On February 26, 2018, we received a notification from the detection system about a malicious sample with a suspicious package and Play Store name. We quickly verified the automatic analysis and confirmed the sample was actively trying to scam users to download it instead of the original BBC News mobile app.
On February 26, 2018, we received a notification from the detection system about a malicious sample with a suspicious package and Play Store name. We quickly verified the automatic analysis and confirmed the sample was actively trying to scam users to download it instead of the original BBC News mobile app.
Fake BBC Metadata
- Application Name: BBC News
- Company Name: BBC Worldwide [Ltd] (the original uses round brackets)
- Package Name: in.com.bbc.mobile.news.ww
- SHA256: 6df385b3f26725ceb9530bd6422910ee8501cc2d03a6fa3b515a7ce658a8a4e5
- Download Link: https://play.google.com/store/apps/details?id=in.com.bbc.mobile.news.ww (which is now unavailable). A cached copy of the original Play Store page can be found here.
Behavioral analysis
Once installed the fake app looks exactly like the original, the icons and drawers labels are the same, but once opened we can spot several differences: On the fake application, we can identify that the BBC News page is loaded in a WebView and that Ads seems to be spawned while browsing the tabs or reading a news.

Fake BBC News app
Real BBC News app
Static analysis
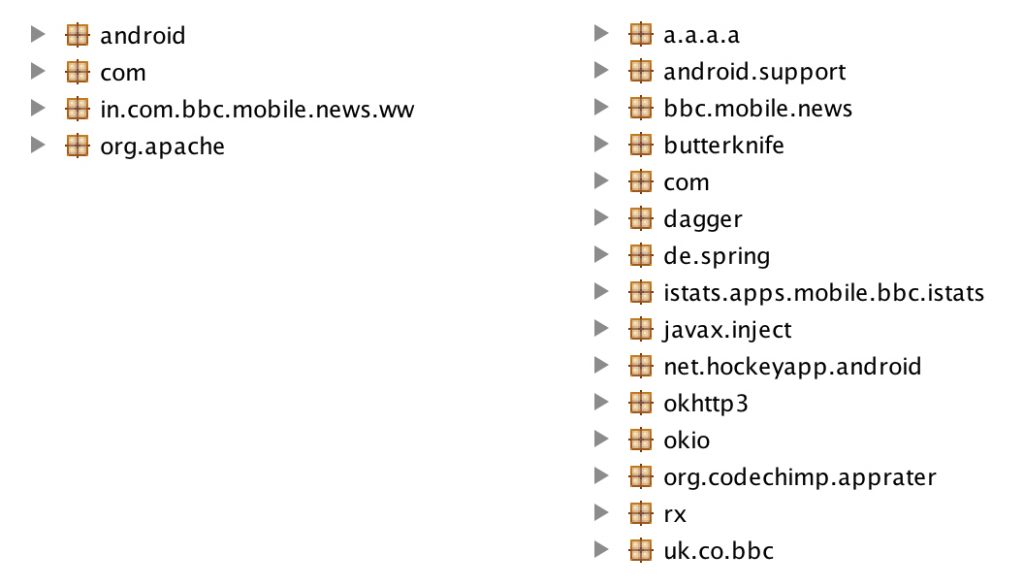
The application seems to have been around since June 21, 2017 and spread on all the unofficial Android markets and APK sites. Checking the AndroidManifest.xml, we can see that the versionName is 4.3.0.25, and comparing the fake and original samples from the same time period we notice a different package structure:
The fake package structure can be seen on the left and the real package structure can be seen on the right. The huge gap in the file sizes is also hinting that the differences are not limited to the Java code: 4 MB for the fake app and 15 MB for the original app. In fact all of the assets and resources do not match.
Usually the authors of such fake applications clone the original packages and inject some ads into them, but investigating the source code and the generated traffic from this sample we can notice that the fake application is acting as a placeholder. Its core structure could potentially be used to imitate other news mobile apps, or more generally mobile apps of services that also has a mobile website that can be loaded in the WebView.
Capturing the traffic, we noticed that the first query is sent to the malicious URL srv1.androidcreator.com; more specifically the following request took place:
| http://srv1.androidcreator.com/srv/config.php?v=9&vname=4.3.0.25&idapp=273964&idusu=229581196&cod_g=m7vgquoy&gp=0&am=0&pa_env=1&pa=US&pn=in.com.bbc.mobile.news.ww&fus=010100000000&recup_todo=1&aid=e622d243445e7c98 |
The application sends several pieces of information to the server and amongst them we can identify the vname=4.3.0.25, idapp=273964 and pn=in.com.bbc.mobile.news.ww to identify the application; some information about the device environment and the idusu=229581196 which is referenced several times in the source code and seems to be uniquely identifying the owner of the device. After the query has been processed, the server answers back with a bunch of configurations that will be appropriately handled by the application:
| [adotro2_cod=][adotro2_tipo=0][idusu=229581196][r_ms=][splash=1][vsp=0][c1_sp=FF000000][c2_sp=FF333333][ft=5][hcn=0][vcn=0][tcn=][icohome=1][vih=0][divisa=$puntoycoma][busc_campos=1,1,0,0][busc_orden=1,0,0][busc_def=TITULO ASC][prods_tit=][prods_masinfo=][prods_comprar=][prods_masinfo_mostrar=1][prods_linksexternos=0][prods_adaptar_ancho=0][pp_email=][pp_div=][cats=0][rt_tit=Rate our app][rt_txt=Do you like our app?][rt_ok=Yes, rate now][rt_ko=Maybe later][rt_1v=2][rt_int=2][ico_ofics_ord=2][ico_share_ord=3][ico_busc_ord=1][ico_exit_ord=0][ico_notif_ord=4][ic_po=0][io1=0][io3=0][ib1=0][ib3=0][is1=0][is3=0][ie1=0][ie3=0][in1=0][in3=0][nd_t=][ip1=0][ip3=0][ip5=0][our=1][appnext_cod=][appnext_cod_int_e=ace62326-e093-4e7d-91f2-73750fbe977b][appnext_cod_int_ia=67f897d3-f8e4-49ea-b3af-413a03e3401a][ap=1][mu=1][adotro_cod=][admob_int_cod=][fbi=][admob_int_v=4][admob_inte_v=4][admob_ch_v=20][admob_int_exit_v=0][admob_int_exit_r=0][admob_cod=][fbb=][appnextb_cod=][admob_pos=0][admob_sma=1][a_p_c=][n_p_c=][fbp=][a_p_s=][a_m_c=][n_m_c=][fbm=][a_m_s=][a_r_c=][n_r_c=][fbr=][r_mo=0][fca=][dom=bbcnews1][fb_m=0][b_c=0][l_c=1][fp=1][cvm=0][emo=1][i=01][cb=][notif_int=0][conf_ex=1][pp=1][share_subject=I recommend you this application for live tv][share_text=I am sending you this application that you may be interested. | |
| http://mobile.9apps.tv][petic_ask_nombre=2][petic_ask_email=2][petic_ask_tel=1][splash_w=2000][pwd=0][tipomenu=1][t_mas=0][bv_txt=][c1=FF000000][c2=FF333333][c_icos=FFCCCCCC][c_icos_t=FFCCCCCC][c_secc_noactiv=FFCCCCCC][c_secc_activ=FFFFFFFF][c_linea=FFFF0000][sep_secc=1][c_sep_secc=FFCCCCCC][t_ind=2][c_ind=FFFF0000][msl_c=FF000000][s_v=0][c1_ofic=FF000000][c2_ofic=FF333333][c_perofic=0][c_tit_ofic=FFFFFFFF][c_sep_ofic=FFCC0000][c_ico_sep_ofic=FFCC0000][c_txt_ofic=FFFFFFFF][c_icos_ofic=FFFFFFFF][c_ir_ofic=FFCCCCCC][c1_prods=FF000000][c2_prods=FF333333][c_txt_prods=FFFFFFFF][c_icos_prods=FFFFFFFF][c_icos_2_prods=FFCCCCCC][c_tit_prods=FFFFFFFF][c_sep_prods=FFFFFFFF][c_ico_sep_prods=FFFFFFFF][c1_prods_l=FF000000][c2_prods_l=FF333333][c_perprod=0][c_tit_prods_l=FFCC0000][c_precio_prods_l=FFFFFFFF][c_antiguedad_prods_l=FFFFFFFF][c_prods_det=FF333333][s1108700_tipo=1][s1108700_ord=1][s1108700_tit=BBC News][s1108700_idgo=][s1108700_ocu=0][s1108700_ext=0][s1108700_adapt=0][s1108700_r=0][s1108700_d=0][s1108700_url=http://www.bbc.com/news][s1108700_ua=][s1108700_loa=1][s1108700_zoo=1][wv_sc=0][wv_sc_txt=][wv_c=1][s1144098_tipo=1][s1144098_ord=2][s1144098_tit=Live TV][s1144098_idgo=][s1144098_ocu=0][s1144098_ext=0][s1144098_adapt=0][s1144098_r=0][s1144098_d=0][s1144098_url=http://mobile.9apps.tv][s1144098_ua=][s1144098_loa=0][s1144098_zoo=0][nsecc=2][idseccs=1108700,1144098][noficc=0][idofics=][fus=270218013601][FIN] |
We can spot several strings (some of them appeared also in the video): Rate our app, Do you like the app?, Yes, rate now, Maybe later, I recommend you this application for live tv, I am sending you this application that you may be interested.
The URLs to be loaded are present too: http://mobile.9apps.tv, http://www.bbc.com/news. We can also identify configurations about the UserAgent to be used or the title to be displayed. Finally, the advertisements IDs are received; this fake application is relying on AdMob and AppNext for the monetization process. Further analysis of the sample clarified that there is a core structure common to other samples too, and that it has been built by the Android Creator utility available at: www.androidcreator.com
A quick look into Android Creator
During the initialization phase, after the request and response with the server, the application checks if an updated version of the app is available and if available it will update. The response contains information about colors, labels and other graphical components to be used in the button or tabs of the app, confirming again that the concept is to have an application capable of adapting to several graphical layouts for maximal reuse. The utility lets the user build an application without actually knowing how to code for Android and all the configurations and actions are carried on using requests and responses between the application and the androidcreator.com server.
Querying Google we found several applications built with the utility, as an example the query “site:androidcreator.com” will return results for other applications and using the query “site:androidcreator.com BBC” will get the application ID of the Fake BBC app.
Banner of the Fake BBC News app in the androidcreator.com site.
We mentioned that the Android Creator utility let the user configure several actions, the Fake BBC News application contains the following request pages part of the srv1.androidcreator.com/srv/ URL, some examples are:
- cancelar_privado.php
- cancelar_solicitud.php
- chats_home.php
- coments_profile.php
- config.php
- eliminar_coment.php
- eliminar_fotogal.php
- eliminar_perfil.php
- eliminar_usu.php
- enviar_coment.php
- enviar_foto.php
- enviar_mensaje.php
- enviarmensaje.php
- favorito_usu.php
- fondo_guardado.php
- fotos_profile.php
Conclusion
The embedding of the ads seems to be optional, so we can surmise that the main goal of the Fake BBC News application seems to be monetization. The analyzed sample didn’t show dropping capabilities or sensitive data exfiltration, so it should be considered as an AdWare.
IOC
Fake BBC News: 6df385b3f26725ceb9530bd6422910ee8501cc2d03a6fa3b515a7ce658a8a4e5
Thanks
I would like to thank my fellow Zimperium teammates for their expertise and assistance, especially Gianluca Braga (@Matrix86_) and Christy Matthew (christypriory) .