Authors: Pablo Morales, Esteban Tissot
Phishing scams remain a persistent threat in the digital world, constantly developing new methods to exploit trust. Mobile devices are not immune to this threat since, at the moment of writing, 78% of phishing sites are targeting mobile browsers. In this blog, we analyze the phishing lifetime from a dataset of URLs collected during March 2024, focusing on the fast deployment over the so-called “0-day” stage, the rising trend of HTTPS usage and the ability to use available sites to attack more than one target at a time. With this analysis, we will show the need of 0-day, On-Device, Real-Time detection for the user to be properly protected.
This article will focus on the Phishing Chronology. Analyzing 88014 phishing URLs collected from public sources and Zimperium data, we will show how dynamic and fast evolving are the phishing threats.
The diagram below shows the typical lifeline of a phishing site: the domain creation, certificate creation and the discovery (we are here purposely ignoring the phase in which content is added to the site). As the diagram highlights, 60% of the newly created domains get a SSL certificate during the first 2 hours of being registered. This means that in just 2 hours, a new phishing domain can be created and be fully operational over a secure HTTPS connection.
Another important point we will focus on in this article; 50% of phishing sites are discovered during the first week of being created, meaning that the other 50% of newly created phishing sites are alive as zero days for more than a week.
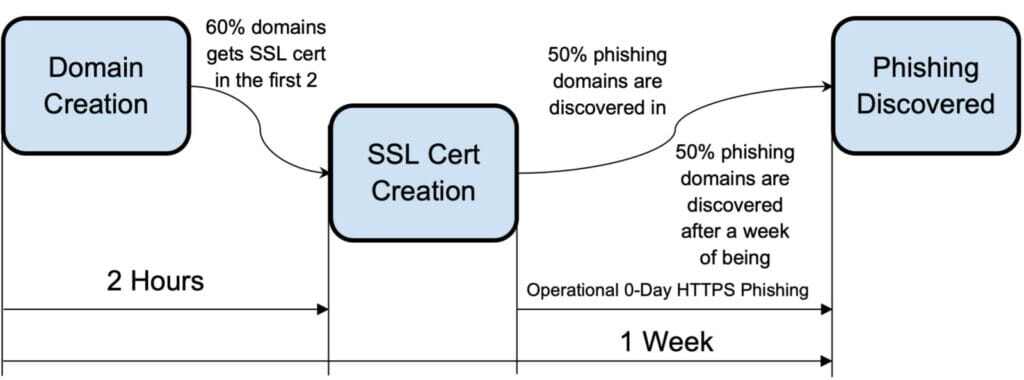
When a phishing site or domain is reported, it starts to appear in public blocklists, which allows tools like Google Safe Browsing to block them. During the timeframe the site is working as a zero day.
For the following analysis we used data phishing URLs from public sources collected over a period of 4 weeks along with Zimperium’s own threat data.
The rising use of secured phishing sites
Due to changes in browser behavior to treat non encrypted sites as less secure, and the ability to evade detection due to encrypted communication, attackers have been migrating to use secure communications (HTTPS) for modern phishing attacks.
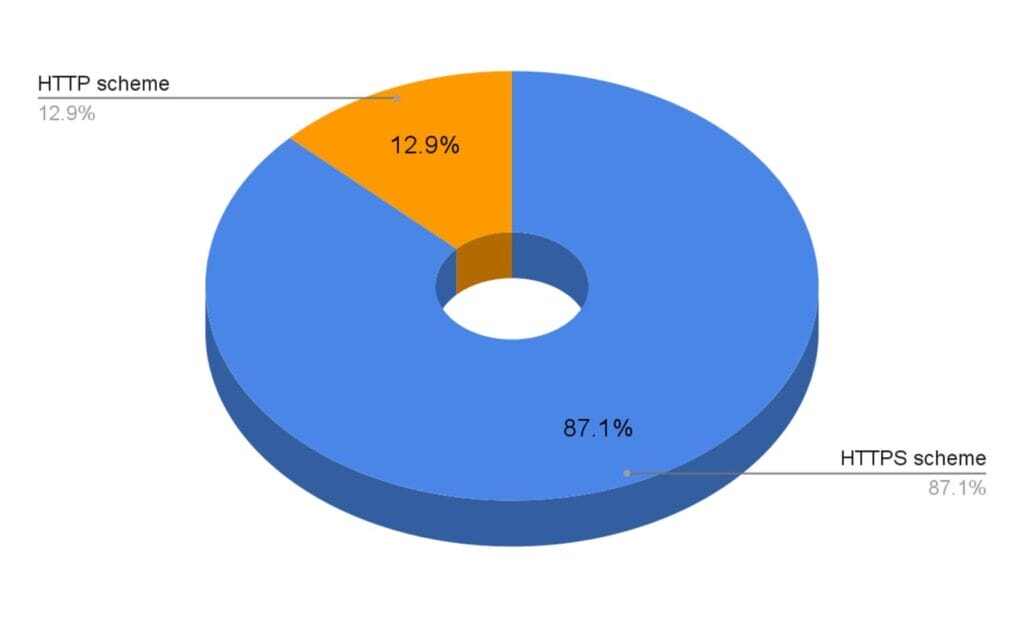
At the moment of writing, our analysis shows that only 12.9% of phishing URLs employ an unencrypted HTTP scheme, while 87.1% utilized the more secure HTTPS (including those that redirected from HTTP to HTTPS). The use of secured connections to serve malicious content can create a false sense of security for the user or mask malicious intent behind the “lock” icon on the browser.
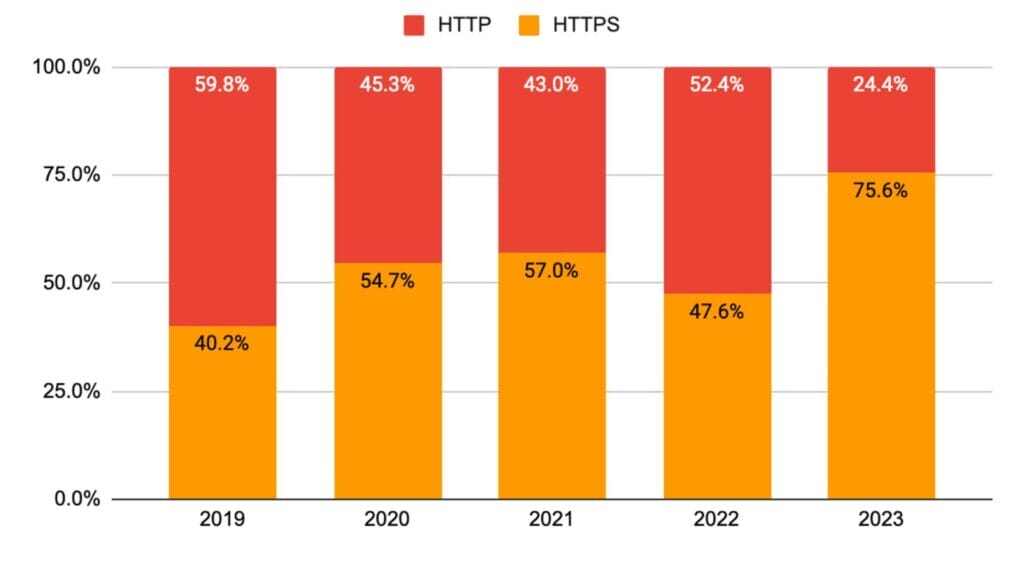
During our research we only analyzed the subset of URLs that use a SSL certificate (HTTPS). The below data highlights the rising trend of HTTPS usage in phishing attempts over recent years.
One domain, multiple targets
The analysis of SSL-certified URLs reveals a bunch of different domains used in phishing campaigns, each often hosting multiple fraudulent sites. On average, these phishing domains host approximately four distinct fraudulent sites, showing how attackers leverage a single domain to target multiple brands simultaneously. The graph below illustrates the domains that relate the different brands, thicker lines correspond to a greater number of domains.
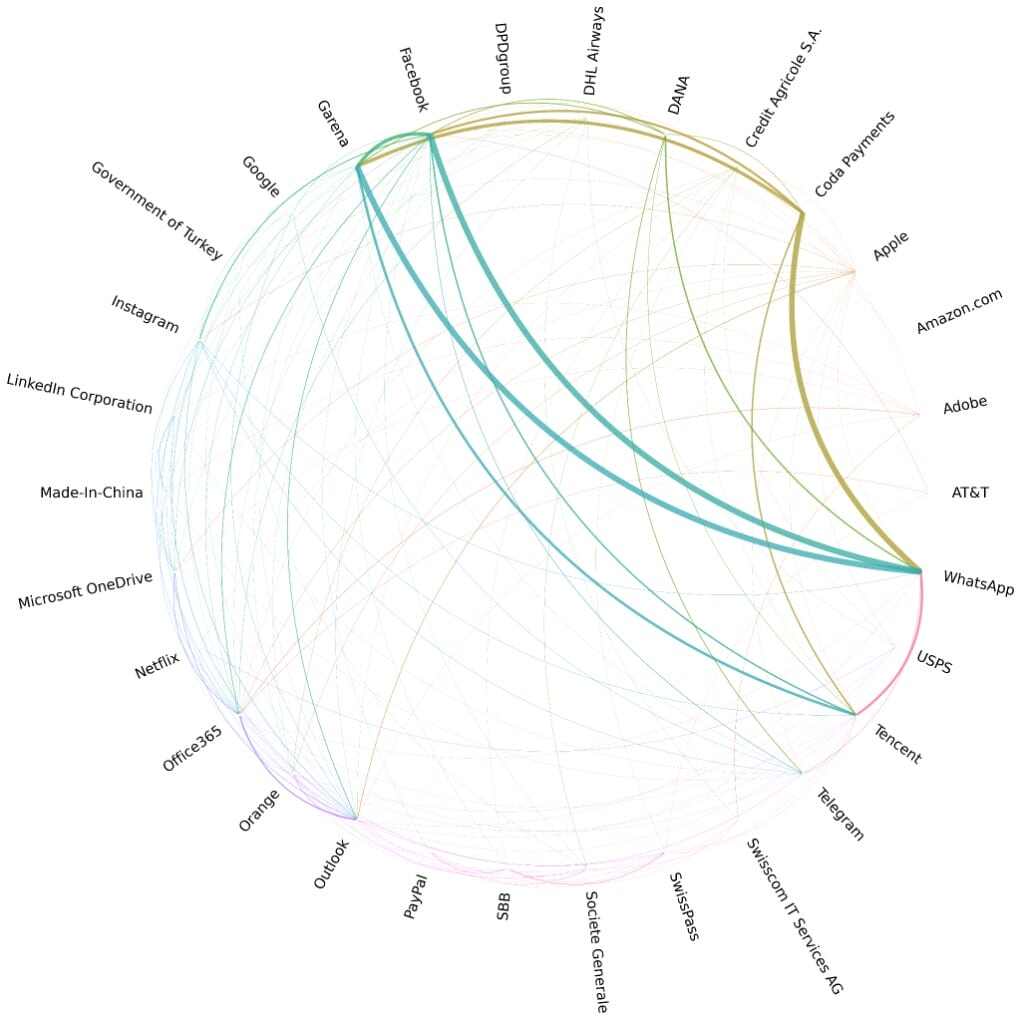
This chart shows that some types of brands tend to be attacked together. For example, WhatsApp appears along with Facebook and Instagram. We can also see brands that are targeting the same geography (such as Garena, Tencent and Coda Payments). Attackers tend to target multiple brands due to users reusing passwords; if an attacker obtains a social site credentials, it’s likely that the same or a similar password is used on other sites.
Temporal Dynamics: Unveiling the Phishing Chronology
In this section, we’ll perform a temporal analysis that will take in account the timestamp for phishing discovery time, the domain creation and the SSL certificate creation. It’ll consider a phishing site to become active, as soon as its domain is created (which is not true for every site, but it’s a fair simplification). The time between its creation and the discovery time is called “0-day”. It is the time window in which the threat is active without being reported.
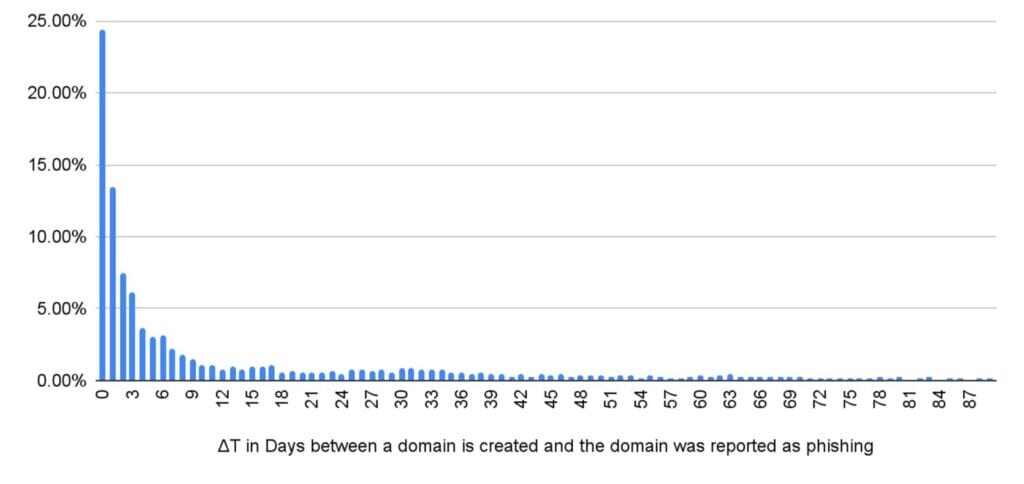
Time from creation until public detection
The histogram below shows the time elapsed between phishing domain creation and its appearance in public phishing lists, measured in days. The concentrated bars on the left side reveal that around half of phishing domains were reported within a week of being created, and almost 25% within a day. This highlights the fast deployment of new phishing sites, and the critical need for advanced zero-day detection technologies.
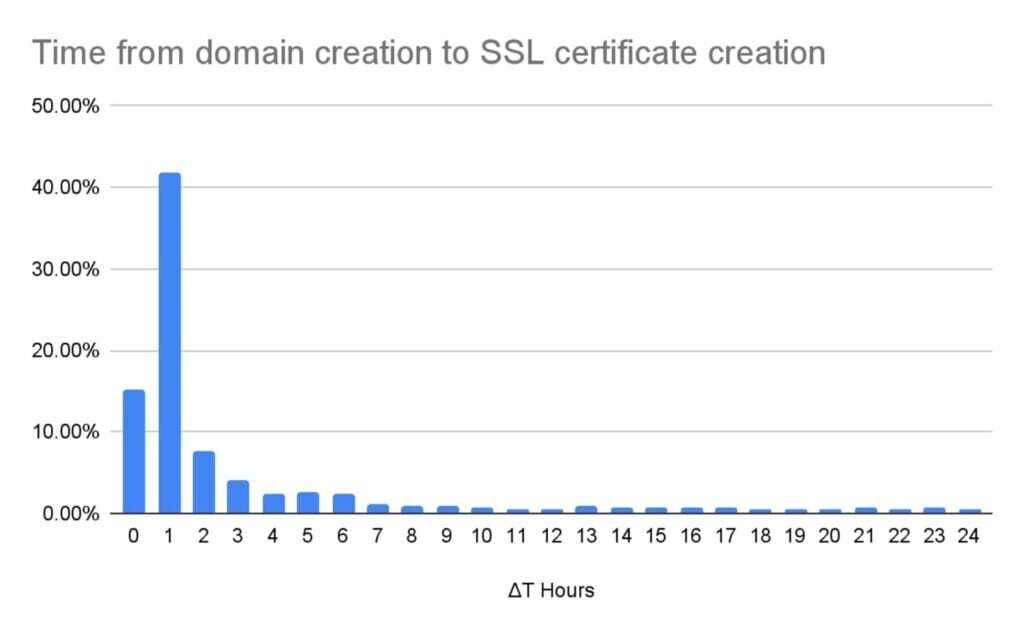
The next chart will show the time elapsed since the domain registration to the ssl certificate creation, which is necessary for a HTTPS site to become fully operational. The events in this chart are faster. Within the first 2 hours, almost 60% of the new created phishing domains already have a working SSL certificate. This behavior aligns with the current trend of most hosting sites providers offering SSL certificates in order to facilitate the work the user needs to do. At the same time, this generates the opportunity to detect malicious sites by monitoring newly created certificates.
Time from SSL Certificate Creation until public detection
The chart below shows the time passed between the SSL certificate being created until it is detected for the first time. As most of the certificates are created very close after the domain creation, the dynamic of this chart is very similar to Time from creation until public detection.
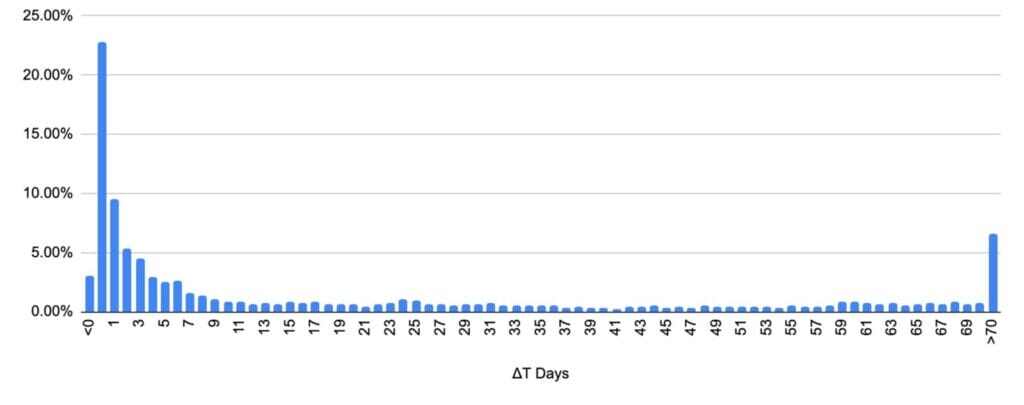
If we take a closer look at the previous chart, we can observe 3% of domains detected as phishing before the SSL certificate creation date. This is because a significant portion of these domains initially operated with HTTP scheme and before transitioning to HTTPS. The remaining domains consistently maintained HTTPS URLs, suggesting a pre-existing SSL certificate. It’s plausible that these certificates were created prior to our analysis, with updates occurring post-attack.
Zimperium Zero Day Phishing Protection
Phishing attacks remain the top threat for enterprises, evolving from simple email scams to sophisticated, multi-channel campaigns leveraging AI. Traditional security solutions and techniques are struggling to keep pace with these advanced phishing threats, exposing the organization and their users to significant risk. Moreover, mobile devices provide a unique attack surface for this type of attack.
Zimperium’s phishing protection solution offers a critical defense to today’s evolving phishing threats. By combining on-device and cloud-based technologies, we deliver comprehensive protection against the full spectrum of phishing attacks, including those delivered via email, SMS and social media. Our solution goes beyond static block lists, utilizing machine learning and behavioral analysis to detect even the most sophisticated phishing attempts.
With Zimperium, organizations can proactively defend against phishing attacks, safeguarding sensitive data and protecting their brand reputation. Our solution is the cornerstone of a robust cybersecurity strategy, empowering businesses to confidently navigate the ever-evolving threat landscape.


