Identifying a problem is a critical first step, but there can be a big leap between detecting an issue and fixing it. This is very much the case when it comes to mobile device security in today’s enterprises.
There’s now general awareness of the fact that mobile devices are posing a significant risk. For example, when asked to identify which category of endpoints had the weakest security in their organization, survey respondents chose mobile devices above all other categories. In fact, mobile devices received 44% of responses, and laptops were a distant second, with 30%.
In spite of this recognition from security and tech leaders, the mobile security problem persists. Phishing attacks in particular are a constant threat, and these attacks are proving effective. According to the recent Verizon Mobile Security Index report, 83% of organizations experienced an email-based phishing attack that successfully tricked a user into taking a risky action, such as clicking a malicious link or downloading malware. Further, in our analysis of forensic data, we’ve found that 75% of phishing sites either targeted mobile devices exclusively or were specifically coded to ensure a mobile-friendly format.
While it’s one thing to learn about these risks at a high level, it’s important to understand exactly how these attacks work in reality. Fortunately, Zimperium can help. Through our deployments, we effectively have 70 million sensors out in the world that report back on the malicious activities impacting enterprise-connected mobile devices every day. In the following sections, we will describe a few examples of what different mobile threat chains look like in reality.
Following are a few key points to consider as you review the examples below:
- Running the latest OS releases is important—but insufficient. We’ve seen many cases of successful attacks targeting devices that had the latest releases of iOS and Android.
- iPhone users aren’t immune. We still hear from individuals who basically feel that, because they’re using an iOS device, they’re somehow immune from cyberattacks. Our data should dispel that notion. The reality is that iPhones are being targeted constantly, and too often, these attacks are proving to be effective.
- Zimperium detected each step. The examples below are drawn from Zimperium solutions. Each designated step was detected by our mobile threat defense system.
- Users need to be educated. Regarding the multi-step attacks detailed below, it is important to underscore that alerts were generated at each phase. Attacks only succeeded in compromising devices because users chose to ignore those warnings.
- Privacy is protected. In each of these examples, a customer’s security operations staff will be given the specifics they need to remediate an issue. Zimperium can report on the high-level indicators of compromise, such as a device connected to a phishing site and that was subsequently tampered with. However, we’re unable to report on the specific details of the site or tampering. More importantly, personal data, such as emails, passwords, and other information, is never collected in Zimperium solutions.
Full Compromise Based on Network Attack
In this example, an individual connected to an insecure Wi-Fi network with a rogue access point. The device is rooted, which enables multiple cases of system tampering. For example, a file system can be remounted, enabling an attacker to gain a persistent presence on the device. Alternatively, a file system may be modified in a way that it shouldn’t be.
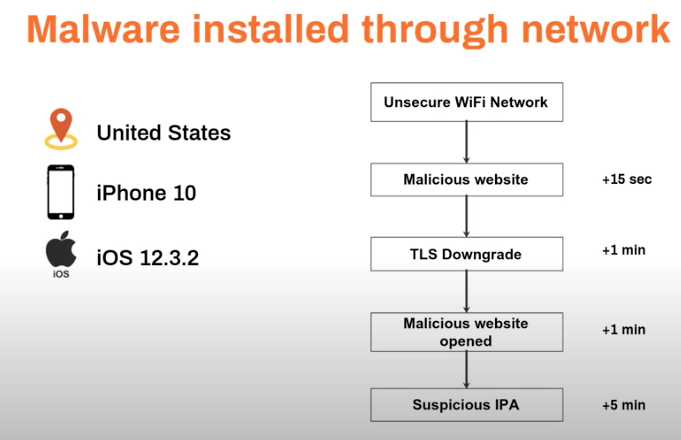
Malware Installed Through a Network
Generally, a user can be directed to a malicious website in two ways. First, a phishing attack sent via email or SMS may trick a user into clicking on a link that directs to the site. Alternatively, an attacker on an insecure network can surreptitiously start redirecting a device’s traffic to or through a device within their control. This latter approach is how it worked in this example.
The device operating in an insecure network is directed to a phishing site. Next, we see the device’s TLS requirements disabled, which means unencrypted traffic can be accepted. This means anything entered on the site, whether credentials, personal information, payment card details, and so on, will be visible. Finally, we see that the user actually installs a malicious iOS application on their device.
Compromise of an Android Device, Example 1
In this case, a user compromises their own device without knowing. The individual has developer options turned on, and within a day, we see several applications sideloaded. Within an hour, we see that there is evidence of system tampering. Ultimately, SELinux, a security module for Linux systems, is disabled, meaning the device isn’t protected from a range of additional threats.
Compromise of an Android Device, Example 2
In this example, the device is being used in an insecure network, say, a café’s Wi-Fi. First, the attacker identifies the device using a TCP scan, a form of reconnaissance and then uses a man-in-the-middle approach to insert their own device as the router. Next, an SSL strip is used to turn off encryption requirements, which means all data and actions are visible. Finally, the user may be issued a notification, for example, that in order to keep browsing, they need to download an app. In this way, the user is tricked into installing malware.
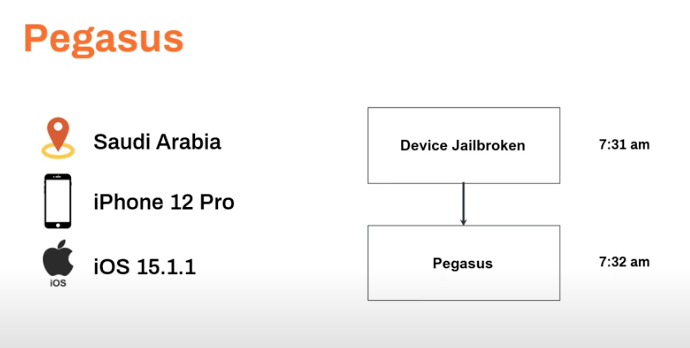
Pegasus-Based Compromise
Pegasus is one of the most notorious pieces of spyware. Sold by an Israeli cyber-arms company, NSO Group, this spyware is capable of reading text messages, tracking calls, collecting passwords, and more. Pegasus has been used by a range of organizations to target tens of thousands of victims, including activists, journalists, heads of state, and more.
In the last six months, we’ve detected three incidents of Pegasus on mobile devices. This spyware takes advantage of a zero-day exploit to jailbreak the device and enable the spyware to be installed without the user knowing. This can happen in minutes. In this example, an individual in Saudi Arabia was using a relatively new device, an iPhone 12 Pro, and running one of the more current operating system versions, and their device was still compromised. It was only through the telemetry data captured by Zimperium that this user and their organization were notified and protected.
Learn More
To learn more about these attack chains and how Zimperium can help, be sure to view our recent webinar, “Mobile Threat Chains: Patterns of Attack Against Enterprise Devices.”