White-Box Cryptography: The Key to Safeguarding Sensitive Data in Mobile Applications
Nowadays sensitive information is constantly at risk of being compromised. Cryptography is routinely used to ensure data integrity and confidentiality. Yet, cryptographic protection is only as strong as the security of the used cryptographic keys. If the cryptographic keys are exposed then the encrypted data can be decrypted and digital signatures can be forged.
Traditionally it was assumed that the device on which cryptography is used is secure and one has to only worry about the data while it is in transit or while it is stored. It is no longer a valid assumption now when attackers can find ways to infiltrate our mobile devices, laptops, and even specialized hardware devices. In many cases, attackers can have full control over the device that uses cryptography. They can see every byte of memory at every moment and can control code execution instruction by instruction.
There are many popular apps that leverage cryptography when running on insecure mobile devices, for example:
- Media streaming apps for playing protected content that is decrypted on the device
- Apps that allow making and receiving card payments that encrypt the card PIN and other sensitive data on the device
- Apps that authenticate themselves with embedded medical devices, cars, or IoT devices by performing encryption and signature operations
How do these apps work without exposing the cryptographic keys used?
Enter white-box cryptography!
White-box cryptography is a set of techniques and algorithms that are used to transform the traditional encryption algorithms and the corresponding cryptographic keys to execute securely in compromised environments. Even when attackers control the device running cryptographic operations, white-box cryptography protects the keys.
It is important to note that white-box cryptography does not rely on any specific cryptographic hardware on the device for the protection of keys. Mathematical techniques such as homomorphic encryption are combined with code obfuscation and run-time protection to achieve the protection entirely in software, thus making the implementation portable and universal.
To help us understand how this is at all possible, here is a simplified example of protecting data that is used on an insecure device.
Let’s assume we want to add two numbers but we don’t want to reveal the numbers to an attacker who can observe everything on our insecure device. If we just send the numbers to the device, the attacker will see the numbers and the result:
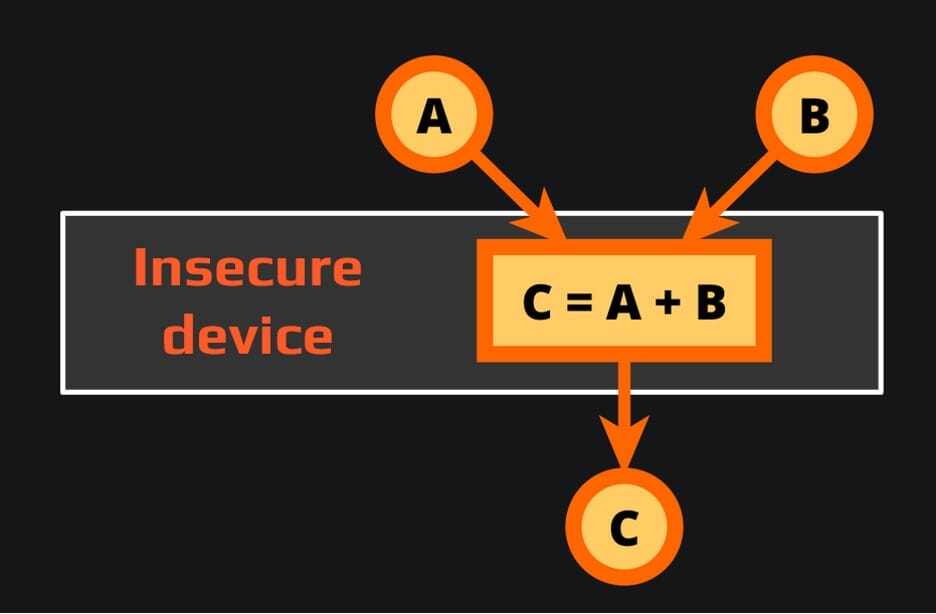
To protect our input, in this case we can add random numbers to our inputs and send the “encrypted” values to the device. Because we used the same operation (addition) for “encrypting” our inputs as is used for processing them, the device can simply add the inputs and return the result to us. Because we know the random numbers that we added to the inputs, we can now recover the real result by subtracting them from the returned result. The attacker, however, does not know the random numbers, so they cannot learn the inputs and the result.
This technique is a simple example of white-box encryption. In real life the operations that need to be performed and protected are much more complex and mission critical. So advanced methods are used to keep the cryptographic keys secure while maintaining acceptable performance and size of the program.
The researchers at Zimperium have been working on techniques for processing protected data on insecure devices for more than 25 years – before there even was a term “white-box cryptography”. The result of this ongoing effort is our zKeyBox library.
The main features of zKeyBox are:
- Cryptographic keys are always protected, even while being used
- Static (hardcoded) and dynamic (acquired at run-time) keys are supported
- Support of many encryption, decryption, signing, verification, key agreement, key generation, and key derivation algorithms (AES, RSA, ECDSA, ECDH, HMAC, NIST AES Key Wrap, NIST SP 800-56C key derivation, and many more)
- Extensions, such as TLS, Secure Database, Secure PIN Entry, DUKPT, TR-31 key blocks, etc.
- Support of all popular mobile and desktop platforms and many specialized platforms
If you are looking to protect your cryptographic operations on insecure devices, consider using Zimperium’s zKeyBox to protect your static and dynamic keys at all times. It provides a uniform interface across all platforms, supports a wide range of cryptographic algorithms, and is independent of hardware security features.


