Authors: Nico Chiaravio & Gianluca Braga
The Hacker News recently published a story that discusses a joint communication among the German intelligence apparatus, the Federal Office for the Protection of the Constitution (BfV), and South Korea’s National Intelligence Service (NIS), warning readers about new tactics used by a North Korean threat actor called Kimsuky.
This actor, also known by Thalium and APT37, has been active since 2012 and has produced several campaigns using various techniques, from watering hole attacks to spear phishing and malware campaigns targeting different platforms, including Android and Chromium-based browsers. These techniques enabled the threat actor to access financial, personal, and client data. This organization was detected targeting Korean and German entities, and it’s believed that the main goal is to target government employees, military, manufacturing, academic, and the think tank of global diplomacy and security.
Kimsuky attacks demonstrate the level of coordination and sophistication involving a multi-step chain to achieve the ultimate goal. The latest campaign described uses different methods:
Method 1:
- Spear Phishing Attack: The campaign uses highly targeted emails to compromise either the ultimate victim or someone in their circle and use it to perform further spear phishing attacks. This step aims to trick the user into installing a browser extension.
- Malicious Browser Extension: This extension targets Chromium-based browsers, and its purpose is to steal the contents of the email account when the victim logs into their Gmail. For this, it uses developer tools API, which bypasses the security settings such as 2FA.
Method 2:
- The first step is similar to the example above and requires the attacker to get the user’s credentials.
- The attacker installs a malicious app on an Android device by exploiting Google’s play synchronization and internal testing feature. Then they upload a malicious application to Google Play Console that will automatically sync with the victim’s device.
Both methods are shown in Figures 1 and 2 below.
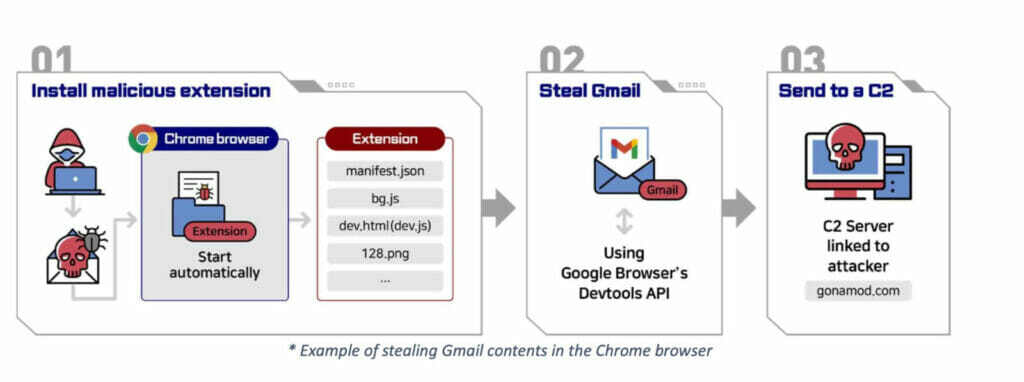
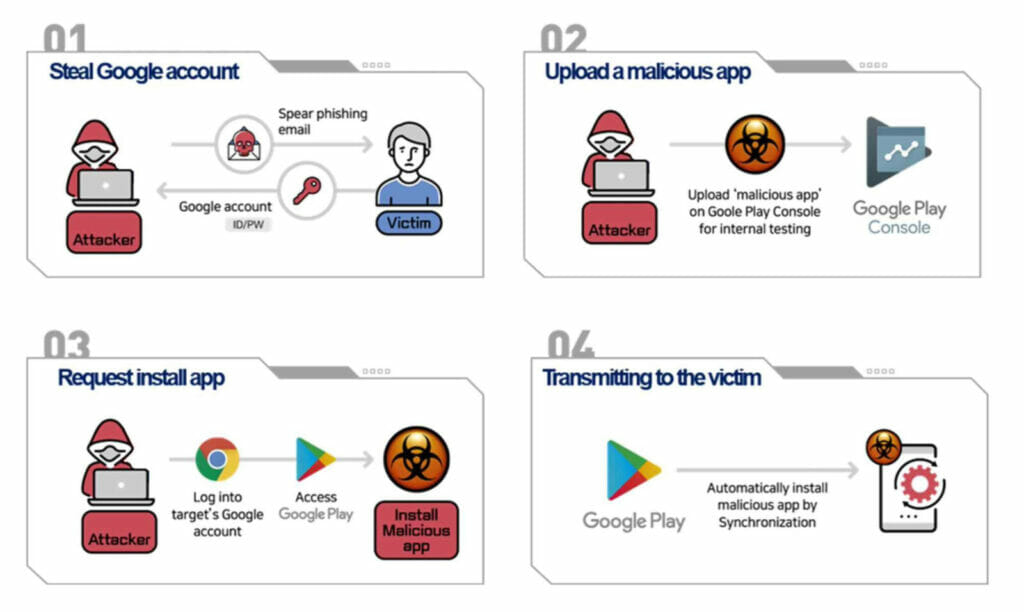
It is important to highlight that the apps used in this campaign are not available in the Google Play Store. These apps are distributed using a feature called “internal testing,” which allows the app developers to distribute their apps to a small group of users flagged as “trusted.” The number of trusted users is very limited, which shows that this campaign is highly targeted.
Zimperium Mobile Threat Defense (MTD) customers are protected against these threats. Our dynamic on-device threat detection engine provides protection against malicious apps installed with these methods In addition, Zimperium MTD protects browsers since the browser extensions are also flagged as malicious to our Chrome OS users. Last, Zimperium enhanced phishing detection can prevent phishing attacks from being successful, stopping the whole attack chain from the initial attack vector.
IOCs:
| Android applications | |
| 3458daa0dffdc3fbb5c931f25d7a1ec0 | FastViewer |
| 89f97e1d68e274b03bc40f6e06e2ba9a | Fastspy |
| 04bb7e1a0b4f830ed7d1377a394bc717 | Fastfire |
| C&Cs | |
| gonamod[.]com | |
| siekis[.]com | |
| navernnail[.]com | |
| lowerp.onlinewebshop[.]net | |
| mc.pzs[.]kr | |
| 23[.]102[.]122[.]16 |


