Triada is now the “umbrella” name for the three mobile Trojan families – Ztorg, Gorpo and Leech – that, as we mentioned before, primarily exploit users of Android 4.4.4 and earlier versions of the mobile OS. In this blog post, the zLabs team presents specifically the findings from our testing of Leech, which like the others in the trilogy, gains root privileges to take over a device and exploits the Zygote system process to inject itself into other system processes. Zimperium customers are safe without performing any updates. Our z9 engine, generated 23 different alerts when we tested Trojan Leech in our labs. In fact, we have first observed detected attacks from this exact malware on 5/2/2015. Read on to learn more and see just how our zIPS with its z9 engine protects against this Trojan.

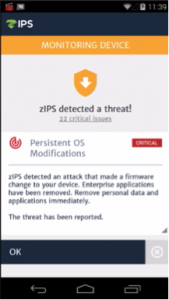 After gaining root privileges on the device, Leech will install the following malicious apps to /system/priv-app/ folder.
After gaining root privileges on the device, Leech will install the following malicious apps to /system/priv-app/ folder.
- SmsManager.apk – Trojan [VT]
Namespace: com.sms.sys.manager, com.aqplay.sdk - ConfigNService.apk – Rootnik Android Trojan [VT]
Namespace: com.bk.config.service
We see a large amount of rooting malware every day and consider the rooting capability as a basic capability for malware. Since we detected this threat we can also share the Indicators of Compromise (IOCs) and actions performed by the attackers in the past.
We have observed attacks under the namespace of com.as.ytb.downloader in the following countries:
- US
- Yemen
- Turkey
- West bank
- Germany
IOCs:
As part of the payload, the malware modified the recovery script:
- File Path: /system/etc/install-recovery.sh
- File Hash: 6ae1dbc9e7674d7dbbf125f606b3f7dbd11f8718bfd0d7e0861ffa5afc42b20d
The malware creates the following files:
| Path | Hash |
| /system/bin/debuggerdd | 0746c3ed1598947566e92b5e258ee955b559f86f661e7a70aaa56a0ecb9792ad |
| /system/xbin/sp | 49f97664b28c15cc244a5d55122f7bb10d246ff851f86fbfeba1bf525da433b9 |
| /system/bin/ndcfg | cb13d25e921941706eb29f7ec2db1bbc74beb5a6a688f6aa53b2d7bfff1f34a5 |

Communication by the malware as an app:
- 67.252.10:80 – Akamai Technologies in Cambridge, Massachusetts, United States.
- 7.41.34:80 – Akamai Technologies in Cambridge, Massachusetts, United States.
- 251.212.218:80 – SG.GS in Singapore.
- 20.83.120:80 – CloudFlare in San Francisco, California, United States.
- 28.24.144:80 – CloudFlare in San Francisco, California, United States.
- 6.165.90:80 – Amazon Technologies in Ashburn, Virginia, United States.
- 2.159.222:80 – Amazon Technologies in Ashburn, Virginia, United States.
- 108.185.113:80 – Lg Dacom Kidc in Seoul, Seoul-t’ukpyolsi, Korea, Republic of.
Contacted the following IPs after obtaining root permissions:
- 105.254.228:80 – Search Guide in Boulder, Colorado, United States.
- 21.91.8:80 – EdgeCast Networks in Santa Monica, California, United States.
- 21.92.20:80 – EdgeCast Networks in Santa Monica, California, United States.
- 205.159.56:80 – Zhejiang Taobao Network Co.,Ltd in Hangzhou, Zhejiang, China.
- 187.73.202:7012 – Amazon Technologies in Boardman, Oregon, United States.
Known Hashes:
a1cdc9736e93bd1db572a5969be0117e4921de99
9985f3362013e31dff1a0dac638b802c4a01fdde
478e5ac7df97b458dd1ed57e0dd093f07aa5d35b
03b2f4efd534d69321746ad0851e4fbe7b8e1db1
4c675b8196fb7e921f7e27646a2fedc83bbde702
006b23bcdd39ffb7b98ef3af1eeb939f11f02393
df4df5c9009753776ff7b3d53f208f9cc11ad1c2
ed7af94974777145329da8e6251437e2ec29f8ab
48b801668aaeced40e183e94b15375a5c5ec8ec9
f3d503acc9e3db9b942f3238cae1eaa085407ef6
9ceba8c4e874bb668ca31491ddcf632f38b23b47
30c9b50f6331de621c8f0e5c884d5dab4b13396b
a31d8d67b49cdf4c44a7f301a931849744c0c96b
30d110bb04932ac5e92b3d56033ac81933b5a208
cc2dc2ead2a8cf384bcf8ac66e31586ca76ee8a9
a1d0dbe601b611a7206f82574fcd72e5ab57f09c
317ce52713f99f3c7a4f38c3a98a02690cce6de7
04e04eae2bd4a29e1a08c38545aef80394f62493
6aba69f858ed360c818bcbe105db01f970d1e6aa
acb292bb3cc0b6095a06dae30d3ff033a3863cfc
82d32c1c8cc1eb08d30326279281f5317bd7b058
f7484ba764d73943f27e8afdf1fc48b09b65caa5
7a2fc3782d179d37a01e4c609ea2be4cb915eebf
8deee992b7c28eec0c414c707724ec2f57d7e168
706aab1479ac2088ea200b988dba61a7e0c38d36
606624c6e7c4627ffc75dbd756ac495ea3b53f69
ed645df93c688885e7a7b01c56d643ad9553b75e
1940de90a38e4f9b06a510ded0472f8829736aff
5b1207d4eb9dd216ed62762a9e8301173b8ccee2
85e9a11e3d04c3c9fd89b55282f2f428643d9bd7
b5a06369e6cf26a947af25790aea053ef1eb398d
9cedd1cdb1a239a7f1c3eda14aa7c4ae3a7022be
c5ba0dd5f7d483ba27ed49f0e9b622622d13a8d4
00be651d94bde3b113569e93ec41dff79749ae82
3a291646b2d21548619b84333beb6f22f8ba5a8d
d7e734be9ea143c41dae3fbf9388a625d6ba8d5d
65bfc482d6c7fbf3b9681af12e25880dfa71785b
34e1e6ec24b92ce374396a5e339c13e47064224a
d9da4f1ed7cd78863b9867d4efbebc22e28e45b5
7a57aa9ee54cc442004a5d6874f623e115552467
4aa1d2cb87352bb96e8cf53c86d5ae40fc7dc1a2
78d311a4a160f3831f978e51b61c5f2d8c165faf
350405545ded0697a3b12e4d9281297005ae9718
6bafdbe578daecd057aa14f11416f717bc4daacc
c9764fd47c1b271945b634a258e1bacac3304f35
4ac1756a4af888bb23f1f0aaec4db9578b159d71
a1cdc9736e93bd1db572a5969be0117e4921de99
af62d2328819267d0207b266bc1cdc3db73fc588
cceee71d75d151fd44d62c25ace07ec9fe8f4647
ff721627e493beaf53371f6eae567725d5a6e6b7
bbb91acd3454be1dc60692a5b7af679467530091
6c0fc552d0fc54c5cb7070e422dfab6537a2956f
a3eaea4926d8088faf4ebcdf8df89594c903e730
ebe809ac123453292b50c75f20d9857caf069aaa
21f06113a03dd7c911adcf902d933a4571052213
e88a5145d6d024e14a5050c1ac93ebc5d400dd17
54ed99f6af6bc246483b235156df28018fd05bc7
12f30c84471ebf8f25a7734932e1144c75888f6f
02d2be28d734f58a30cbebf2c324399279276569
1fbe9ff02b253c9088c70a3b431d7f4559e8d650
410de31222d82b43802cdbc759117696122475b9
cd4439d0c4d98eb2ec2d456173fe4469047a6b08
7f56508595589b74fdea9c277886862aa999ca36
6c3063a6ac9a664c9a52ed39f4c9d8a7d4d89a4b
74c5d21df8ed295f5d87f0707a3f28ad81872c4e
d39a2f010f687c489e886432e6113bd84e96b8a6
6348a1ccdbd541e3e89b4a16d0552189ab7f710d
21feef4ae9e6d6edc2223646aa1137b07e69baf5
3c348b3b2415d37db880bfa5a80567301ab3ea2a
9616f779add04e8c0ef502e19f5c21cf94aa76ff
3fac99faf5039b669710135ae8755e001c7d221d
89bfbdc527a6d070219eb276b8ca1828dd6053eb
417d97d1e2117b3486cd3a8d7498dc1e9b9e5a23


