Apple has released iOS 9 with a large number of security fixes. Zimperium recommends that iOS users install the latest iOS update.
There are 60+ vulnerabilities present in iOS 8.x that are fixed in the upgrade to iOS 9. The vulnerabilities include the ones that are exploitable remotely and locally. Impacted devices include the iPhone 4s, 5th Generation iPods, and iPad 2’s and newer.
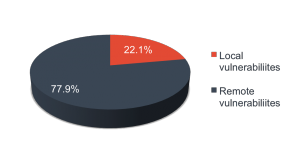
Local attacks
Local attackers can do significant damage when in possession of an iOS device. Attackers are able to get unlimited attempts to brute force the device lock code by resetting the attempt limit – something that can be achieved restoring from a backup.
A significant amount of sensitive OS and user specific information can be acquired by attackers. These include password information, private keys, and visited websites. Local attackers are also able to execute arbitrary code, some with system level privileges.
Remote Attacks
Attackers without physical control of iOS devices have the ability to steal information and execute code. Remote attacks range from the creation of malicious cookies to leaking sensitive information.
Nearly a quarter of the vulnerabilities patched in iOS 9 were exploitable by local attackers.
App User Interface Spooling
A small number of vulnerabilities can allow an attacker to spoof the User Interface of legitimate apps and websites. This could allow the attacker to pose as a legitimate app to fool the user into providing sensitive information(e.g. passwords, usernames, credit card numbers).
Information Leakage
Attackers can gain information on OS structures and memory layout to aid in further exploit development.
Much of the information leakage is only accessible to local attackers, making them a bit harder for an attacker to exploit. This also makes them much more effective when a successful exploit is created.
Privacy Leaks
User privacy is compromised by a group of vulnerabilities. The attacks vary from local attacks to remote or network attacks. Attackers can query Siri for notifications on locked devices. They can also respond to audio messages.
Visiting a malicious website can lead to code execution or simply steal browsing history and network activity.
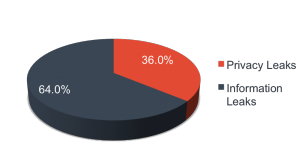
The patched vulnerabilities leaked both personal and system information.
Arbitrary code execution with System or Kernel privileges
Attackers have a number of vulnerabilities that can be exploited to execute code on iOS devices. An attacker able to execute code as a regular user on a device is troublesome, more so when they can escalate privileges and gain root level access.
Loading a crafted font or text file can result in a local attacker running arbitrary code. An attacker can also use a crafted app to gain System level privileges. Malicious apps count for some of the successful attacks that lead to attackers getting their code running on iOS devices.
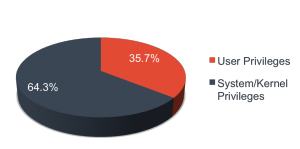
Attackers can execute arbitrary code on iOS devices, but some vulnerabilities will give system or kernel privileges.
iOS 9 update fixes multiple vulnerabilities
Zimperium highly recommends that iOS users update all potentially affected devices to iOS 9. Numerous vulnerabilities that could lead to arbitrary code execution and/or the leaking of sensitive information have been patched.
Follow @Zimperium, @zLabs