A Tale of Two Phishes: Lessons From The Twilio and Cloudflare SMS Spear Phishing Attacks
As details emerge surrounding the spear phishing attacks against Twilio and Cloudflare, it remains clear how enterprises must continuously evolve their access security policies to stand up against sophisticated attackers. Despite being carried out by the same malicious actor, these two attacks paint very different pictures, as one organization fell victim while the other did not.
On August 4th, the customer engagement company, Twilio revealed multiple of their employees had credentials stolen through a sophisticated SMS-based spear phishing attack. As a result, this led to malicious actors gaining access to their internal data systems. The messages sent via text to the unsuspecting victims were no different than what many organizations see every day, notifying the employee their password needed to be reset and providing a link. However, these threat actors brought a unique level of social engineering not often seen by matching employees’ names to their phone numbers.

Unfortunately for Twilio, after the credentials of multiple employees were compromised, the attackers were able to gain access to their critical systems. The attackers then accessed the data of Twilio customers. While the company is reporting around 125 customers’ data was breached, the attack set off a chain of events that led to the end-to-end encrypted messaging service Signal disclosing roughly 1,900 users’ info. Signal, a customer of Twilio, is currently in the process of alerting all impacted customers.
On August 9, content delivery network and DDoS mitigation company Cloudflare reported they too had been targeted by the same spearphishing attack. This attempted attack had taken place earlier this year on July 20th. But, unlike Twilio, Cloudflare’s use of physical FIDO2-compliant security keys prevented any compromised credentials from being used to access data systems. In the span of one minute, over 100 Cloudflare employees received similar text social engineering messages, citing the need to click a link to take action. When prompted to log in, the employees supplied their credentials to the attackers, who were unable to use them due to the increased security procedures around access.
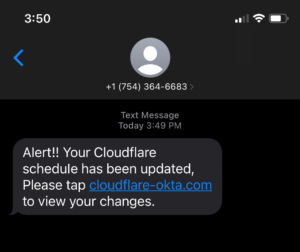
The Cloudflare Security team received reports of the attempted attacks and were able to analyze the threat to their systems and work with outside services for takedowns of the threat to their employees and data. Within 45 minutes of the attack, all compromised employee credentials were reset.
The stories of Twilio and Cloudflare are very different, but both paint a bleak picture of the modern reality of enterprise security infrastructure and the inclusion of advanced mobile security systems. The keys to the proverbial kingdoms in both of these situations are mobile endpoints far outside the traditional security protections of enterprises.
So What Can We Learn From Both SMS Spear Phishing Attacks?
Security Training Only Goes So Far: Whether they are Bring Your Own Device (BYOD) or corporate-owned, these mobile devices are in the hands of employees who, despite security training, still fell victim to convincing spearphishing attacks. Specially crafted spearphishing attacks with legitimate landing pages brought credibility to these attacks. The malicious actors were organized and methodical, using US-based phone numbers and attaching names to the text messages to their targeted victims. The attackers did their homework, collected intel on their intended victims, and struck in unison in hopes of at least one person falling for the trick. Unfortunately, in both cases, they successfully tricked multiple employees.
Phishing is OS-Agnostic: By using SMS-based communications, these attackers were able to target both Android and iOS devices directly. Phishing is agnostic to operating systems, relying on human error for a successful attack, and in the case of mobile phishing, the added element of small screens, limited OEM-provided security, and distracted users increases the chances of a successful attack. Once the phishing URL is delivered, all it takes is one user to click and submit their credentials for enterprise systems to be at risk. And according to our research, mobile-specific and friendly phishing websites account for 75% of all phishing attacks.
Mobile is Just One Component of Cyber Attacks: Well-planned cyber attacks are a lot like dominoes in a row; each piece falling leads to the next piece falling. Twilio and Cloudflare both failed to secure the mobile component of their attack surface, enabling the attackers to deceive multiple employees into giving up credentials. In the case of these attacks, it started with intelligence gathering of existing employees and services, which led to communications and landing pages being created mimicking legitimate assets. From there, the spear phishing attack leads to compromised credentials, then to enterprise system access (for Twilio). Each piece in the attack chain fell into place, with mobile being the largest addressable component left unprotected.
Conclusion: The Need for Mobile Threat Defense to Secure Mobile Endpoints
Cloudflare’s saving grace in this attack was their reliance on physical security keys for employee access, but this layer of security is not adopted universally across enterprises. These days, many enterprises have moved from physical keys to multi-factor authentication (MFA) services that rely on smartphones and apps. But the devices are still left unprotected in more instances than not, and security teams lack critical visibility into the threats targeting the mobile endpoints as part of larger attack chains. Whether as part of zero-trust plays or advanced security insights, the mobile devices used by employees to access any layer of enterprise data are increasingly under attack by malicious actors.
From identity verification, communication tools, and even critical data access, enterprises increasingly rely on their employees’ access to mobile endpoints to be productive in the modern distributed workforce. And each mobile device, whether BYOD or corporate-owned, increases the enterprise attack surface beyond what many security teams are able to monitor and respond to. Mobile device management is no longer enough and is unable to detect the advanced attacks used today against employees.
Unlike Twilio, Cloudflare was prepared AND lucky. But both still had employee devices fall victim to similar attacks. This does not need to be the reality for enterprises. With advanced mobile threat defense capabilities, organizations have the ability to secure against even the most advanced attacks on the device while also providing critical data to security teams to stay ahead of increasingly organized cyber attacks. From phishing to network threats, malicious applications to compromised devices, it’s critical for enterprises to acknowledge that the mobile attack surface is the largest unprotected vector to their data and access.


