The ownership and use of smartphones has grown increasingly ubiquitous. By 2021, the percentage of adults in the U.S. who owned a smartphone grew to 85%1. Between 2010 and 2021, the smartphone market grew from $18 billion to $73 billion.2
Whether we’re looking to stay informed, connected, or entertained, our smartphones are increasingly the tool of choice. Now, the same is true for when we’re looking to get work done—and this is a trend many security teams are still grappling to contend with.
We’ve recently published our 2022 Global Mobile Threat Report, which offers some key insights into the challenges today’s security teams are confronting. This report offers a comprehensive look at the mobile endpoint security landscape, and it specifically examines how the explosive growth in remote and hybrid work in recent years has led to increased reliance on mobile devices—and dramatic expansion in risk.
How Remote Work Has Changed the Game for Security Teams
Now, remote workers routinely use their own networks and their own devices in the course of their jobs. Incorporating BYOD policies have fundamentally changed the game in terms of which security tools and strategies work—and which do not.
In a recent survey, 44% of survey respondents say they have added security policies or requirements as a direct result of cyber security incidents associated with their distributed employee base. Of that group, 34% have switched security vendors or service providers.3
In response to the threats posed by remote and hybrid work, many teams have started to implement cybersecurity best practices. However, a large percentage of organizations have yet to make this move.
The Exposure Posed by BYOD
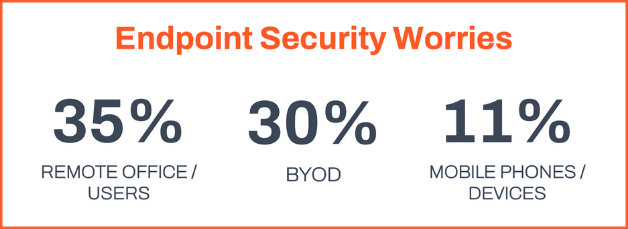
To respond to the pandemic and the need to foster the productivity of remote workers, IT organizations have scrambled to build and expand support for bring-your-own-device (BYOD) policies. 30% of respondents in a survey cited BYOD as a top concern for endpoint security. Further, this concern is proving to be justified: In 2021, nearly 50% of respondents indicated that their work-from-home strategy played a significant role in cybersecurity incidents.
When it comes to vectors of attack, Microsoft Office represents the primary target of cybercriminals. One report indicated this software suite accounted for more than 72% of exploits, while browsers were responsible for 13%.4 For enterprise security teams, the takeaway is clear: More than any other apps or tools, Office is the target of choice for cybercriminals looking to gain access to corporate data by monitoring email accounts and communications occurring via the Microsoft Teams app. Mitigating the exposure these apps present is a key imperative.
Emerging iOS Threats
As BYO device usage increases in the workforce, keeping up with the ever-evolving threat landscape is essential. For some, the fact that Apple iOS devices are commonly being targeted for attacks may come as a surprise. In recent years, many had the perception that it was largely Android devices that were being successfully targeted. In 2021, iOS vulnerabilities accounted for 64% of the mobile-specific zero-day attacks discovered. That year, 11 separate zero-day exploits targeting iOS and Apple WebKit were found.5
In addition, iOS devices were at the center of one of the spyware attacks that gained the most notoriety in 2021. First discovered in 2016, Pegasus spyware reappeared in the news. Attackers used Pegasus in a campaign that targeted 50,000 journalists, activists, political leaders, and others. Initially uncovered by Amnesty International, the spyware campaign featured zero-day exploits targeting iOS devices.
In years past, the closed nature of Apple’s App Store helped stem the proliferation of malicious apps on iOS devices. However, attackers are leveraging workarounds. For example, Apple offers configuration profiles that give legitimate businesses the ability to install and run applications, such as mobile device management solutions, without the scrutiny of Apple’s App Store submission process.
However, this feature also allows end-users to load unapproved and often unsecured apps. Third-party app stores and app signing services have started to emerge that are capitalizing on this workaround, which poses the threat of increased malware ultimately making its way onto unsuspecting users’ devices.
Endpoints Creating Blind Spots
Mobile endpoints represent an increasingly prominent target for cybercriminals. The reality today is that every time an employee uses a mobile device to open an email, send a text, or access a corporate application, it can pose a threat to the enterprise, potentially exposing personally identifiable information, intellectual property, and more.
However, if teams in the security operations center are relying on traditional endpoint security tools, this constant activity isn’t being tracked consistently and effectively, if it’s tracked at all. A significant percentage are clear this lack of visibility poses a problem: 39% say that, with their existing tools and procedures, reaction time is too slow.6
These realities make clear that comprehensive mobile threat defense (MTD) solutions represent an urgent requirement. With advanced MTD offerings, teams can establish effective defenses against modern-day mobile threats, protecting against attacks at the device, network, and application level. Further, MTD solutions can protect end-users against phishing attacks that target such vectors as SMS text messages, messaging apps, personal email, and corporate email.
Conclusion
The insights above give you a glimpse of the extensive findings reported in the 2022 Global Mobile Threat Report. The report makes one thing abundantly clear: The mobile device has become a common target for malicious actors globally. Whether through device exploits, application misconfigurations, malware, or leaky databases, cybercriminals are succeeding in exploiting mobile devices and gaining access to sensitive personal and corporate assets.
Establishing robust, adaptive, and persistent mobile endpoint security is therefore a primary objective. Be sure to review this year’s report, which features expert analysis of mobile threat data from the field, including prominent attack vectors, regional trends, evolving vulnerabilities, phishing developments, and malware advancements. To learn more about mobile security threats and how to guard against them, download the 2022 Global Mobile Threat Report.
- Statista, “Percentage of U.S. adults who own a smartphone from 2011 to 2021,” April 2021, https://www.statista.com/statistics/219865/percentage-of-us-adults-who-own-a-smartphone/
- O’Dea, S., Statista, “Smartphones in the U.S. – Statistics & Facts,” August 4, 2021, https://www.statista.com/topics/2711/us-smartphone-market/#dossierKeyfigures
- Zimperium, Pulse QA, “How have you shifted your remote work strategy as an organization as a result of cybersecurity incidents in the past year?” 2021
- Chebyshev, V., Securelist, “IT threat evolution Q3 2019. Statistics,” April 28, 2021, https://securelist.com/it-threat-evolution-q3-2019-statistics/95269/
- Google Project Zero, 0day “In the Wild,” Google Docs, 2021, https://docs.google.com/spreadsheets/u/1/d/1lkNJ0uQwbeC1ZTRrxdtuPLCIl7mlUreoKfSIgajnSyY/edit#gid=2129022708
- Zimperium, Pulse QA, “Secure Access Practices In North America,” 2021