Today, corporate networks and websites face varying degrees of cyber-threats – ranging from widespread well-publicized threats like the recent Heartbleed bug, to those that are less well-known, but just as damaging, like “Man-in-the-Middle” (MITM) attacks. The latter cyber-threat threats are network attacks that allow hackers to intercept users’ internet communication, steal sensitive data and even hijack sessions. Though MITM attacks vulnerabilities are prevalent and have existed for years, many of today’s largest websites and social networks still haven’t taken the necessary steps to protect users’ sensitive data from vulnerabilities that magnify the damage of this type of attack.
LinkedIn is one of these websites. Through a relatively straightforward MITM attack that leverages an SSL stripping technique, hackers can steal a user’s credentials and gain full control of the user’s account. Given the severity of this threat, it’s the security community’s responsibility to raise awareness, educate the public and urge these vulnerable companies to protect users’ data. We have reached out to LinkedIn six times over the last year to bring this critical vulnerability to their attention and have urged them to improve their network security, but more than a year after disclosing the bug they have yet to implement a patch for this vulnerability.
Using Zimperium Mobile Security System to the rescue:
We decided to use the mobile pentesting component of Zimperium Mobile Security System called zANTI, to evaluate LinkedIn’s public-facing cyber-vulnerabilities. zANTI mirrors the methods a cyber-attacker will use to audit security gaps on a network, allowing businesses to take appropriate corrective actions to fix critical security gaps.
What information is vulnerable?
Using basic MITM, we found that an attacker can extract a LinkedIn user’s credentials, hijack their session to gain access to all other LinkedIn information and impersonate the user. The following information is exposed, along with anything else that you, as a user, have access to:
- Email address
- Password
- Read and Sent Messages
- Connections
- “Who viewed my profile”
Attackers can impersonate the user to use any account feature, including:
- Send invitations to connect
- Edit the user’s profile
- Edit job postings
- Manage company pages
So not only is your personal LinkedIn information at risk, but also if you are an administrator for your corporate LinkedIn presence, your company’s brand reputation could also be damaged if a malicious actor were to gain control over posts and email communication on LinkedIn.
Who is vulnerable?
Every single user we tested was vulnerable to this attack. In addition, this vulnerability doesn’t just exist when an attacker is on the same network as the target – if an attacker has already compromised a device, once that device enters a different network, the attacker can use the victim’s device to attack other users on the same network.
Reproducing a MITM attack on LinkedIn
A hacker can use a MITM attack to intercept a user’s communication by replacing all “https” requests with its non-encrypted form, “http”. This technique is known in the security community as “SSL stripping”. This allows the attacker to read everything the victim does in plain text. Once the attacker has extracted a user’s credentials, they can reuse the user’s credentials or session cookies to authenticate and forge the exact session.
With LinkedIn, the default login page is using SSL so that users’ credentials (i.e., username and password) will be sent securely to the server. Once the user authentication is successful, it will redirect to http:// for the remainder of the time a user is browsing LinkedIn. This means that LinkedIn, one of the largest social networks, still has a significant portion of its website traffic that does not enforce the use of https://.
LinkedIn – Website login
By default, when a user types linkedin.com into their desktop browser, they will be redirected to https://www.linkedin.com. The typed username and password in the page with https:// will be sent to the server in an encrypted form that cannot be read.
After login
After successful authentication, the user will be redirected to http:// (i.e., http://www.linkedin.com/nhome/?trk=).
From this point on, the data will be sent over an unencrypted channel where an attacker can intercept the communication using a “Man-in-the-Middle” (MITM) attack and will be able to ‘sniff’ the communication.
SSL Strip
During the MITM attack, the attacker will strip all https:// requests to http:// in order to intercept the victim’s traffic – meaning all the communication data will be in plain text and easily read by the attacker. This attack is possible when an attacker is on the same network as the victim.
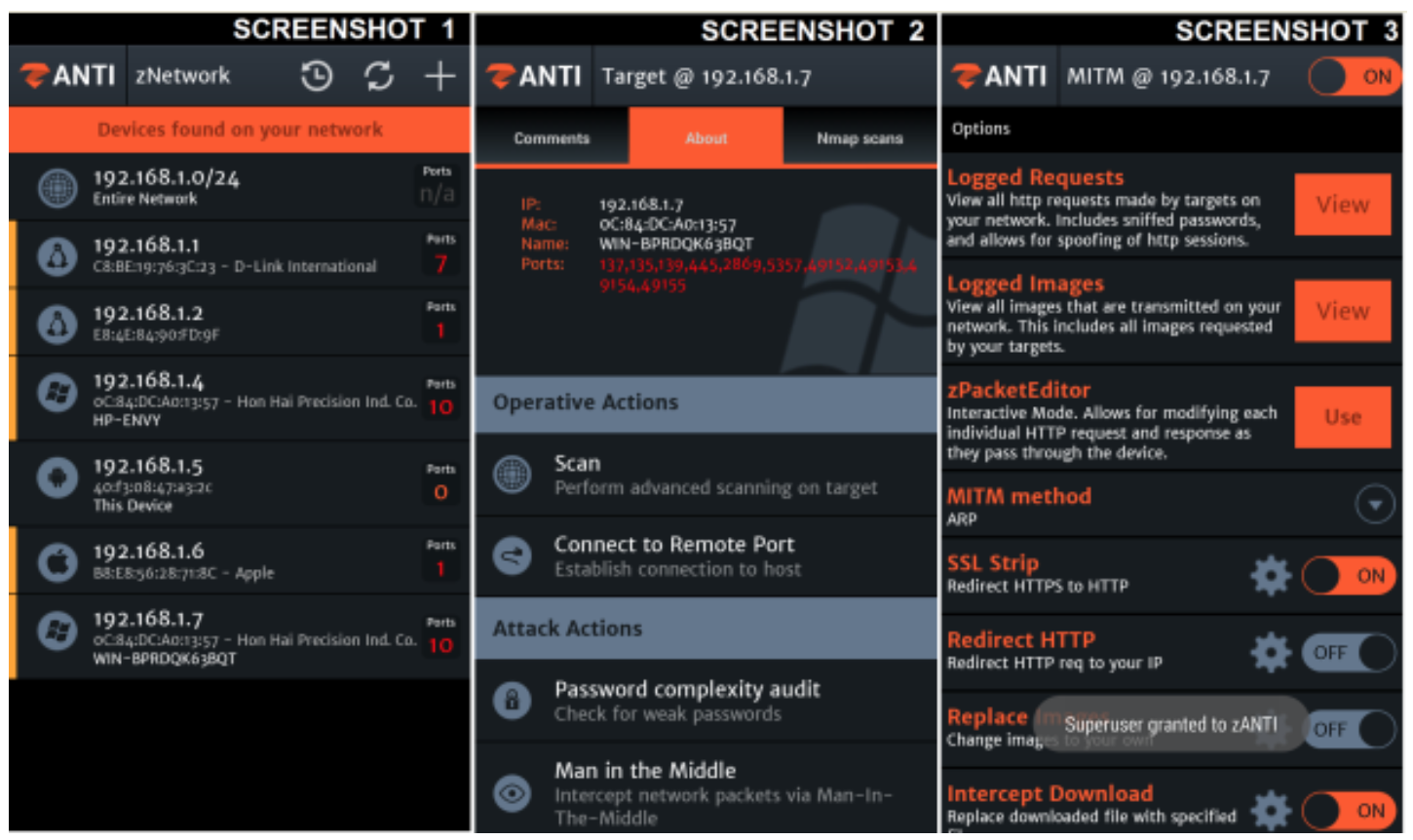
Steps to reproduce using zANTI
We used our mobile penetration testing toolkit, called zANTI, to reproduce this attack in the following steps:
- Scan the network
- Select a target
- Click on MITM
- Turn ON – SSL Strip (responsible for replacing https:// with http://)
- Turn ON – MITM
When users attempts to log into LinkedIn using linkedin.com, they are redirected to https://www.linkedin.com by default. When an attacker on the same network enables MITM with the SSL Strip, the https:// request is replaced with http:// and now the attacker can read the user’s data in plain text.
The user is redirected to http://www.linkedin.com.
When the victim types email and password, it’ll be sent over the network in an unencrypted form that can be easily read by any attacker – even the most amateur ones.
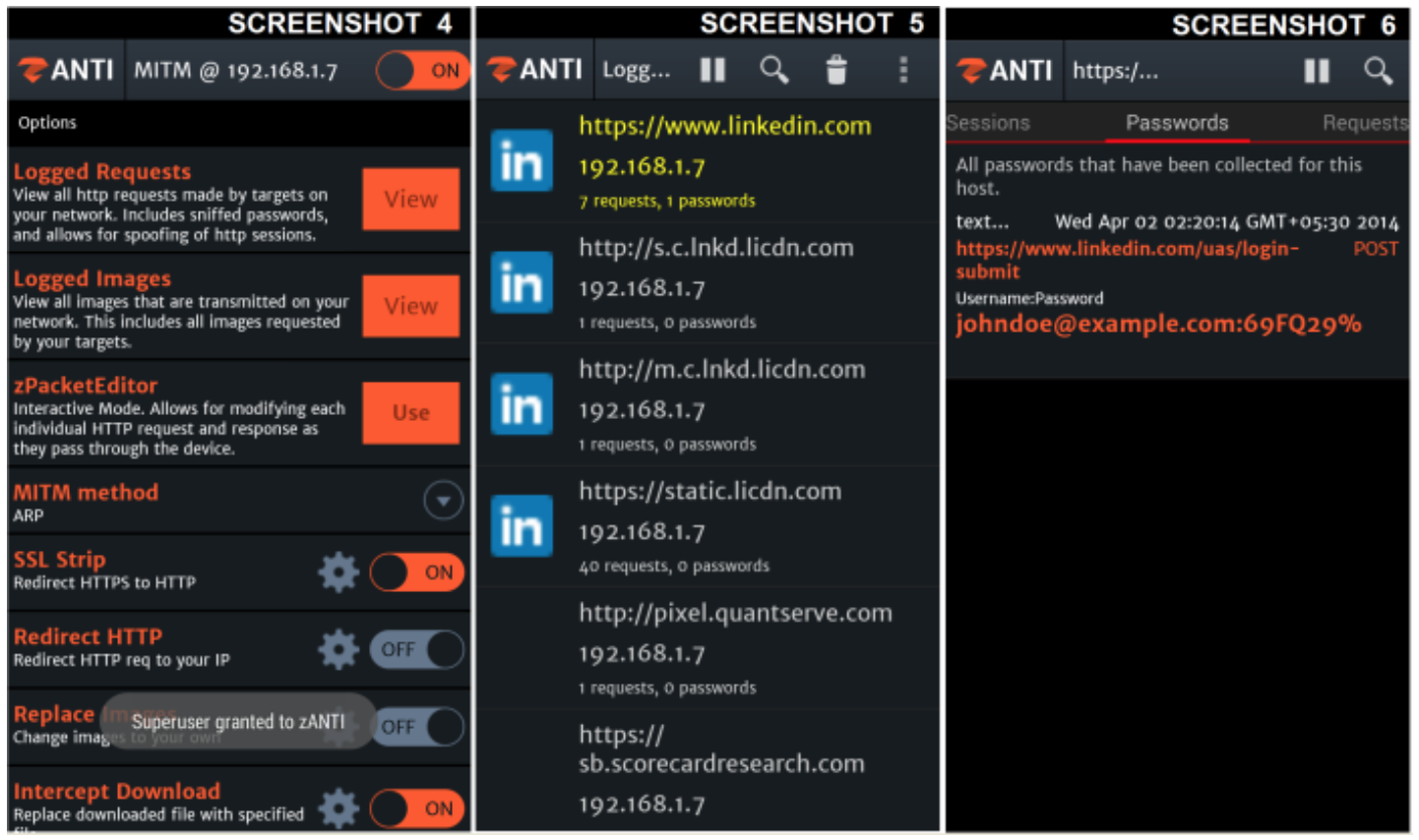
Logged requests
- View logged requests
- Select https://www.linkedin.com
- Sessions > tap left
- Password logs
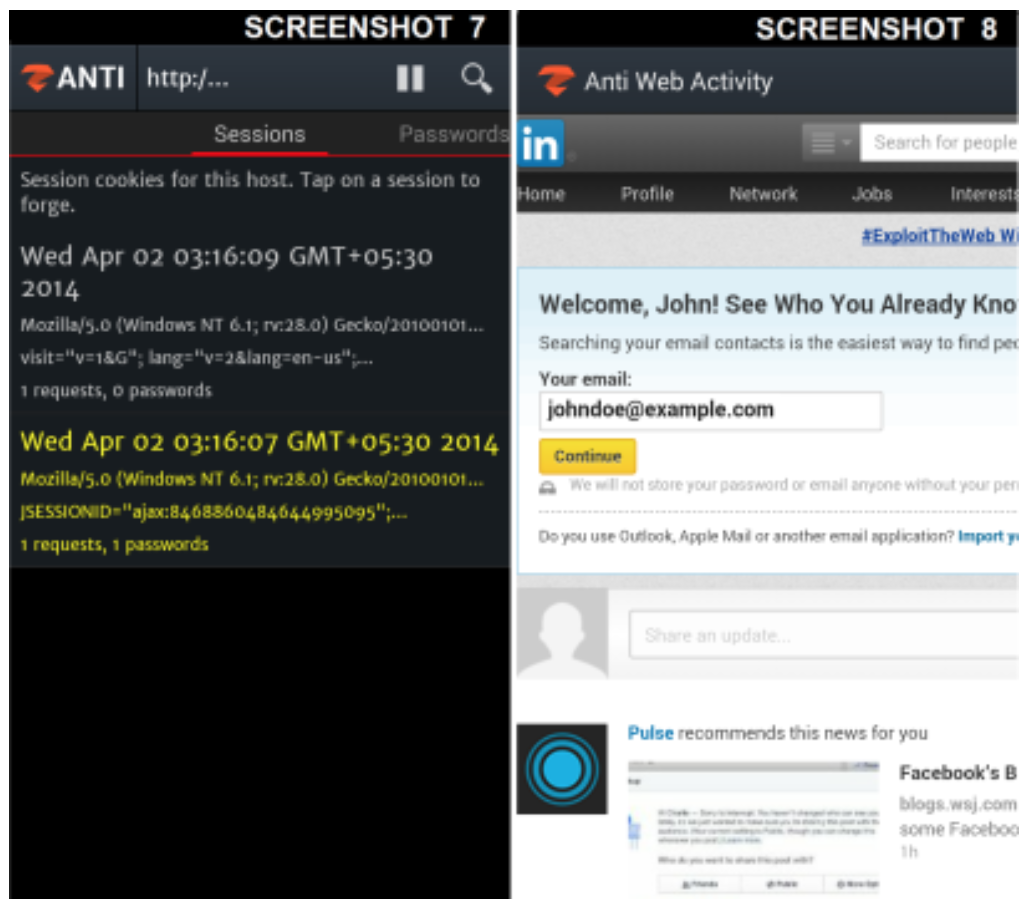
Session forge using MITM
If the user is already logged in when the attack is taking place, we’ve noticed (as shown above) that, after successful authentication, LinkedIn will redirect users to http:// web pages, where all communication data (including cookies) is in an unencrypted form and can be easily viewed by the attacker.
Assuming the victim is already logged in, the attacker can still grab the victim’s session cookies and reuse those cookies to be connect with the victim’s session – allowing the attacker to impersonate the victim..
Steps to reproduce using zANTI
- Start MITM on the target
- View logged requests
- Tap on the www.linkedin.com
- Tap on each session until you get a logged in session
- The screenshot of a successful session with reused cookies is below:
The attacker is able to:
- Edit the victim’s profile
- View connections
- Read messages, invitations
- Add secondary email
- Enable / disable notifications
MITM – Insert HTML
The attacker can also inject custom HTML/JavaScript code into all web pages served in http:// that could manipulate the content of your incoming/outgoing messages.
LinkedIn – Mobile website assessment
We tested LinkedIn’s mobile website and found it is also vulnerable. Attackers can strip the SSL and execute a MITM attack to forge the victim’s session on LinkedIn’s mobile site as well.
LinkedIn – Mobile app assessment
Currently, LinkedIn’s mobile app is not vulnerable to the threat of stealing user credentials via the same MITM attack or session forge. However, attackers can still sniff random HTTP requests and profile pictures.
Don’t trust Linkedin’s default settings – Turn ON HTTPS Manually
Until LinkedIn encrypts all its communication by default, you can protect yourself by enabling a security setting on the site that results in serving all traffic in https://. To do this, click “Review Privacy & Settings” on the drop-down menu that appears when you hover over your account icon, select “Account,” “Manage security settings”, and click the box that says, “A secure connection will be used when you are browsing LinkedIn.”
This will turn on HTTPS for all of your LinkedIn interactions, meaning that your communications will be encrypted when you’re already logged into your session and browsing through https://. However, if you attempt to log in by typing linkedin.com instead of https://www.linkedin.com, the hacker will still be able to steal your email and password so make sure that you type https:// whenever you login to linkedin’s service.
Zimperium Mobile Threat Defense customers are protected against this type of vulnerability via zIPS Mobile IPS app that detects MITM attacks before they have the opportunity to hijack your LinkedIn session as well as protection from advanced cyber attacks on mobile devices. Additional product information on the Zimperium Mobile Threat Defense suite is available at www.zimperium.com.
Zimperium Zero Day Disclosure Policy
Conclusion
As one of the largest social networks in the world, LinkedIn holds huge value in allowing users to connect and discover new business opportunities. However, LinkedIn’s vulnerability to cyber attacks threatens its millions of users — as personal data like email addresses, passwords, messages and more are vulnerable to be compromised by malicious actors. MITM attacks are extremely popular these days and the chances of getting hacked are high.
Today, people are more concerned than ever about their online security. For this reason, it’s imperative that users understand the threats they face and the steps they can take to keep their data safe until LinkedIn takes the necessary steps to secure the site from network attacks like MITM.
Vendor Disclosure History
This vulnerability is being disclosed publicly without a patch in accordance with the Zimperium 180-day zero-day policy. Multiple attempts have been made to disclose this vulnerability to LinkedIn since May 2013, and the vendor has chosen not to enforce secure connection on all users to date. Due to the popularity of MITM and the simplicity of this attack (require no modifications on behalf of the attackers) – we believe that this vulnerability is being used, in-the-wild, against Linkedin’s users.
Vendor Contact Timeline:
5/3/2013 – Zimperium responsibly disclosed a critical ‘session hijacking’ vulnerability to Vendor’s security team..
5/3/2013 – Vendor confirmed this vulnerability, but claims it does not affect users who have turned on the sub-menu to enforce SSL. During 2013 and 2014, all accounts that were tested by Zimperium to validate this vulnerability were vulnerable and did not have SSL enforced – which confirmed that most people are not aware of this option.
05/14/2013 – Zimperium asked Vendor for a status update. Vendor responded with the following statement: “Some of the product changes we are planning to introduce will address this issue, but we cannot comment on our future product roadmap or timeline.”
6/23/2013 – Zimperium asked for a status update. Vendor replied a day after on 6/24/2013 with the following statement: “We have no update at this time.”
8/5/2013 – Zimperium asked for a status update. Vendor replied with following statement: “If I recall our previous discussion, if our users select the secure connections option, the risk is averted.” Zimperium confirmed this is the case, but again called attention to the fact that this option is well hidden, and all of the users we had tested are vulnerable.
11/23/2013 – Zimperium asked for a status update.
12/2/2013 – Vendor responded: “We’re putting together a timeline for full-site SSL-by-default deployment in 2014, which will address the issue.”
2/7/2014 – Zimperium asked for status update. Vendor provided responded that they are still working on default SSL.
6/12/2014: Zimperium publicly disclosed.
Disclosure Timeline:
5/3/2103 – Initial contact attempt with vendor
6/18/2014 – Public release of advisory