Executive Summary
Since April 2024, zLabs has identified a growing trend of Android applications misusing NFC and Host Card Emulation (HCE) to illegally obtain payment data and conduct fraudulent transactions. What began as just a few isolated samples has now expanded to more than 760 malicious apps observed in the wild—demonstrating that NFC relay abuse is not slowing down but continuing to accelerate.
Campaigns previously documented by other vendors are now broadening their reach to additional regions, including Russia, Poland, the Czech Republic, Slovakia, and others.

Figure 1: List of entities that were impersonated by these apps
Monitoring of these campaigns from April 2024 has revealed the following key findings:
- Over 70 command-and-control (C2) servers and distribution sources have been identified.
- Dozens of Telegram bots and private channels are being used by operators for exfiltration and coordination.
- Approximately 20 institutions have been impersonated - primarily Russian banks and financial services, but also targets organizations in Brazil, Poland, Czech Republic, and Slovakia (Fig. 1).
- Hundreds of malicious samples have been detected over the period of time (Fig. 2).
- Multiple variants were observed exploiting NFC functionality while disguising themselves under different brand names.
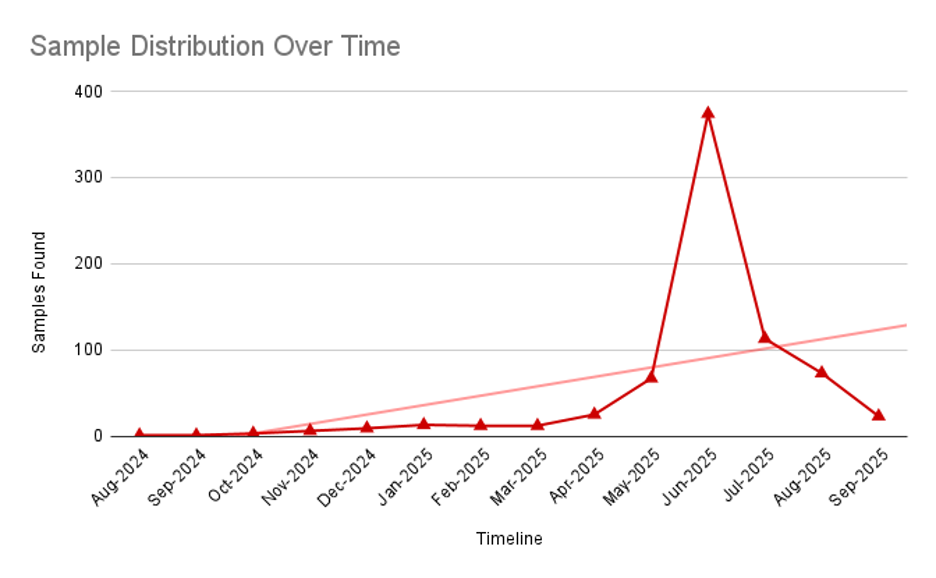
Figure 2: Graph showing the found samples over the period of time
Who They Pretend To Be: Impersonating Trusted Institutions
To deceive users, these applications masquerade as legitimate services from financial institutions, payment processors, and government agencies. The following entities have been observed as the primary targets.
|
App / Service |
Category |
Country of Origin |
|
Central Bank of Russia |
Government / Regulator impersonation |
Russia |
|
Gosuslugi (State Services Portal) |
Government Services |
Russia |
|
Santander Bank |
Banking / Finance |
Spain (multinational) |
|
Kuban Credit Bank |
Banking / Finance |
Russia |
|
Rosfinmonitoring (Federal Financial Monitoring Service) |
Government / Financial Regulator |
Russia |
|
VTB Bank |
Banking / Finance |
Russia |
|
Promsvyazbank (PSB) |
Banking / Finance |
Russia |
|
Tinkoff Bank |
Banking / Finance |
Russia |
|
National Bank of the Republic of Belarus (NBRB) |
Central Bank / Regulator impersonation |
Belarus |
|
PKO Bank Polski |
Banking / Finance |
Poland |
|
Československá obchodní banka (ČSOB) |
Banking / Finance |
Czech Republic |
|
National Bank of Slovakia (NBS) |
Central Bank / Regulator impersonation |
Slovakia |
|
Bradesco Bank |
Banking / Finance |
Brazil |
|
Itaú Bank |
Banking / Finance |
Brazil |
|
Google Pay |
Mobile Wallet / Payments |
USA |
|
ING Bank |
Banking / Finance |
Netherlands (global) |
In the Crosshairs: ‘Mamont’ Is Cybercriminal Slang for Victim
While the discovered samples share similar objectives, their operational methods vary significantly. Some applications operate as scanner/tapper tools, seemingly offered by threat actors to third parties. In such cases, one app extracts data from a card, while another utilizes a Point of Sale (POS) system to complete a purchase.
Other samples, however, are designed solely to collect card data and exfiltrate it to a designated Telegram channel. In these cases, threat actors receive automated messages for each connected device, containing details such as device IDs, card numbers, expiration dates, and other EMV (Europay, Mastercard and Visa) fields. The messages are then posted into private Telegram channels as shown in Fig. 3:
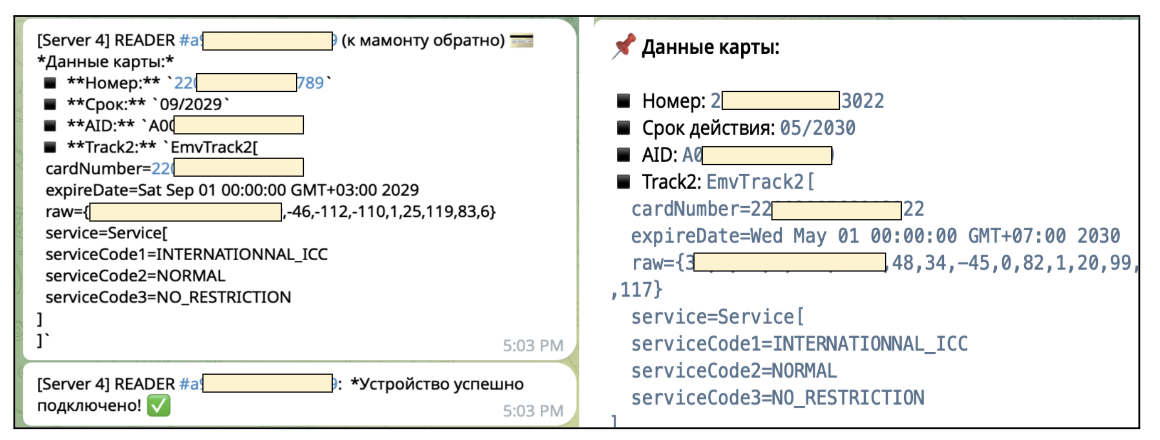
Figure 3: Data received on the threat actor’s private channel
The applications are designed to require minimal user interaction, typically displaying a simple full-screen "bank" page - sometimes within a WebView. They prompt the user to set the app as the default NFC payment method, while background services silently handle NFC events (Figure 4).
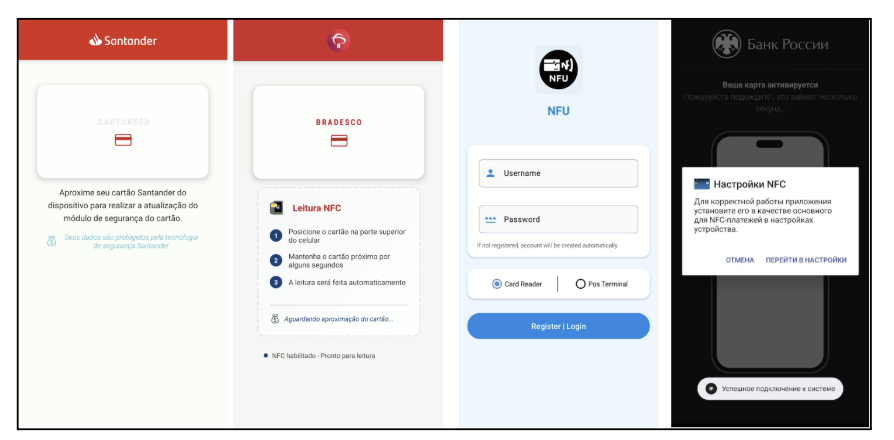
Figure 4: The app layout presented by variants of NFC malwares
The following table presents the key commands exchanged between C2 (Command & Control servers) and the malicious apps.
|
Command |
Description |
Flow |
|
login |
The app asks the server to sign in (sends credentials). |
App to Server |
|
login_response |
Server replies to the app’s login request. |
Server to App |
|
register / register_device |
The app provides device details (HWID, model, NFC support, IP). |
App to Server |
|
register_response |
Server confirms device registration. |
Server to App |
|
logout |
The app tells the server it is logging out. |
App to Server |
|
apdu_command |
App forwards a payment terminal’s request (APDU) to the server. |
App to Server |
|
apdu_response |
Server returns the crafted APDU reply (attacker’s answer to the terminal). |
Server to App |
|
card_info |
The server instructs the app to show card info or PIN screen. |
Server to App |
|
card_removed |
Server signals the card/emulation session has ended. |
Server to App |
|
clear_card_info |
Server tells the app to clear/refresh card info display. |
Server to App |
|
get_pin |
The app requests a PIN value from the server. |
App to Server |
|
pin_response |
Server provides a PIN value (app may display + forward it). |
Server to App |
|
ping |
Either side sends this to check if the other is alive. |
Both |
|
pong |
Reply to a ping, confirming connectivity and status. |
Both |
|
check_status |
The app asks if the device is blocked/allowed. |
App to Server |
|
status_response |
Server replies with current device status (e.g., blocked, maintenance). |
Server to App |
|
paired |
Server confirms this device was paired with another endpoint. |
Server to App |
|
unpaired |
Server tells that the app pairing was removed. |
Server to App |
|
update_required |
Server instructs the app to prompt user to download/install update. |
Server to App |
|
telegram_notification |
The app sends a message intended for the attacker's Telegram bot. |
App to Server |
|
telegram_response |
Server replies to confirm Telegram-related action. |
Server to App |
|
error |
Server signals a problem (e.g., bad token, login failed). |
Server to App |
Conclusion
With the rapid growth of “Tap-to-Pay” transactions, NFC has become an increasingly attractive target for cybercriminals. These malicious applications exploit Android's NFC permission to steal payment data directly from victims’ devices—illustrating why this attack technique has gained significant traction in recent months.
The data tells a clear story: NFC is being abused at scale. With over 760 apps, dozens of C2s, and multiple Telegram channels, this is no longer isolated activity. Different actors are reusing the same concept and tailoring it to local banks and services.
Financial institutions, mobile vendors, and users should treat any unknown or unfamiliar application requesting NFC payment privileges as high risk.
Zimperium vs NFC Relay Malware
The surge in NFC relay malware campaigns underscores how quickly threat actors are evolving to monetize Tap-to-Pay systems. Unlike traditional banking trojans that rely on overlays or SMS interception, these malicious applications exploit Android’s Host Card Emulation (HCE) capabilities to impersonate legitimate payment apps and relay sensitive transaction data in real time. The result is a new threat class that combines financial fraud with device-level abuse of NFC functionality—something traditional defenses often overlook.
Zimperium’s Mobile Threat Defense (MTD) and Mobile Runtime Protection (zDefend) deliver zero-day, on-device detection coverage against all known NFC relay malware samples observed in the wild. Our dynamic detection engine identifies malicious behaviors and permission abuse patterns from the moment of installation—without relying on cloud lookups. This ensures protection even as attackers continuously rebrand and repack the same codebase to impersonate different financial institutions across regions.
As the number of malicious apps abusing NFC continues to grow, organizations must recognize this is not a niche phenomenon but a scalable, global fraud technique. Zimperium remains committed to protecting mobile users against this emerging threat, providing resilient, on-device defense against both current and future iterations of NFC relay abuse.
MITRE ATT&CK Techniques
Indicators of Compromise
The IOCs for this campaign can be found in this repository.


