- 14% of Devices Contain Malware
- 4% detected a Man-in-the-Middle Attack
- 1 of 3 Devices Not Running Latest Version
Mobile devices are now standard computing platforms in businesses of all sizes. U.S. consumers now spend over 5 hours per day on mobile devices [1]. The average time spent per day on mobile devices has increased every quarter since users prefer the ease of use and mobility. As more time is spent on mobile, personal and company data (e.g., emails, contacts, calendars, documents, photos, credentials) on the devices are exposed to theft and other misuse.
Perpetrators have long sought out the path of least resistance. An individual’s personal and enterprise data is most vulnerable via mobile devices since most of time spent is away from secure networks, on public Wi-Fi and on apps they do not control. Security conscious companies understand the threat and have installed mobile threat defense apps like Zimperium zIPS on both corporate and BYO devices.
During the first quarter, Jan. 1 – Mar. 31, 2017, zIPS-protected devices detected several types of mobile device risks and threats around the world. The risks and threats are described as follows:
- Device Threats & Risks – Threats to the device or OS, including unpatched vulnerabilities
- Network Threats – Threats delivered to the device via the cell network or Wi-Fi
- App Threats – Mobile Malware, Spyware, Adware, or “leaky apps” on devices
Device Risks and Threats
 Attackers are constantly finding new and unique ways to exploit mobile operating systems. Sophisticated remote attacks do not require end-user interaction to install or detonate an attack in order to compromise a device. Remote attacks are difficult to detect during or after an attack without a mobile threat defense solution monitoring the device OS behaviors and file systems.
Attackers are constantly finding new and unique ways to exploit mobile operating systems. Sophisticated remote attacks do not require end-user interaction to install or detonate an attack in order to compromise a device. Remote attacks are difficult to detect during or after an attack without a mobile threat defense solution monitoring the device OS behaviors and file systems.
Since 2016 there have been over 600 CVEs registered for Android and 300 for iOS [2]. While not all vulnerabilities are severe, there were still hundreds that enabled remote code execution like Stagefright and Pegasus that forced the business world to pay attention to mobile device security.
Data from Zimperium’s customers was collected and reported in aggregate for device risks associated with mobile device configurations, settings, and installed operating system versions. The risks are separated by each operating system, Android and iOS, since each has its own update ecosystem.
For this first quarter of 2017, we analyzed devices running Zimperium’s zIPS app on Android and iOS. Out of all of the Android devices, 98% of them are not running the latest version available as of March 31, 2017 [3]. Less than 2% of Android devices are running the latest 7.1+, which leaves the remaining devices running older versions vulnerable to known exploits mentioned earlier. Even more concerning are the configuration settings on 15% of the devices. These devices are rooted, allow downloads from stores outside of Play or have developer options enabled. These configurations make the devices more susceptible to attack without running the zIPS mobile threat defense app. Five percent of the devices analyzed have USB debugging enabled on the device. USB debugging enables an Android device to communicate with the Android SDK (Software Developer Kit) over a USB connection. It’s best not to enable this setting if you are not a developer or fully aware of the security issues USB debugging introduces.
The fragmented Android update process is well documented, but a surprisingly high number of iOS devices are not running the latest version either. Greater than 35% of iOS devices were not running the latest version iOS 10.3 and haven’t received security updates as of March 31, 2017. Since Apple controls the OS and the process to update devices, many believe devices are updated in a timely fashion. Our data shows one of three iOS devices do not update the OS when it becomes available. The most concerning risks associated with iOS devices were malicious configuration profiles and “leaky apps.” These profiles can allow third parties to maintain persistence on your device, decrypt your traffic, synchronize your calendars and contacts, know your location and could allow a remote connection to control the device or siphon data from the device without the user knowing. These profiles were installed in lieu of security policies in the MDM since they cannot be detected without MTD.
Keeping your devices updated is an important part of keeping them secure. The mobile operating systems are constantly being modified and receive hundreds of security updates every year as the platforms continue to evolve. In 2016, there were 523 registered CVEs for Android. Nearly half the vulnerabilities scored 7+ on the Common Vulnerability Scoring System (CVSS) scale, meaning they were high risk allowing code execution or memory corruption. There were 161 vulnerabilities and exposures registered for iOS in the same time period. Over 40 percent of the iOS vulnerabilities scored 7+ on CVSS [4].
Network Threats and Attacks
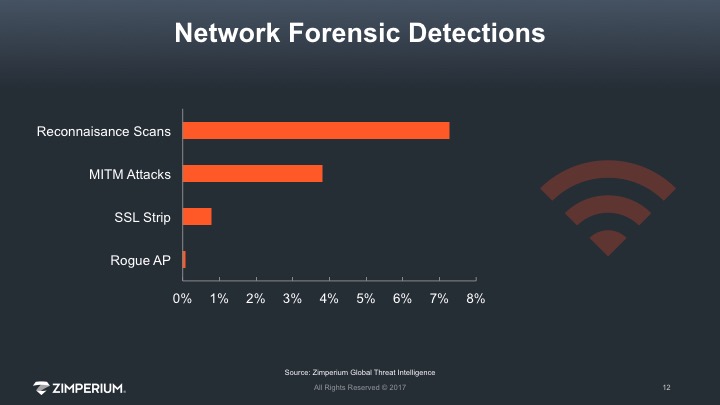 When an attacker intercepts a mobile device’s network traffic through techniques such as a Man-in-the-Middle (MITM) attack or a rogue access point, the device and its data are exposed to many different threats. An attacker can read and capture credentials, emails, calendars, contacts and other sensitive data as part of a more advanced attack.
When an attacker intercepts a mobile device’s network traffic through techniques such as a Man-in-the-Middle (MITM) attack or a rogue access point, the device and its data are exposed to many different threats. An attacker can read and capture credentials, emails, calendars, contacts and other sensitive data as part of a more advanced attack.
For the first quarter of 2017, our data shows over 7% of all devices detected a reconnaissance scan from a network device or an attacker. Many of these devices experienced multiple scans over the quarter. Attackers scan networks to find victims and reroute traffic via a MITM attack. On half of the devices that experienced a scan, zIPS automatically detected a MITM attack and simultaneously reported it to the customer’s security team. This is the most severe type of network attack since it is usually invisible to a user. Unless a user has a mobile threat defense app that can detect the attack on his/her device in real-time (e.g., zIPS), their wireless connection can be rerouted to a proxy and their data may be compromised.
Rogue access points are another network attack that reroutes traffic. A rogue access point is a wireless access point that has been installed on a secure network without explicit authorization from a local network administrator. Rogue access points can be placed anywhere and follow trusted naming conventions to capture traffic from potential targets. Nearly 1% of devices detected a rogue access point after a device connected to it. zIPS was able to detect these rogue network devices, report back to the corporate security teams and automatically terminate the session if the security policy dictated and configured that action.
App Risks and Threats
 Apps can be used to deliver and execute malicious code to compromise a device, or to act as a proxy in a more sophisticated attack. App-based attack examples include examples like XcodeGhost on iOS and Gooligan, a family of Android-based malware.
Apps can be used to deliver and execute malicious code to compromise a device, or to act as a proxy in a more sophisticated attack. App-based attack examples include examples like XcodeGhost on iOS and Gooligan, a family of Android-based malware.
Since Zimperium provides on-device detection, we don’t require signatures or hashes to detect malicious activity on the device. Zimperium monitors the OS behavior for anomalies and can detect attacks in real-time that would otherwise not be detected by only looking for malware. Zimperium’s mobile application reputation service scans apps installed on devices or in app stores and interrogates them for security issues and privacy abuse enabling security teams to make informed decisions.
Over the first quarter, Zimperium analyzed apps on users’ devices to report on malware, security issues and privacy abuse. Among the devices running Android, we found 13% of devices had apps containing known malware. Each of the devices containing malware logged an event and provided recommendations to the user and the enterprise security team. The number of iOS devices containing known malware represent less than 1% of devices from which we collected data. While only 1% of Apple devices saw mobile malware, they have a greater percentage of suspicious profiles, apps using weak encryption and potentially retrieving private information from devices. Our analysis found over 19% of apps had the capability of retrieving private information like passwords and device’s Unique Device Identifier, UDID. Retrieving the UDID from devices has been prohibited by Apple since 2011. Approximately 3% of the apps were using weak encryption or hashing algorithms – like MD2 – and are not considered secure to pass private or payment data.
If you would like to obtain forensic detail like the above for your enterprise devices, please contact us to set up the appropriate steps.
Sources
- http://flurrymobile.tumblr.com/post/157921590345/us-consumers-time-spent-on-mobile-crosses-5
- https://cve.mitre.org/
- Zimperium, Inc.
- CVEdetails.com


