Executive Summary
Mobile infostealers have rapidly evolved into a critical threat vector for both individuals and enterprises. These malicious apps are designed to harvest credentials, intercept communications, and exfiltrate sensitive data—often without detection. As businesses become increasingly dependent on mobile, cybercriminals have adopted a mobile-first attack strategy to exploit inattentive users and their often unprotected mobile devices.
This report highlights five active mobile infostealer families detected in the wild by Zimperium’s detection engine: TriaStealer, TrickMo, AppLite, Triada, and SMS Stealer. These malware strains target financial services, communications platforms, and authentication mechanisms, with tactics ranging from overlay attacks that mimic the user’s screen to pre-installed firmware backdoors.
Key findings include:
- Over 2,400 variants detected, with 69 countries impacted
- Zero-day detection of three malware families was made before any public IOC’s were released
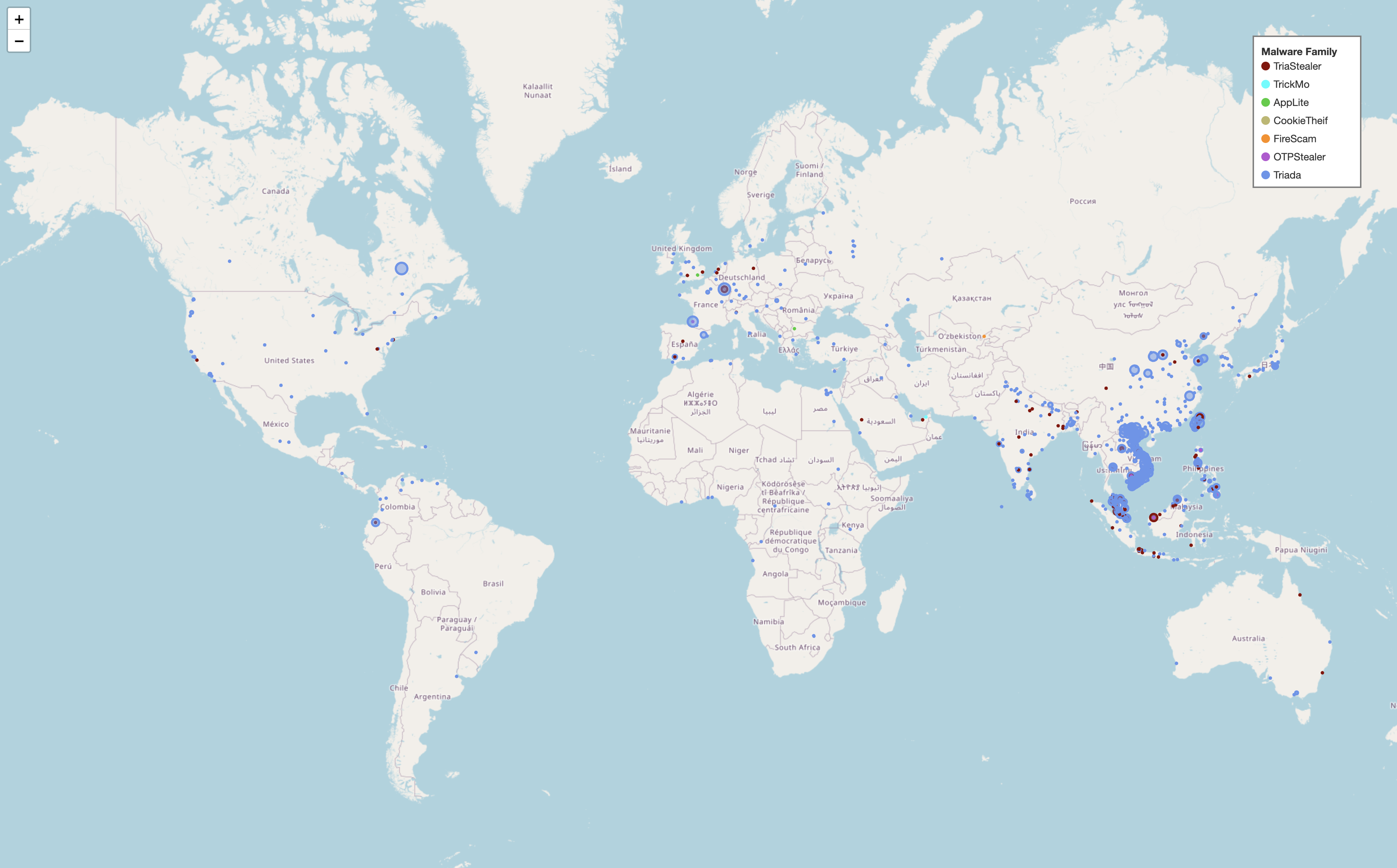
- Southeast Asia identified as a major hotspot for infections
- Most impacted industries: finance, retail, and software
Zimperium's on-device, dynamic detection engine, leveraging advanced AI capabilities, enabled proactive detection of these previously unknown threats, even in the absence of public IOCs. This underscores the critical importance of real-time, behavioral-based mobile threat defense.
What are Infostealers?
Infostealers are malicious software designed to steal sensitive data from devices, such as login credentials (including one-time passwords & MFA codes), personal information, financial details, and communication content. Once exfiltrated, this highly personal data is immediately weaponized. It's either directly leveraged for targeted phishing, blackmail, and account takeovers, or sold on underground forums, serving as the foundational vector for more impactful and sophisticated intrusions driven by stolen credentials.
With an increase in the use of stolen credentials in 10% of cyber attacks in 2023 to 16% in 2024 they represent a significant risk in today's threat-landscape. Despite 82% of organizations leveraging mobile platforms in the workplace, these devices are highly vulnerable to cyberattacks due to the significantly lower deployment of security tools compared to traditional desktop and laptop endpoints.
Numerous malware families of this kind exist. In this blog post, we highlight five prominent mobile infostealer malware variants that our zLabs team identified in the wild. Thanks to our advanced on-device malware detection capabilities, Zimperium MTD users were protected against each of these attacks, but critically we were able to proactively detect three of these as malicious in a zero-day fashion - before they became public knowledge or their Indicators of Compromise (IOCs) were widely released. Furthermore, our analysis detected many more related samples not reported in the original IOCs, underscoring the breadth and sophistication of these malware campaigns.
TriaStealer: Account Hijacking and Impersonation
TriaStealer (first discovered by Kaspersky) emerged as a formidable Android threat, built for account hijacking, victim impersonation, and unauthorized money transfers. This infostealer targets a broad spectrum of communication and email platforms, encompassing popular services like WhatsApp, WhatsApp Business, Google Messages, Samsung Messages, MMS, Gmail, Outlook, and Yahoo Mail. TriaStealer is engineered to pilfer sensitive data, including text messages, email content, application notifications, and crucial one-time passwords (OTPs), effectively compromising a user's digital life. Initially observed targeting users in Malaysia and Brunei, it exfiltrates stolen information to Telegram bots, demonstrating a sophisticated exfiltration method.
Its primary objective is to seize control of personal messaging accounts, enabling attackers to impersonate owners for illicit money transfer requests. It also aims to bypass critical security measures by intercepting Transaction Authorization Codes (TACs) and One-Time Passwords (OTPs). This is achieved through a trove of requested permissions, including the ability to read SMS, access network states, and intercept notifications, painting a stark picture of its intrusive capabilities.
TrickMo: Evolution from Banking Trojan to Full-Scale Infostealer
TrickMo has dramatically evolved from a mere banking trojan into a highly sophisticated tool for extensive victim data leakage. Initially discovered by Cleafy, Zimperium zLabs subsequently disclosed additional indicators of compromise after its own research.
Initially observed to heavily target users in Canada, the United Arab Emirates, Turkey, and Germany, TrickMo's reach extends to target popular services such as Google, Yahoo, Zoho, Dropbox, Adobe, Zendesk, and Zoom. This advanced malware now incorporates innovative techniques to evade detection and analysis, utilizing methods like zip file manipulation and obfuscation.
Beyond its credential theft, TrickMo boasts a formidable arsenal of capabilities to achieve its goals, including OTP interception, screen recording, robust data exfiltration, and even remote control over infected devices. It leverages Accessibility Service abuse and automatic permission granting to seamlessly integrate into the device. Furthermore, TrickMo can steal device unlock patterns or PINs by presenting a deceptive UI that mimics the actual unlock screen. Collectively, these tactics enable TrickMo to compromise not only banking information but also sensitive credentials for corporate resources like VPNs and cloud services, marking it as a significant and persistent threat in the Android ecosystem, particularly for Enterprises.
AppLite: Targeting Mobile Employee Devices
AppLite, a pernicious new variant of the AntiDot banking trojan, was discovered by Zimperium. This sophisticated threat is specifically engineered to compromise mobile employee devices and distributed via highly deceptive Mishing (mobile-targeted phishing) campaigns. It frequently masquerads as legitimate applications like Chrome and TikTok to ensnare unsuspecting users.
Once entrenched, AppLite sets its sights on a wide array of financial and communication applications. Its targets include, but are not limited to, Venmo, Cash App, Wise, Google Wallet, Gmail Go, Payoneer, Neteller - Fast Payments, PayPal, and 14 other financial services.
To achieve its credential-stealing objective, AppLite employs a suite of insidious tactics: it can deploy a deceptive overlay mimicking the device's lock screen to capture entered credentials, or present a fake AlertDialog prompting a supposed update and a subsequent login. Furthermore, this malware is capable of injecting malicious JavaScript directly into HTML pages, allowing it to intercept and exfiltrate a victim's login credentials seamlessly, posing a significant threat to corporate and personal financial security.
Triada: Pre-installed Firmware Threat
Triada, initially discovered by Kaspersky, is a highly deceptive infostealer that can come pre-installed within some device firmwares, making it a threat from the moment a device is acquired. This multi-stage Trojan backdoor grants attackers virtually unlimited control over a victim's device. Its stealthy operation begins by infecting the crucial Zygote process, effectively compromising every application running on the system.
With a highly modular architecture, Triada can tailor its malicious functionality to target specific applications with alarming precision. It actively steals authentication tokens and cookies, manipulates clipboard data—especially targeting cryptocurrency wallet addresses during transfers and within QR codes—and intercepts or modifies messages. Its extensive list of targets includes popular platforms like Telegram, WhatsApp, Instagram, TikTok, SMS apps, Chrome, Edge Browser, and Opera Browser, alongside at least 11 other applications. Beyond merely stealing credentials, Triada can replace links in browsers, send arbitrary text messages, intercept replies, and modify cryptocurrency wallet addresses, demonstrating its comprehensive ability to subvert user control and financial transactions.
SMS Stealer: Deceptive Apps and OTP Theft
The SMS Stealer, discovered by Zimperium, represents a pervasive Android-targeted malware singularly focused on obtaining One-Time Passwords (OTP’s) delivered via SMS messages. This malicious software typically infiltrates user devices when individuals are tricked into sideloading deceptive applications, often propagated through misleading advertisements or malicious Telegram bots.
Upon successful installation, the SMS Stealer immediately requests essential SMS message read permissions, then establishes a discreet connection to a Command and Control (C&C) server to register its presence. From that point forward, it silently monitors all incoming SMS messages, meticulously extracting OTPs as they arrive. This threat specifically targets a vast array of services, including prominent platforms like Google, Gmail, Microsoft, ProtonMail, and Skype, alongside over 60 global brands. By harvesting these OTPs, the SMS Stealer aims to bypass the critical added protection they provide, thereby enabling malicious actors to infiltrate corporate networks and sensitive data.
Global Impact and Detections
Zimperium detected over 2400 variants of Infostealers across these five families in the wild. While some align with original Indicators of Compromise (IOC’s), Zimperium’s zLabs team later discovered several new variants through its extensive research of these families, as shown in the table below.
|
Family |
IOC detections |
New variants |
|
TriaStealer |
6 |
1735 |
|
TrickMo |
4 |
2 |
|
AppLite |
2 |
2 |
|
Triada |
0 |
580 |
|
SMS stealer |
0 |
133 |
Infostealers from these families have been detected across 69 different countries globally. However, a review of the detection map below clearly indicates that Southeast Asia is a significant hotspot for these threats.
Industry Impact
While detections span multiple sectors, the retail, finance, and software industries remain the most heavily targeted. This trend reflects attackers' clear focus on compromising credentials, digital wallets, and transaction systems.
The following chart shows the distribution of detections based on the targeted industry.
Zero-day Detections
Three of the five malware families in this report were detected by Zimperium before their IOCs were publicly disclosed. This early detection was made possible through our on-device dynamic detection engine, which analyzes behavior in real time without requiring continuous cloud connectivity.
|
1st Zimperium detection |
Blog post |
|
|
Triastealer |
August 2024 |
|
|
Trickmo |
May 2024 |
|
|
Applite |
October 2024 |
Be Prepared
Infostealers are no longer solely targeting desktops—they are now deeply embedded in the mobile ecosystem, propagating via sideloaded applications, sophisticated phishing links, and even device firmware. While best practices such as avoiding untrusted apps and suspicious links are helpful, they are no longer sufficient.
To adequately secure their workforce and the sensitive data residing on mobile devices, organizations require:
- Real-time, on-device mobile threat detection that identifies and neutralizes threats directly on the endpoint, ensuring continuous protection even when devices are offline and providing immediate response capabilities against evolving attacks.
- AI powered Zero-day detection that proactively identifies previously unknown threats and novel attack techniques without relying on signatures or prior Indicators of Compromise (IOCs), offering unparalleled protection against emerging threats.
- Comprehensive visibility into app behavior at scale to continuously monitor and assess the security and privacy risks of all applications across the mobile fleet, enabling organizations to enforce policies, identify risky behaviors, and maintain a secure app ecosystem.
Zimperium’s Mobile Threat Detection (MTD) and Mobile Runtime Protection (zDefend) enable exactly that—detecting and stopping infostealers before they can exfiltrate sensitive data or compromise enterprise resources.
Learn More
For a deeper technical dive into each of these malware families,, we encourage you to explore our original blog posts. These dedicated posts provide detailed insights, comprehensive indicators of compromise (IOCs), and insights into detection techniques.
Indicators of Compromise (IOCs)
The newly discovered IOCs can be found in the following repository.