By: Zuk Avraham, Joshua Drake, Yaniv Karta, Jimmy Shah
(To download the detailed report, click here)
Recently, Verizon published a report that says that malware on mobile is not an issue.
We strongly suggest Verizon and other enterprises not underestimate the scale of one percent. The sheer number of mobile devices deployed mean that one percent is a huge number. Attacks against the users within this one percent could be the first foothold of attacks like those we saw against Sony and can lead to an advanced attack on every single Fortune 500 company.
First, let’s examine the core problems with Verizon’s report.
Verizon looks at Apps as the sole vector of attacks . The company claims that there are not enough statistics that allow detection on iOS devices and therefore notes that Android has more attacks than iOS. While it may be easier to attack Android devices through Apps, it is not the case for targeted attacks where both OS are likely to get targeted.
. The company claims that there are not enough statistics that allow detection on iOS devices and therefore notes that Android has more attacks than iOS. While it may be easier to attack Android devices through Apps, it is not the case for targeted attacks where both OS are likely to get targeted.
There is no mention of Network attacks (MITM, etc.) of any kind. There are two references to USB, but they are not descriptive.
1) Android and iOS Sandboxes Impact Protection, for the Good and Bad
 Sandboxes, which are similar in architecture for Android and iOS, restrict app-to-app interaction, thereby blinding traditional security apps. The best such security apps can do is check for known signatures of other apps and focus on ‘find/lock my phone’ features.
Sandboxes, which are similar in architecture for Android and iOS, restrict app-to-app interaction, thereby blinding traditional security apps. The best such security apps can do is check for known signatures of other apps and focus on ‘find/lock my phone’ features.
2) Lack of Permissions
 Unlike desktops, mobile devices do not allow root access for security purpose. If a security device were to go the ‘Deep Packet Inspection’ (DPI) route, this approach impacts the battery life. The traditional approaches to security do not work well in the mobile environment.
Unlike desktops, mobile devices do not allow root access for security purpose. If a security device were to go the ‘Deep Packet Inspection’ (DPI) route, this approach impacts the battery life. The traditional approaches to security do not work well in the mobile environment.
3) Targeted Attacks
 Most enterprises are subject to targeted attacks, which involves exploiting a vulnerability in client-side browser or document reader. As the communication between email clients and servers are encrypted, Verizon has almost no visibility on the cellular network side to detect spear-phishing attacks.
Most enterprises are subject to targeted attacks, which involves exploiting a vulnerability in client-side browser or document reader. As the communication between email clients and servers are encrypted, Verizon has almost no visibility on the cellular network side to detect spear-phishing attacks.
4) No Visibility to Time-Bombs
 The limitation of most security solutions is that they do not monitor an app continuously. Attackers have ways to pretend as clean app until security solution monitoring is off their back. This evasion technique can prevent Verizon, as well as security vendors, from ever seeing what’s happening in other Apps (different sandboxes). They won’t even be able to tell if the device is under attack or not.
The limitation of most security solutions is that they do not monitor an app continuously. Attackers have ways to pretend as clean app until security solution monitoring is off their back. This evasion technique can prevent Verizon, as well as security vendors, from ever seeing what’s happening in other Apps (different sandboxes). They won’t even be able to tell if the device is under attack or not.
5) Mobile Attack Vectors > Apps
 PCs or charging stations can access folders that an on-device malware scanner can’t even see, (an attack named “Juice-jacking”). Security vendors that are using traditional security approach do not have access to all areas of iOS and Android devices.
PCs or charging stations can access folders that an on-device malware scanner can’t even see, (an attack named “Juice-jacking”). Security vendors that are using traditional security approach do not have access to all areas of iOS and Android devices.
WHAT OUR DATA SHOWS:
We examined these attacks on a subset of our business users and used over 200,000 business devices out of millions of licensed devices of our Enterprise Mobile Security solution. The numbers are quite disturbing. Out of the hundreds of communication providers in United States, we focused on the total sum of attacks on Verizon and AT&T.
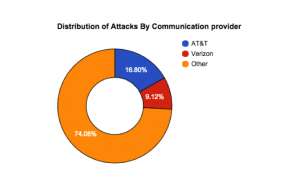
 a.) Out of all communications providers in US, Verizon and AT&T account for 25.92% of all attacks. Out of all attacks that happened when the user was connected to cellular networks, Verizon and AT&T accounted for 31.98%.
a.) Out of all communications providers in US, Verizon and AT&T account for 25.92% of all attacks. Out of all attacks that happened when the user was connected to cellular networks, Verizon and AT&T accounted for 31.98%.
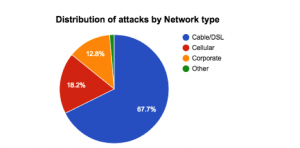
b.) Of the total attacks, 18.2% happened on 3G/4G networks, on which Verizon and other carriers have better, yet still limited visibility
In conclusion, we think Verizon’s reporting on mobile attacks leaves much to be desired. A wide variety of attacks are happening. However, detecting them requires a variety of approaches. Even by using next generation methodologies, some attacks are still very difficult or impossible to detect. If you are interested, we are happy to speak with you and quickly show a few examples of attacks that can not be detected due to smartphone architecture and permission model. You might want to take us up on that offer before someone else, with malicious intent, does.
Zimperium’s detailed Threat Intelligence report can be downloaded below.
If you would like to get visibility into attacks that are happening in your organization, either through BYO devices or Corporate owned devices, request a demo of our products at www.zimperium.com/request-demo


