Scammers Used 265 Different Google Forms to Dupe Unsuspecting Users of Top Brands

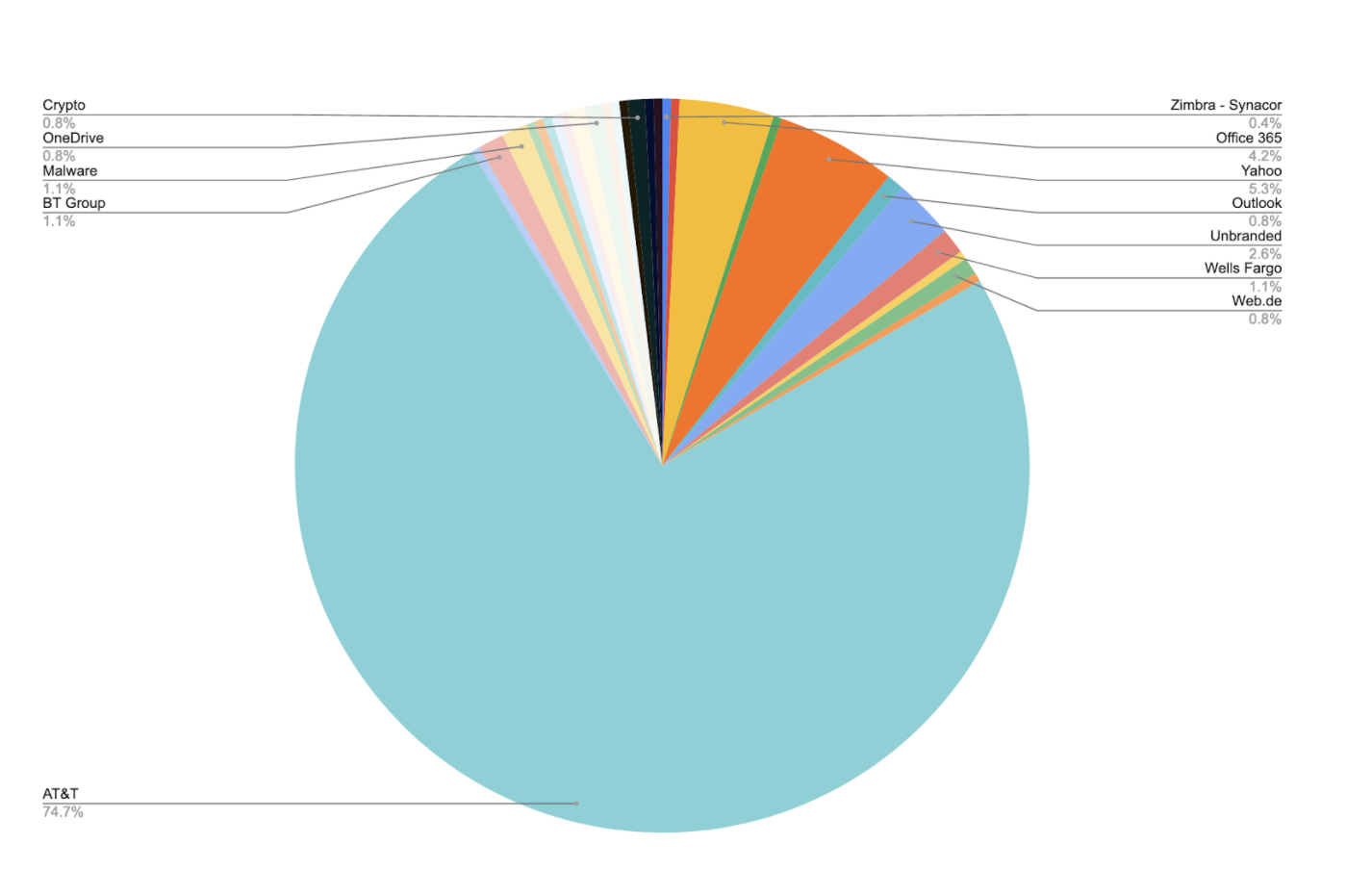
Nearly 75% used AT&T or AT&T and Yahoo logos
Scammers – masquerading as more than 25 different companies, brands and government agencies – used 265 Google Forms in an effort to steal user passwords and credentials.
According to our findings, the links remained active for several months after being added to public phishing databases. All of the Google Forms were removed by Google after we reported it to them.
In this blog we will:
- Identify the companies used in the phishing attacks and provide select attack examples;
- Compare a phishing form with a legitimate one; and
- Explain why Google Forms were used.
Targeted companies
In our analysis, more than 70 percent of the sites targeted AT&T (or Yahoo and AT&T together). The full list of targeted companies, brands and government agencies – listed alphabetically – included:
- AOL (America Online)
- AT&T
- Binance
- BT Group (British Telecommunications)
- Capital One
- Citibank
- European Union – Foreign Direct Investments
- GESupplier.com
- Google Docs
- IRS (Internal Revenue Service)
- Mexican Government
- Microsoft OneDrive
- Microsoft Outlook
- Oca Card
- OneDrive
- Office 365
- Pôle emploi
- SBC
- Sir
- Sky – TATA
- Swisscom
- T-Mobile
- Trust Wallet
- Web.de
- Wells Fargo
- Yahoo
- Zimbra
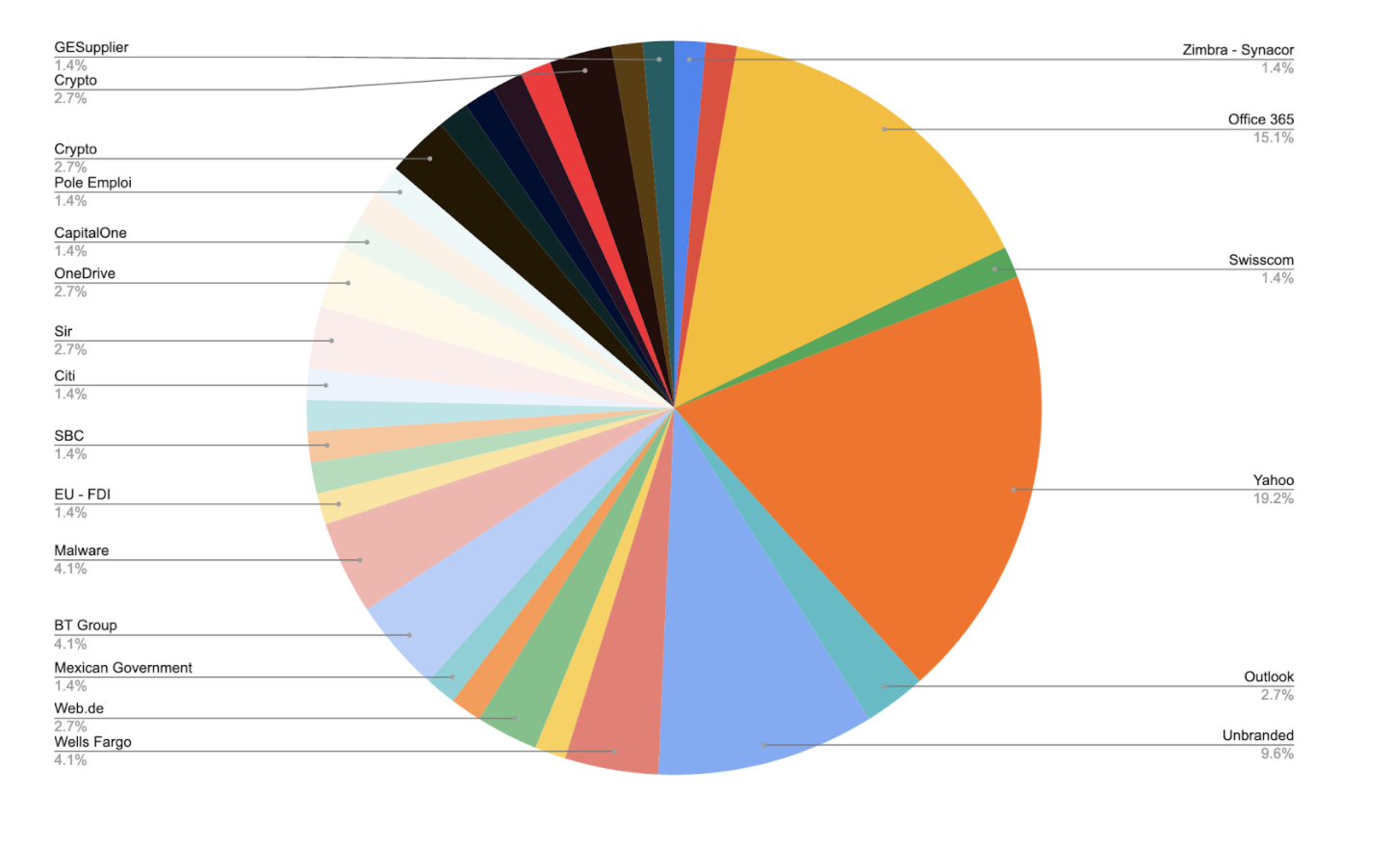
The pie chart below shows the Google Form percentages. “Unbranded” consists of the remaining companies/brands not listed in the pie chart; “Malware” are Forms where the scammer was trying to have the user download a malicious app. These Forms weren’t branded. To ease the visualization, the same chart is provided removing AT&T from it.
Whether a company’s logo or brand was used once or several times on different Google Forms, the phishing dangers were very real.
Google Form phishing
Google Forms is a survey administration app included in the Google Docs Office Suite and Classroom along with Docs, Sheets, and Slides.
From a phishing perspective, Google Forms are quite desirable to use – – they are very easy to produce, and have the advantage that they are hosted under Google domain.
Unfortunately, creating a Google Form for phishing has several other advantages:
- The hosting of the domain doesn’t have to be solved by the attacker;
- Being hosted under a Google domain avoids the detection of reputation based phishing detectors (after all, nothing better than hiding under the most recognizable domain on the web);
- Phishing detectors based on domain antiquity won’t work in this site; and
- Google Forms also provide a valid SSL certificate meaning user’s relying on the “secure” indication of the browsers are easily fooled at no cost.
- Google forms state automatically at the base of each form “never submit password via Google forms” but this is evidentially ignored by many victims.
In this instance, the following Google Form was designed to steal an AT&T user’s credentials:

Users may have seen the “secure” icon next to the URL (just showing that it is an encrypted https connection using a valid SSL certificate) and thought the website was legit. At the same time, the browser was very likely to have *.google.com domain whitelisted which wouldn’t trigger a deceptive site warning.
In addition, the final button always said “Submit” (instead of the typical Login), and the default completion or message on all fields was “Your answer” (instead of “your username” and “your password”).
Furthermore, this phishing attempt was very likely successful despite Google showing advice to “Never submit passwords through Google Forms” next to the “Submit” button.
This form wasn’t detected as phishing using most of the common industry techniques since it used a high-reputation domain, established several years ago and it used a valid SSL certíficate.
Let’s take a look at the legitimate AT&T login:
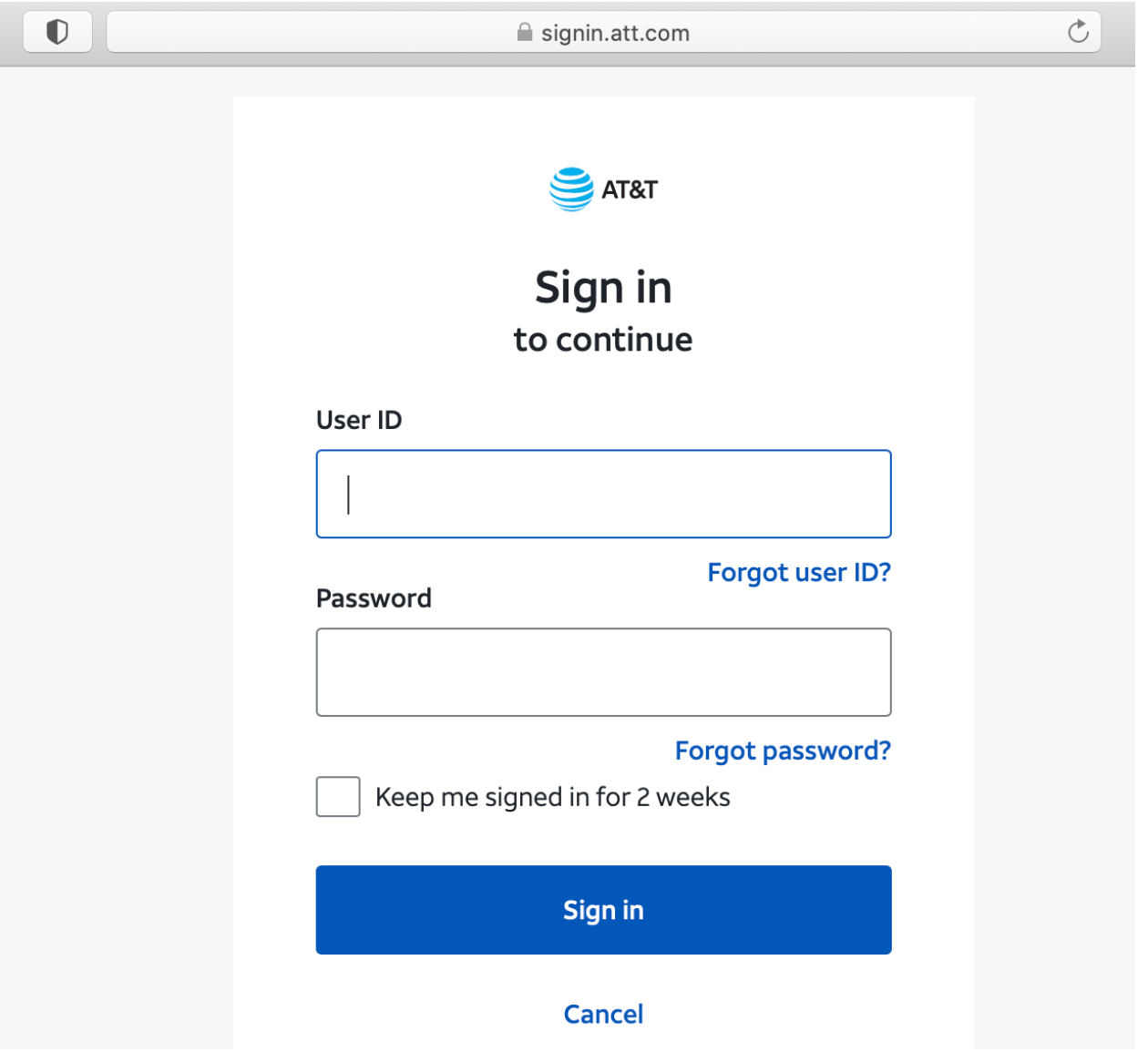
It’s “Sign in” instead of “Submit.” The logo and brand name matches the url domain. There are extra options like “Keep me signed,” “Forgot ID” and “Forgot password.”
There are several differences that will alert some experienced users, but lots of users will write their credentials on any form showing a company logo, unless the browser or a security tool warns them.
The following is another example of a phishing form with some extra fields:

An astute user may have noticed the password fields didn’t get hidden with the usual “****” and there was an unusual/confusing “Option 1” field.
Some automatic detection tools analyze forms or web pages for keywords like “email” “user” or “password,” in order to avoid detection, these forms used images to replace the sensitive text.
Additional examples
Unfortunately, as we reported, these were not the only examples of these phishing Google Forms.
The following form was trying to get Office 365 credentials:
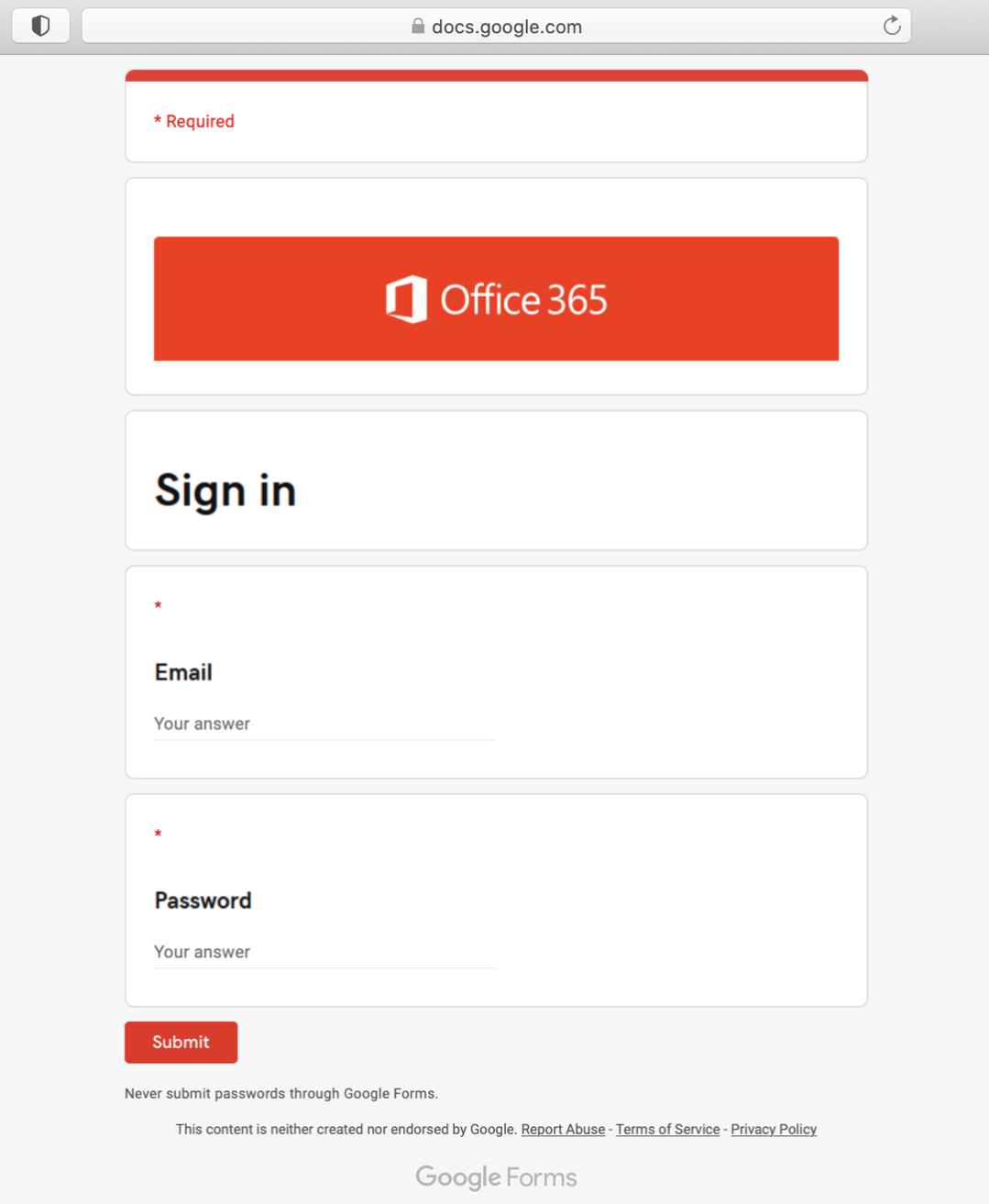
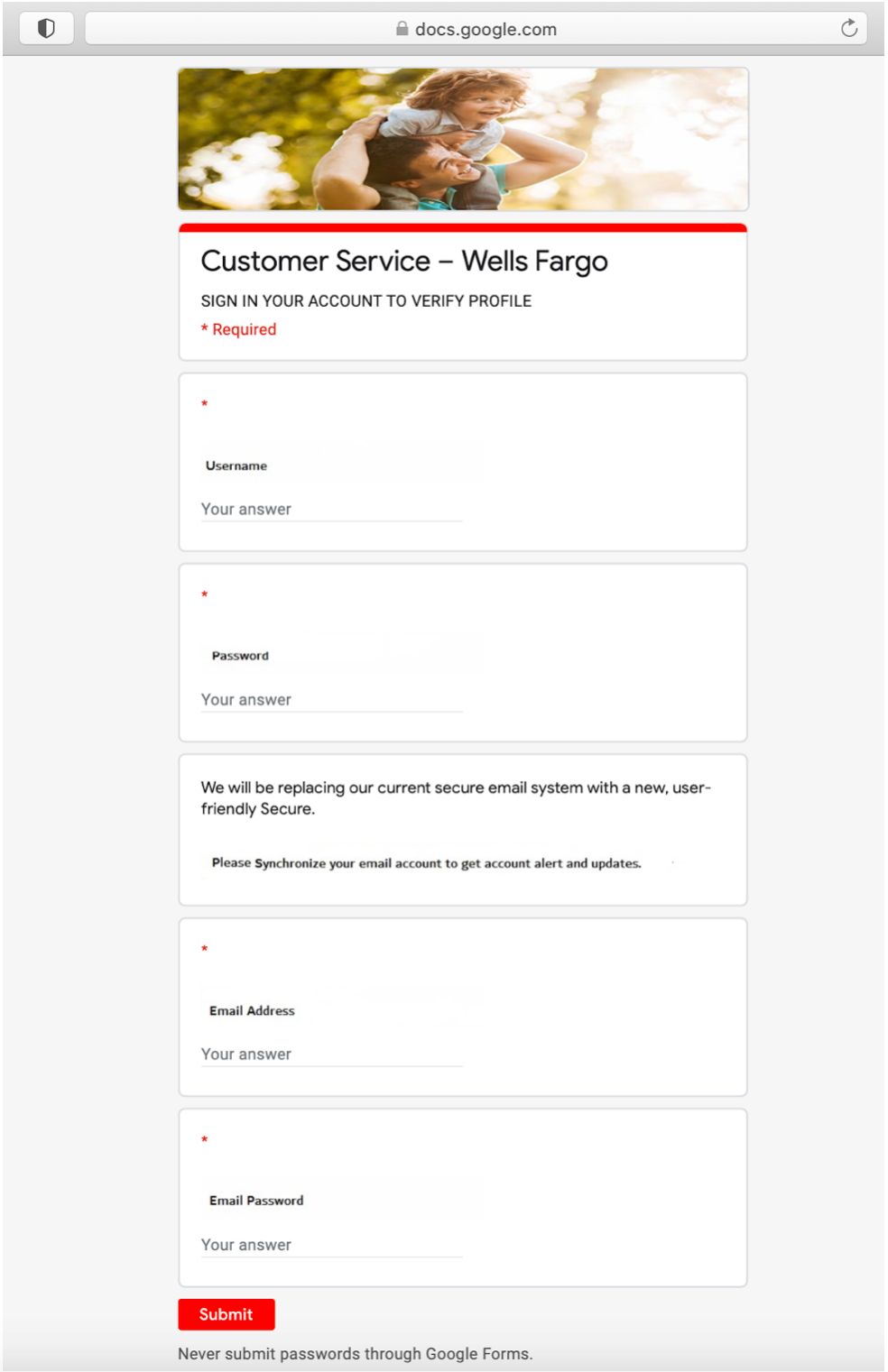
Here, they were trying to get Wells Fargo banking credentials:
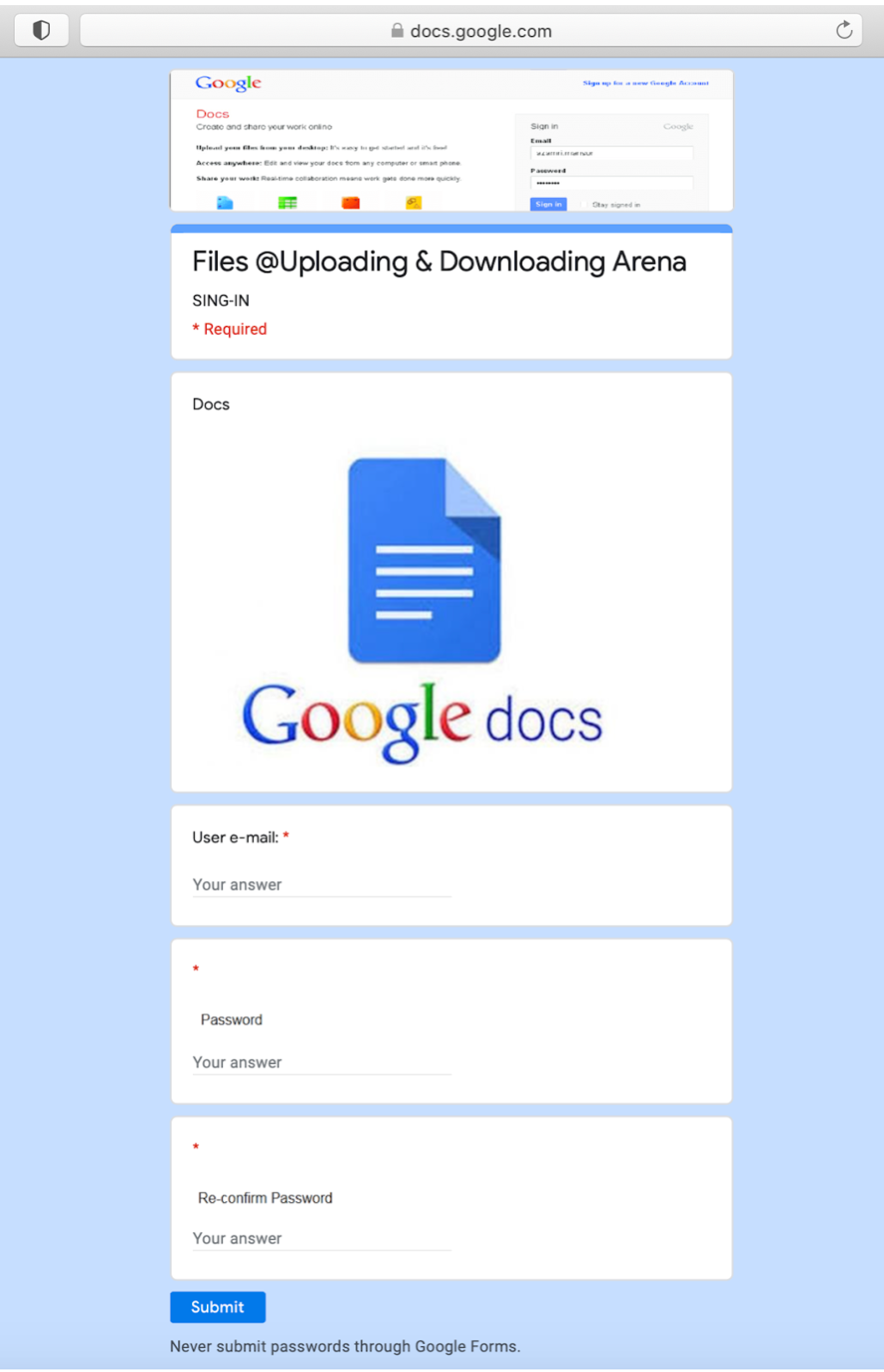
Attackers even created a form trying to get a user’s Google Doc credentials:
Phishing is on the rise
According to our research, the amount of phishing websites using HTTPS traffic raised from 12 percent in early 2019 to almost 60 percent today, with new phishing techniques appearing quite often.
This growing complexity has a direct impact on the difficulty to detect the phishing sites and forces detection engines to adapt fast in order to keep up to industry standards. For a quick dive on the phishing world, we recommend reading this blog post.
Many phishing kits are widely available online and can produce an exact copy of the legitimate page.
GigaOm Names Zimperium as a Leader in Anti-Phishing
We rank as an outperforming leader in GigaOm’s 2020 Radar for Phishing Prevention and Detection. According to the GigaOm Radar, Zimperium – the only major mobile threat defense (MTD) solution to be a part of the report – “is the leader in this space.” This is the second consecutive year Zimperium has been the sole MTD provider in GigOm’s coverage of anti-phishing market leaders.
Referring to Zimperium, GigaOm states, “Its holistic approach to detection of phishing attacks targeted at users’ mobile devices allows it to block phishing attacks that use text, social media, and personal and corporate email as vectors. It can do this while ensuring user privacy.”
If you’d like to talk to us directly to learn how to secure your mobile devices from phishing and other attacks, please contact us. We are here to help.


