Securing Medical Devices & Their Connected Digital Health Apps
Connected medical devices are in high demand, and their usage continues to grow. This growth has been fueled by increased adoption of compatible devices, expanded internet access, and the substantial growth in IoT technology across medical applications. The demand for real-time remote health monitoring via connected IoT devices is also fueling growth. By 2028, the connected medical device market is projected to reach USD 136.76 billion, growing at an annual rate of around 22%. [Source]
Connected medical devices have emerged as life-changing products in such areas as diabetes, neuroscience, and cardiovascular health. These products have a direct connection to patient health. Consequently, the FDA regulates pre-market submissions related to these devices’ marketing and manufacturing via the 510(k) process.
Over the last few years, several hacks and security incidents impacted the larger healthcare ecosystem. In response, the FDA has reclassified these devices as “cyber devices.” The FDA recognizes that internet connectivity and sophisticated technological features make these medical devices more vulnerable than ever before. Once these products are released to the market, they can be accessed by malicious actors and exposed to a variety of threats. A new round of guidance was issued by the FDA in December 2022 as part of the Omnibus Appropriations Act Section 524B, which went into effect on March 29, 2023, and was explicitly added to ensure post-market cybersecurity of medical devices.
The new guidance requires that medical device companies have a plan for monitoring, identifying, and addressing postmarket cybersecurity vulnerabilities and exploits and for doing so in a reasonable timeframe. These companies must ensure their devices and related systems are secure and provide any required postmarket updates and patches. A software bill of materials must also be submitted, including for any commercial, open-source, and off-the-shelf software components used.
The new FDA guidance is a step in the right direction. Medical device companies are highly skilled in building specialized hardware, but they are not security experts. But the cybersecurity concern is not limited to just the software on the actual device. Today’s connected medical device products are no longer just restricted to specialized hardware running proprietary software. Devices now send data to and are controlled by sophisticated mobile applications. Malicious actors looking to compromise the device and health information may find this to be a low-hanging fruit.
Today, these mobile health apps, also referred to as digital health apps, are more than just diagnostic monitors; they transmit info to providers and are increasingly controlling the medical devices that administer treatments. While these apps provide tremendous value, they also create a new attack surface that is susceptible to vulnerabilities and exploits. This is compounded by the fact that most mobile applications in public app stores have security gaps, which leave them exposed to emerging security threats.
Last year, we conducted research into more than a million public applications. This research shows that the security within these apps was lacking in several critical areas.
Android Applications

iOS Applications
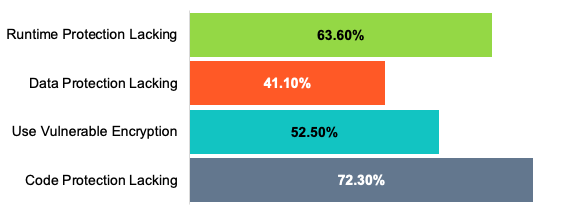
In order to ensure that their devices are secure, medical device manufacturers need to secure the digital health apps associated with their products.
How Zimperium Helps You Build Secure Digital Health Apps
Today, Zimperium secures more than ten mobile apps that the FDA has cleared to connect to medical devices.
Zimperium’s Mobile Application Security Suite (MAPS) helps medical device companies build secure, FDA-compliant mobile applications. MAPS is the only unified solution that combines comprehensive in-app protection with centralized threat visibility. The solution offers these advantages:
- Pre-Market Compliance
- During development and pre-release testing, continuous Mobile Application Security Testing (MAST) enables pre-release visibility into mobile applications.
- Post-Market Compliance
- Our in-app protection includes application shielding, runtime application self-protection (RASP), and anti-malware.
- The solution features RASP capabilities that provide post-release visibility into threats and attacks occurring on the end user’s device.
To learn more about Zimperium MAPS, contact us today.
