Application sideloading is the practice of installing applications through non-official distribution channels. While this allows for greater customization and app availability, it also opens the door to significant security vulnerabilities increasing the attack surface users are exposed to.
In this blog post, we will discuss the differences between Android and iOS sideloading and delve into the specific risks associated with sideloading applications using Zimperium’s own telemetry.
Sideloading 101
For most device owners, installing a new application onto their devices is a simple and safe process. We go to our device’s official app store (e.g., Google Play Store, Apple App Store, or OEM store), search for an application, and click the download and install button—a simple, safe, and harmless process.
But this is not the full story. When it comes to our mobile devices, mobile applications allow us the freedom and opportunity to personalize our digital experiences. However, we are limited when only restricted to the device’s official app stores. This is why users engage in “sideloading”.
Sideloading refers to installing an application onto a device from a source outside of the manufacturer’s official app stores, granting users greater control and flexibility. This app installation method is often used by users who want to access apps that are unavailable in their region, aren’t approved by the official app stores, perform illegal activities, such as bypassing DRM, or gain access to advanced features that might otherwise be restricted.
Developers also benefit from this practice. It facilitates faster development cycles by allowing them to distribute pre-release versions directly to testers, bypassing the official app store’s approval process. This enables quicker feedback loops and iterative development before a public release. Developers can gather feedback on their apps from a targeted group of testers before submitting them to the official store. Additionally, sideloading allows a device owner to install an application when internet connectivity is not available.
Sideloading is a fairly popular practice. Our research indicates that 18.3% of mobile users globally engage in sideloading. In some regions, such as the Asia Pacific, the impact is as high as 43%.
Unfortunately, because of how sideloading works it exposes users to risk and abuse, something the official app stores try to mitigate with its controlled ecosystem and vetting processes. According to our telemetry, users who engage in sideloading are 80% more likely to have malware running on their devices compared to those who do not. In fact, sideloading is a great contributor to malware risk; in 38.5% of cases where malware was detected, the source can be traced back to a sideloaded application.
Let us now take a closer look at how users sideload applications and the details of the associated risks.
The sideloading guide to the galaxy
The process to sideload applications differs from Android to iOS.
Android
For years, Android has supported freedom of choice, allowing the device owner to override the default installation process. To enable this option, device owners just needed to follow a few simple steps.
Distribution and installation of Android applications is done using an APK (Android Package Kit) file. APKs are executable files that contain everything necessary to install and run an application on an Android device. These files can be obtained from the official app store or from sources commonly known as 3rd party sources. Examples of 3rd party app sources include:
- 3rd Party app downloader apps
- Internet hosted sites
- File Sharing services
- Enterprise application stores
Once an application has been downloaded, the device owner can either install it directly (direct sideloading) or have another application do the installation.
“Direct sideloading” consists of downloading an APK, enabling developer options and USB debugging, connecting the device to a computer, and installing the application using Android Debug Bridge (ADB). This is shown in the following figure.
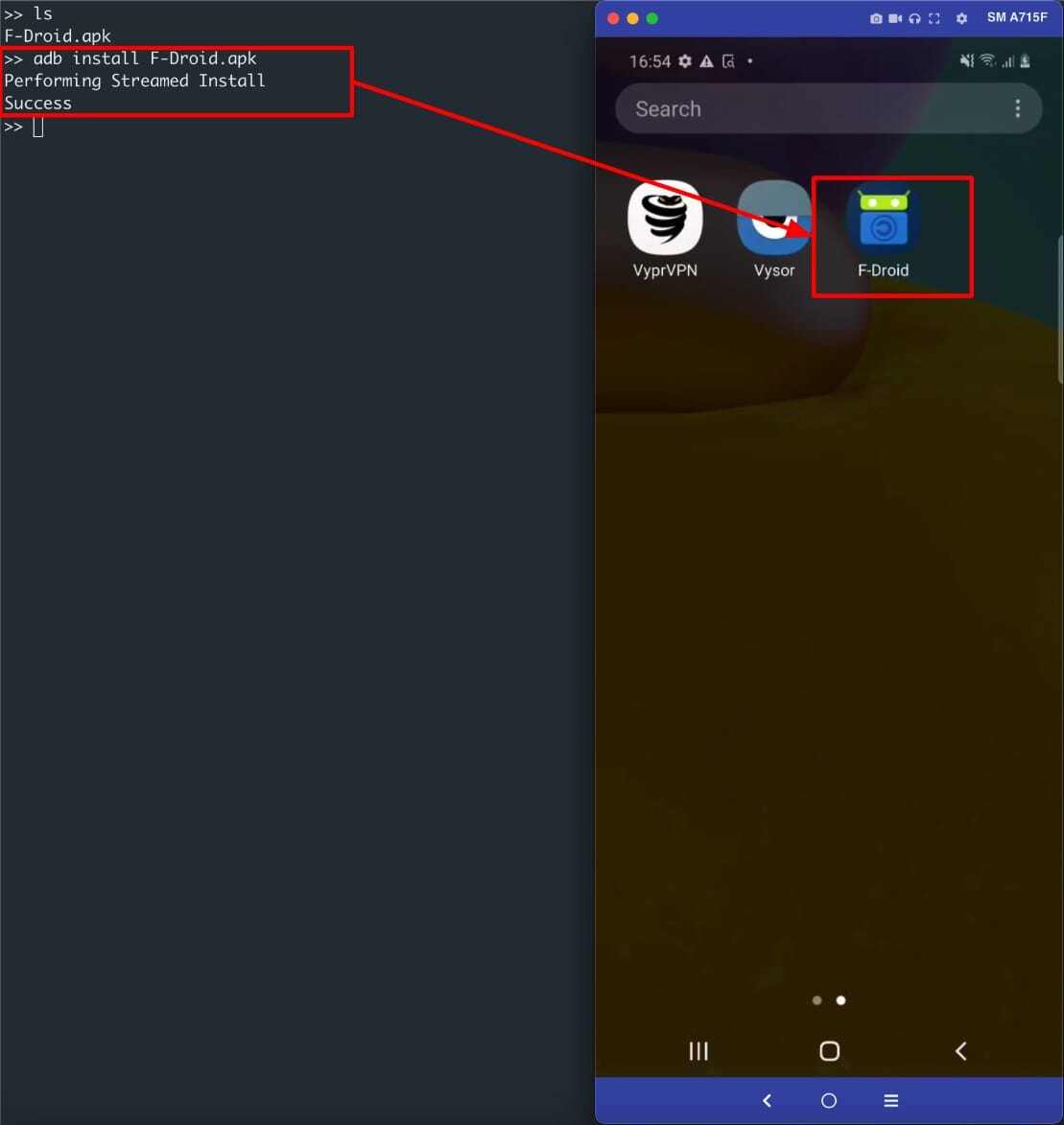
The second method involves using a third party app that requests the REQUEST_INSTALL_PACKAGE permission. The most common apps in this category are browsers, file managers and non official third party app stores. An example of this process is shown in the following figure.

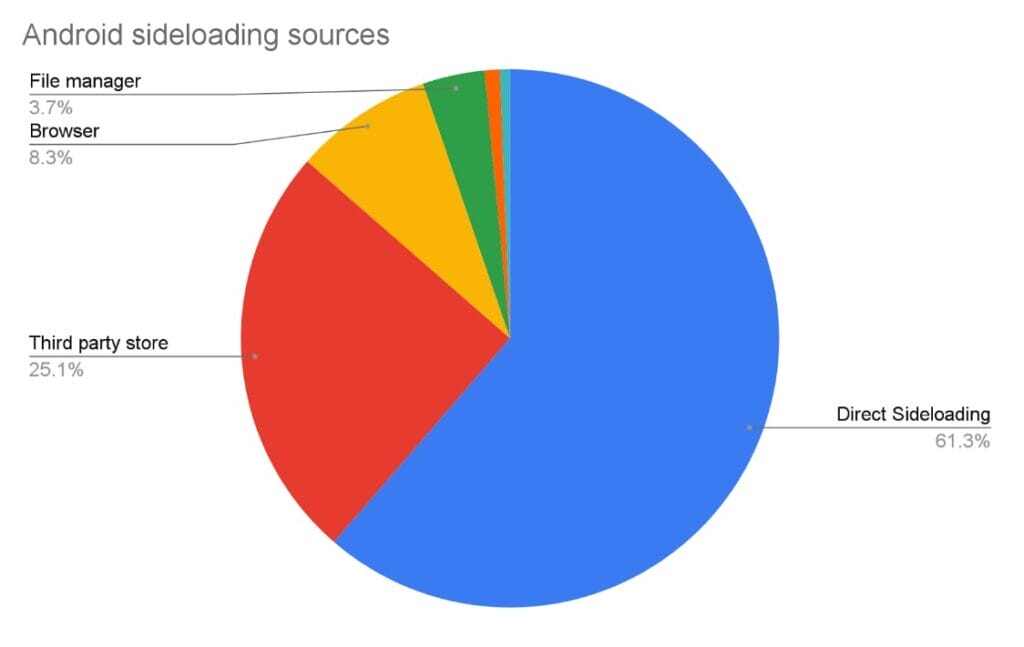
The most common sideloading method on Android is direct sideloading, followed by third-party stores and browsers, as seen in the chart below.
iOS
In order to comply with the European Union regulations, starting March 2024, Apple has had to allow third-party app stores for the EU. Despite having a set of safeguards on how these app stores are set up, the applications offered will not have the same level of scrutiny as those obtained from the official app store. This reduces user friction and opens the door to similar risks Android users are exposed to when sideloading.
Some examples of recently released third-party App Stores are:
An additional but limited “sideloading” method is the installation and authorization of an application with its associated Developer Certificate. This method is more common during application development and testing and is also used during a limited beta release cycle of known and trusted devices.
Prior to Apple officially supporting the use of third-party app stores, device owners used unofficial and very risky methods, such as jailbreaking the device or installing risky configuration profiles to bypass the Apple notarization process, to install applications outside of the official Apple App Store.
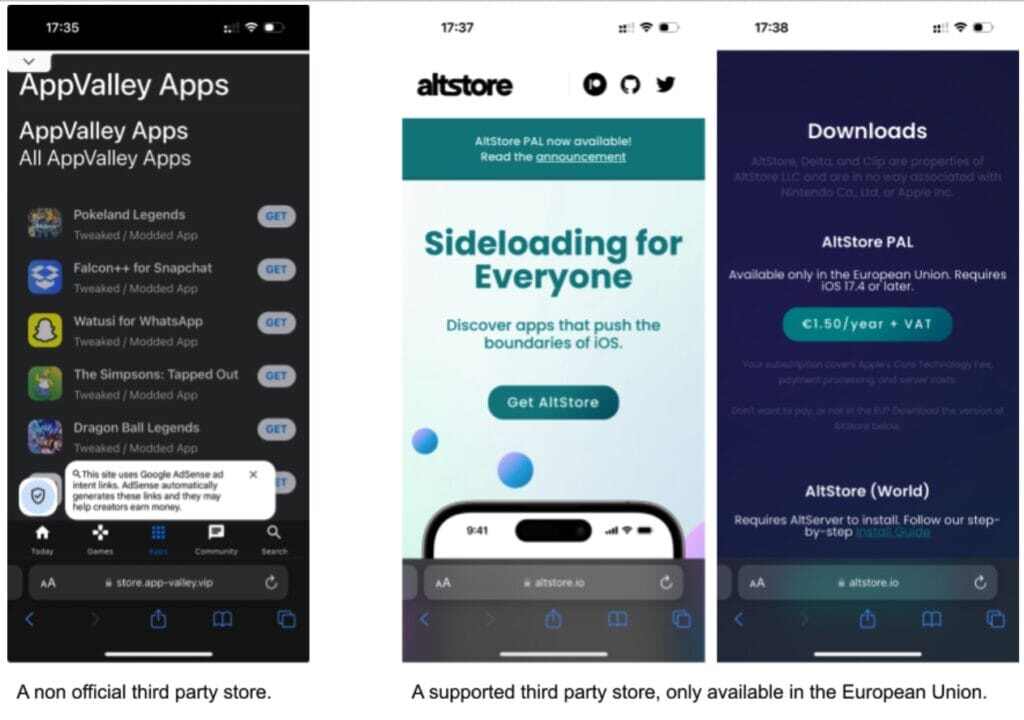
In the images below, we highlight examples of both official and unofficial third party app stores. On the left, installing an app from an unofficial third-party app store on a jailbroken device. On the right installing from a supported third-party app store.
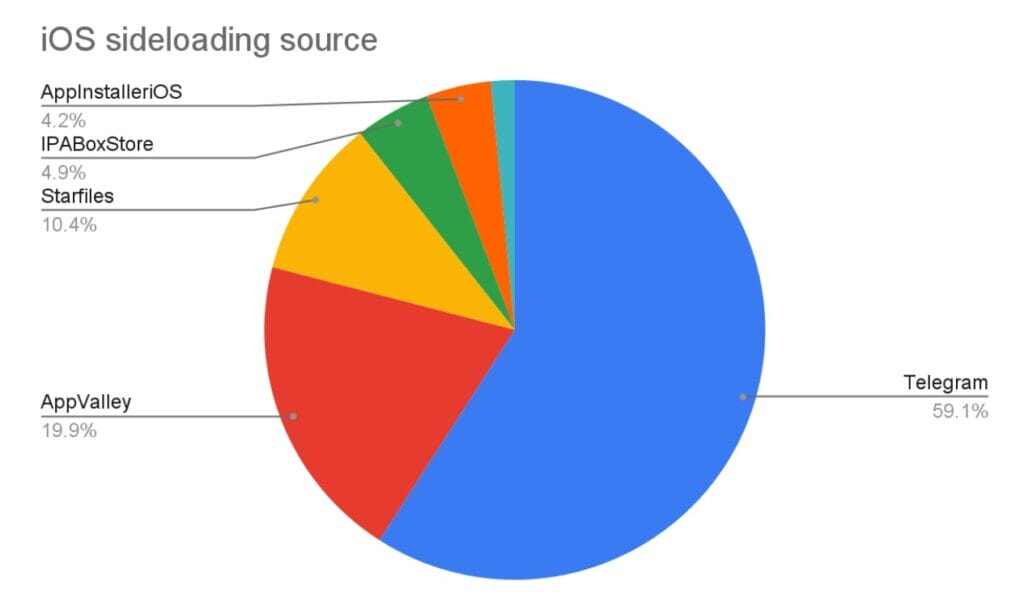
Looking into our global threat intelligence data, Telegram is the largest third-party source for “sideloading” iOS applications. Several channels distribute fake, modified, or cracked apps. The most popular unofficial third-party app store on iOS is AppValley.
The risks of sideloading
As we mentioned, sideloading an application is when a device owner installs an application from outside of the official app stores. This means the device owner is consciously and knowingly configuring their device to bypass the operating system’s safeguards put in place to protect the user and device. While sideloading offers access to a wider range of applications, it comes with significant risks, the most critical being potential exposure to malware since no vetting process is enforced on the installed apps.
Official app stores pour significant resources into the application vetting process, hoping to mitigate the introduction of risky or malicious applications being added into the app ecosystem. But when these safeguards are bypassed we significantly elevate the risk posture of the device, exposing the device to malicious applications, and more importantly, the device being fully compromised, which could mean a remote attacker gaining complete control of the device, accessing the user’s sensitive information, or impersonating the user to gain access to a bank account or other sensitive systems, to name a few of the potential risks.
The worst-case scenario of sideloading is that the device could be completely compromised, meaning a remote attacker could gain complete control of the device, gain access to the user’s sensitive information, or impersonate the user to access a bank account or other sensitive systems.
The following attack chains on Android show real examples of devices being tampered with after an app was sideloaded. In these cases, sideloading an application can be considered the first step of the attack chain. However, the real chain often begins months before, when users enable settings that make devices more vulnerable (such as developer options, USB debugging, and installing from third-party sources).
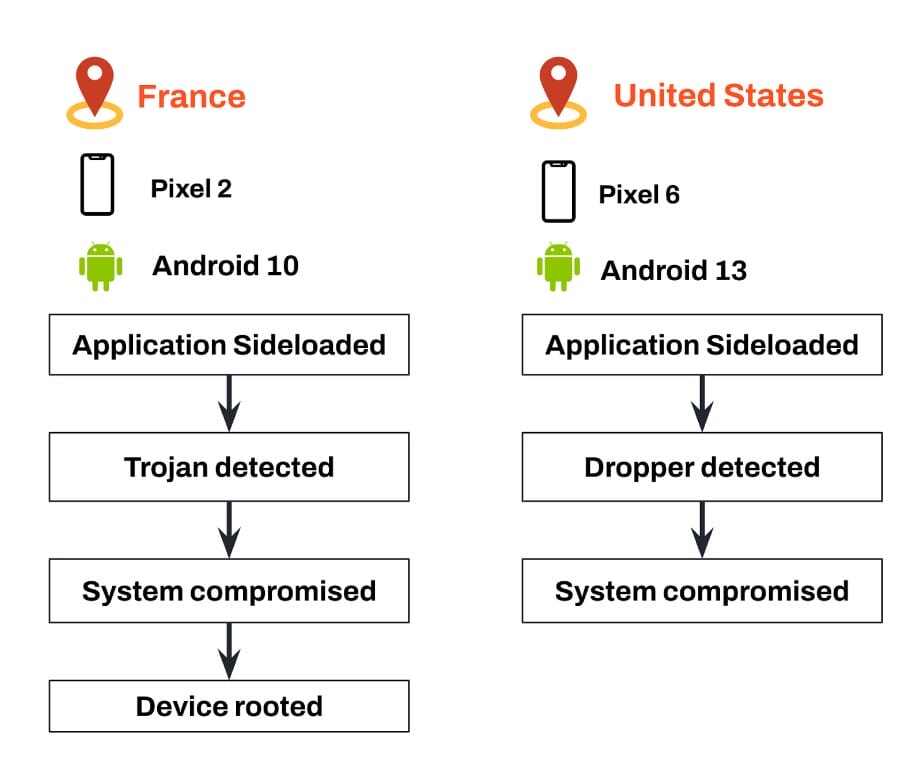
The chain on the left shows a Google Pixel 2 device running Android 10 that installs an app containing a trojan. After a couple of minutes, indications of the device being fully compromised (including a rooting detection) are detected. The detected modifications cannot happen without a user running with elevated privileges.
In the chain on the right, a similar attack chain is shown but on a Pixel 6 device running Android 13 that sideloads an app that contains a dropper. Droppers can get payloads from C&C servers that can contain exploits. In this case, after the detection of the dropper a full compromise of the device is detected.
On iOS, the landscape is not that different. Apps distributed through unofficial channels are known for repackaging apps, usually injecting libraries to perform different types of fraud and data exfiltration. At the same time, these libraries can contain exploits that are able to compromise the device fully.
Most frequently sideloaded malware
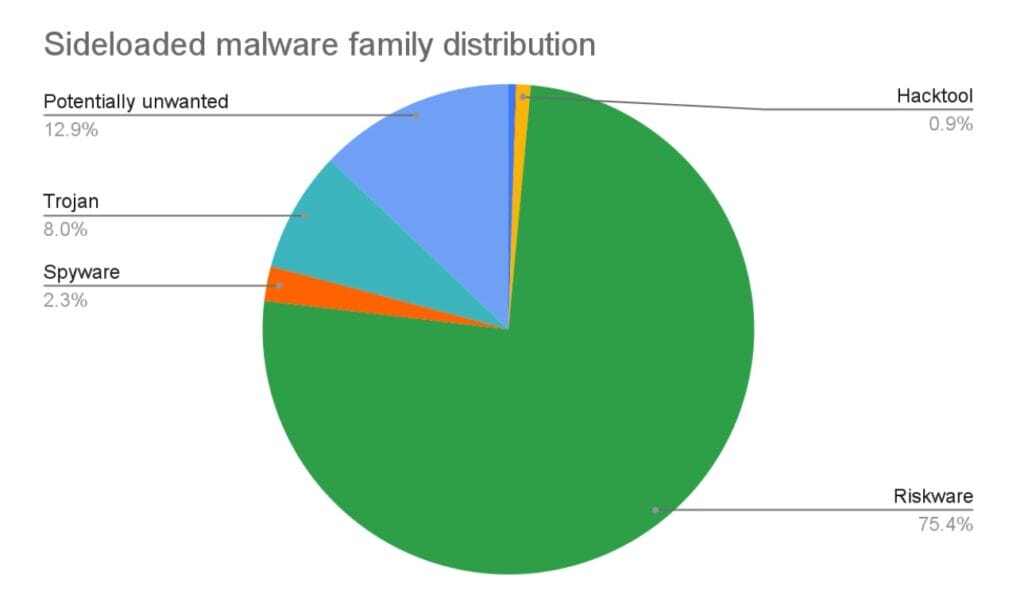
The most common malware families found in sideloaded apps are:
- Riskware: Software that may pose a risk to the device’s security or privacy, often bundled with legitimate applications but capable of exposing the device to vulnerabilities (e.g., remote administration tools (RATs) that allow someone to control a mobile device remotely).
- Spyware: Software designed to secretly monitor and gather information about a user’s activities and personal data without their consent, potentially compromising their privacy and security (e.g., keyloggers that record everything a user types, including passwords and personal messages).
- Trojan: Malicious software that disguises itself as legitimate or harmless to trick users into installing it, enabling unauthorized access, data theft, or further malware installation once executed (e.g., a fake antivirus program that claims to scan for threats but actually installs malicious software). A particularly risky type of trojan is banker trojans, which are used to steal banking information and have the capability to harm both end users and banking institutions.
- Hacktool: Software tools used to exploit vulnerabilities in systems, networks, or applications, often aiding hackers in bypassing security measures, cracking passwords, or performing other malicious activities (e.g., password crackers that use brute force methods to break into accounts).
- Potentially unwanted applications: Applications that, while not directly harmful, may present unwanted behavior (e.g., cryptocurrency miners, excessive advertisement).
Based on threat data, the distribution of sideloaded malware is the one shown in the figure below.
Unknown threats
To assess the industry coverage of malicious applications that rely on sideloading for distribution, we extracted all unique hashes of apps that satisfy these conditions in our threat data and used widely used application repositories to check what other vendors’ assessments were. The results were surprising. We found that 56% of the samples had never been seen by the industry, showing that most of the threats we found are unknown to the industry.
This could be explained by the fact that malware developers who plan to use official distribution channels use these online analysis services to assess whether their malicious samples would be detected by specific engines. If the app is intended for sideloading, there is no need to go through the app vetting process, which also means that there is no need to upload the sample to online scanning services.
This highlights the importance of having on-device zero-day malware detection. Relying on heuristics to detect known malware exposes the user to substantial risk.
What can Zimperium do to mitigate the risk?
As we have shown, sideloading applications poses a security risk to the device owner, app teams, and, most importantly, to the enterprise itself. Untrusted and unvetted applications introduce a variety of unwanted security risks for enterprises but can easily be avoided if monitored and controlled properly. Ignoring the risks is not an option. That is why it is important to take proactive measures to understand your risk exposure and to protect your device assets and the sensitive information associated with it.
Zimperium Mobile Threat Defense (MTD) is a comprehensive mobile security solution designed to secure both corporate-owned and bring-your-own devices from advanced mobile threats across various vectors, including device, network, phishing, and app risks, as well as malware vectors. Zimperium’s security solution employs a comprehensive set of Enterprise-grade features to understand their risk posture across their mobile fleet, protect against the evolving mobile threat landscape, and incorporate mitigation actions to safely address the risks associated with sideloading of applications.
Below are a few examples that will help you understand Zimperium’s breadth of visibility and control capabilities when it comes to the risks associated with sideloading:
Device Risk Posture: Continuous assessment of the device’s risk posture by monitoring critical configuration settings and device integrity health metrics. Zimperium has over 20 unique threat types to help Enterprises understand and protect the device from risky or malicious intent from “sideloading” applications. A few examples of how Enterprise can understand the risk(s) are:
- Has Developer Options been enabled on the device?
- Has Unknown Sources been enabled?
- Does the device have any unknown risky, or untrusted Profiles installed?
- Is the device compromised?
- What is the current integrity state of the device?
- Has adb been enabled and have the files and commands been evaluated?
Network-based Detection & Prevention: Continuous assessment of the state and safety of the connected networks (e.g Man-in-the-Middle, Rogue Access Points, etc.) and access prevention to risky sites hosting unofficial applications.
- Blocking (and alerting) access to risky sites hosting unofficial or risky applications, including Zimperium-specific curated list of 3rd party app stores.
- Invoking network prevention mitigation actions to prevent malicious actions such as C&C interaction and/or data leakage stemming from a risky or malicious application being “sideloaded” onto a device.
- Is the device connected to a safe and trusted network?
Application-borne Threats: Continuous assessment and visibility of application-borne threats and risks, using Zimperium’s patented On-Device Dynamic Detection Engine.
- Are the applications installed on the device safe?
- Where did the applications and how did the application get installed?
- What can this application do and what are the risks?
Advanced App Vetting: Deep app analytics using Zimperium’s comprehensive App Vetting services to expose the composition, as well as the dynamic exposure of an application, including applications sourced outside of the official app stores.
- Is the Developer and certificate that signed applications a trusted source?
- Does the application expose sensitive data insecurely?
- Is the application using outdated or vulnerable software libraries?
- Where does the application send data to?
- Does the application basic industry compliance standards
- Where is this application hosted?
- What Permissions are available and do they fit the intent of the application?
To learn more about Zimperium’s comprehensive mobile threat detection solution stack contact us today.


