale and speed, scaling automatically to address your needs.
Traditional SIEMs have also proven to be expensive to own and operate, often requiring you to commit upfront and incur high cost for infrastructure maintenance and data ingestion. With Azure Sentinel there’s no upfront costs, you only pay for what you use, and Microsoft offers free Office 365 activity data import to help you reduce security costs significantly.
Patented detection engine designed for mobile
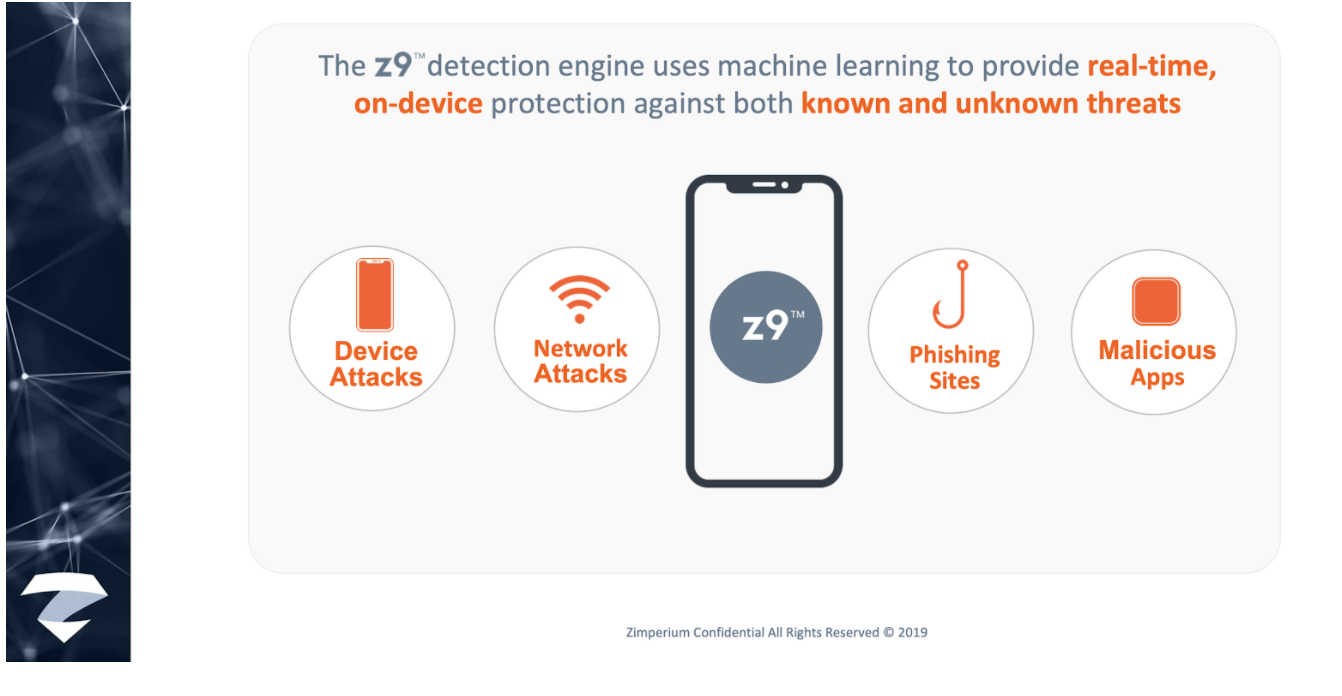
One of the endpoints needing to be protected are mobile devices. Zimperium offers the only real-time, on-device, machine learning-based protection against Android and iOS threats, including the detection of device, network, phishing and malicious app attacks. When we detect suspicious activities on-device, it sends detailed threat forensics data that can be used for SOC analysis.
Our detailed forensics can be integrated with Sentinel, providing a fuller, more detailed and clearer picture on what’s going on within a given organization as a whole, not just specifically on mobile or in silos on other endpoints. Organizations can maximize the value of all solutions and create a more cohesive security structure for the entire company.
Zimperium & Microsoft Azure Sentinel
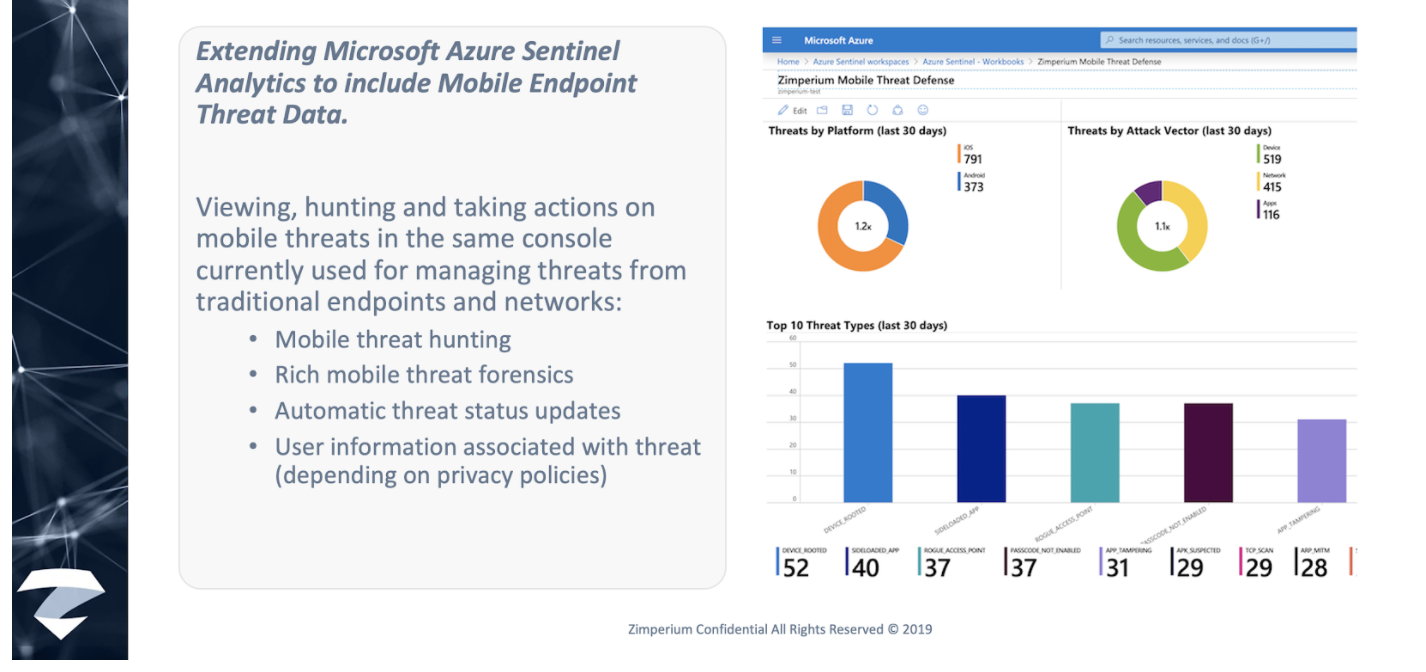
Any analytics tool is only as good as the data that it gains. We provide granular forensics and granular detections across that full stack of threats – both early on in the kill chain cycle and leading up to any full device compromises – so that organizations can leverage Sentinel to identify those initial exposure points, stop the attack in its tracks and prevent it from spreading across the rest of the organization.
Best of Both Worlds on-demand webinar
Watch our on-demand webinar to see David and Kern talk about and demonstrate:
- Integrating mobile threat data from Zimperium into Azure Sentinel;
- Achieving visibility, correlation and threat hunting across all endpoints and networks;
- Utilizing Azure Sentinel to respond to incidents with built-in orchestration and automations.
Contact us
To learn more or to schedule your own demonstration, please contact us.


